Documenti di Didattica
Documenti di Professioni
Documenti di Cultura
EIT - Ethics For IT Professionals
Caricato da
John 존앨빈 DelosSantosTitolo originale
Copyright
Formati disponibili
Condividi questo documento
Condividi o incorpora il documento
Hai trovato utile questo documento?
Questo contenuto è inappropriato?
Segnala questo documentoCopyright:
Formati disponibili
EIT - Ethics For IT Professionals
Caricato da
John 존앨빈 DelosSantosCopyright:
Formati disponibili
Chapter 4 Privacy
Ethics in Information Technology,
Second Edition
Updates by Carlotta Eaton, NRCC
1. What is Right of Privacy?
2. Las for electronic s!rveillance
". #orms of data encry$tion
%. What is identify theft?
&. Strategies for cons!mer $rofiling
'. Treat c!stomer data res$onsi(ly
). Why and ho or* $lace monitoring
+. What is s$amming?
,. -a$a(ilities . ethical iss!es of advanced
s!rveillance technologies
Ethics in Information Technology, Second Edition 2
Chapter 4 Privacy Objectives
Systems collect and store *ey data from every
interaction ith c!stomers
/any o(0ect to data collection $olicies of
government and (!siness
Privacy
1ey concern of Internet !sers
To$ reason hy non!sers still avoid the Internet
Reasona(le limits m!st (e set
2istorical $ers$ective on the right to $rivacy
#o!rth 3mendment 4 reasona(le e5$ectation of $rivacy
Ethics in Information Technology, Second Edition "
Privacy Protection and the Law
6efinition
7The right to (e left alone8the most com$rehensive of
rights, and the right most val!ed (y a free $eo$le9
7The right of individ!als to control the collection and !se
of information a(o!t themselves9
Legal as$ects
Protection from !nreasona(le intr!sion !$on one:s
isolation
Protection from a$$ro$riation of one:s name or li*eness
Ethics in Information Technology, Second Edition %
The Right of Privacy
Legal as$ects
Protection from !nreasona(le $!(licity given to one:s
$rivate life
Protection from $!(licity that !nreasona(ly $laces one in
a false light (efore the $!(lic
Ethics in Information Technology, Second Edition &
The Right of Privacy (continued)
Legislative acts $assed over the $ast %; years
/ost address invasion of $rivacy (y the government
<ot cor$orations
<o single, overarching national data $rivacy $olicy
-omm!nications 3ct of 1,"%
#reedom of Information 3ct =#>I3?
#air -redit Re$orting 3ct of 1,);
Privacy 3ct of 1,)%
-hildren:s >nline Protection 3ct =->P3?
E!ro$ean -omm!nity 6irective ,&@%'@E- of 1,,+
Aramm4Leach4Bliley 3ct
Ethics in Information Technology, Second Edition '
Recent History of Privacy Protection
>ther initiatives
BBB >nline and TRCSTe
Inde$endent, non$rofit initiatives
#avor an ind!stry4reg!lated a$$roach to data $rivacy
Ethics in Information Technology, Second Edition )
Recent History of Privacy Protection
(continued)
>$t4o!t $olicy
3ss!mes that cons!mers a$$rove of com$anies
collecting and storing their $ersonal information
ReD!ires cons!mers to actively o$t o!t
#avored (y data collectors
>$t4in $olicy
/!st o(tain s$ecific $ermission from cons!mers (efore
collecting any data
#avored (y cons!mers
Ethics in Information Technology, Second Edition +
Recent History of Privacy Protection
(continued)
Ethics in Information Technology, Second Edition ,
u!!ary of the "#$% O&C' Privacy
(uide)ines
Sec!re #light airline safety $rogram
-om$ares the names and information of 1.% million daily
C.S. airline $assengers ith data on *non or s!s$ected
terrorists
Eiolation of Privacy 3ct
Ethics in Information Technology, Second Edition 1;
Lega) Overview* The Privacy +ct
Aovernment electronic s!rveillance
6ata encry$tion
Identity theft
-!stomer $rofiling
<eed to treat c!stomer data res$onsi(ly
Wor*$lace monitoring
S$amming
3dvanced s!rveillance techniD!es
Ethics in Information Technology, Second Edition 11
,ey Privacy and +nony!ity -ssues
#ederal Wireta$ 3ct
>!tlines $rocesses to o(tain co!rt a!thoriFation for
s!rveillance of all *inds of electronic comm!nications
G!dge m!st iss!e a co!rt order (ased on $ro(a(le ca!se
3lmost never deny government reD!ests
7Roving ta$9 a!thority
6oes not name s$ecific tele$hone lines or e4mail acco!nts
3ll acco!nts are tied to a s$ecific $erson
Ethics in Information Technology, Second Edition 12
(overn!enta) &)ectronic urvei))ance
.
Ethics in Information Technology, Second Edition 1"
/u!ber of Tit)e --- 0iretaps (ranted
Electronic -omm!nications Privacy 3ct of 1,+'
=E-P3?
Sets standards for access to stored e4mail and other
electronic comm!nications and records
E5tends Title III:s $rohi(itions against the !na!thoriFed
interce$tion, disclos!re, or !se of a $erson:s oral or
electronic comm!nications
Prosec!tor does not have to 0!stify reD!ests
G!dges are reD!ired to a$$rove every reD!est
Ethics in Information Technology, Second Edition 1%
(overn!enta) &)ectronic urvei))ance
.
Electronic -omm!nications Privacy 3ct of 1,+'
=E-P3?
2ighly controversial
Es$ecially collection of com$!ter data sent over the Internet
#ailed to address emerging technologies
Ethics in Information Technology, Second Edition 1&
(overn!enta) &)ectronic urvei))ance
.
#oreign Intelligence S!rveillance 3ct of 1,)+
=#IS3?
3llos ireta$$ing of aliens and citiFens in the Cnited
States
Based on finding of $ro(a(le ca!se that a target is
/em(er of a foreign terrorist gro!$
3gent of a foreign $oer
E5ec!tive >rder 12"""
Legal a!thority for electronic s!rveillance o!tside the
Cnited States
Ethics in Information Technology, Second Edition 1'
(overn!enta) &)ectronic urvei))ance
.
-omm!nications 3ssistance for La Enforcement
3ct =-3LE3?
ReD!ires the telecomm!nications ind!stry to (!ild tools
into its $rod!cts so that federal investigators can
eavesdro$ on conversations
3fter getting co!rt a$$roval
-ontains a $rovision covering radio4(ased data
comm!nication
Incl!des voice over Internet =EoIP? technology
Ethics in Information Technology, Second Edition 1)
(overn!enta) &)ectronic urvei))ance
.
CS3 Patriot 3ct of 2;;1
Aives see$ing ne $oers to
6omestic la enforcement
International intelligence agencies
-ontains several 7s!nset9 $rovisions
Ethics in Information Technology, Second Edition 1+
(overn!enta) &)ectronic urvei))ance
-ry$togra$hy
Science of encoding messages
>nly sender and intended receiver can !nderstand the
messages
1ey tool for ens!ring confidentiality, integrity, a!thenticity
of electronic messages and online (!siness transactions
Encry$tion
Process of converting electronic messages into a form
!nderstood only (y the intended reci$ients
Ethics in Information Technology, Second Edition 1,
'ata &ncryption .
Encry$tion *ey
Earia(le val!e a$$lied !sing an algorithm to encry$t or
decry$t te5t
P!(lic *ey encry$tion system !ses to *eys
/essage receiver:s $!(lic *ey 4 readily availa(le
/essage receiver:s $rivate *ey 4 *e$t secret
RS3 4 a $!(lic *ey encry$tion algorithm
Private *ey encry$tion system
Single *ey to encode and decode messages
Ethics in Information Technology, Second Edition 2;
'ata &ncryption .
Ethics in Information Technology, Second Edition 21
Pub)ic ,ey &ncryption .
/ost $eo$le agree encry$tion event!ally m!st (e
(!ilt into
<etor*s
#ile servers
Ta$e (ac*!$ systems
Seagate Technology hard drive
3!tomatically encry$ts all data
C.S. 3rms E5$ort -ontrol 3ct controls the e5$ort
of encry$tion technology, hardare, and softare
Ethics in Information Technology, Second Edition 22
'ata &ncryption
Theft of *ey $ieces of $ersonal information to gain
access to a $erson:s financial acco!nts
Information incl!desH
<ame
3ddress
6ate of (irth
Social Sec!rity n!m(er
Pass$ort n!m(er
6river:s license n!m(er
/other:s maiden name
Ethics in Information Technology, Second Edition 2"
-dentity Theft .
#astest groing form of fra!d in the Cnited States
Lac* of initiative in informing $eo$le hose data
as stolen
Phishing
3ttem$t to steal $ersonal identity data
By tric*ing !sers into entering information on a
co!nterfeit We( site
S$ear4$hishing 4 a variation in hich em$loyees are sent
$hony e4mails that loo* li*e they came from high4level
e5ec!tives ithin their organiFation
Ethics in Information Technology, Second Edition 2%
-dentity Theft .
S$yare
1eystro*e4logging softare
Ena(les the ca$t!re ofH
3cco!nt !sernames
Passords
-redit card n!m(ers
>ther sensitive information
>$erates even if an infected com$!ter is not connected to
the Internet
Identity Theft and 3ss!m$tion 6eterrence 3ct of
1,,+ as $assed to fight fra!d
Ethics in Information Technology, Second Edition 2&
-dentity Theft .
Ethics in Information Technology, Second Edition 2'
&1!ai) 2sed by Phishers
-om$anies o$enly collect $ersonal information
a(o!t Internet !sers
-oo*ies
Te5t files that a We( site $!ts on a !ser:s hard drive so
that it can remem(er the information later
Trac*ing softare
Similar methods are !sed o!tside the We(
environment
6ata(ases contain a h!ge amo!nt of cons!mer
(ehavioral data
Ethics in Information Technology, Second Edition 2)
Consu!er Profi)ing .
3ffiliated We( sites
Aro!$ of We( sites served (y a single advertising
netor*
-!stomiFed service for each cons!mer
Ty$es of data collected hile s!rfing the We(
AET data
P>ST data
-lic*4stream data
Ethics in Information Technology, Second Edition 2+
Consu!er Profi)ing .
#o!r ays to limit or even sto$ the de$osit of
coo*ies on hard drives
Set the (roser to limit or sto$ coo*ies
/an!ally delete them from the hard drive
6onload and install a coo*ie4management $rogram
Cse anonymo!s (rosing $rograms that don:t acce$t
coo*ies
Ethics in Information Technology, Second Edition 2,
Consu!er Profi)ing .
PersonaliFation softare is !sed (y mar*eters to
o$timiFe the n!m(er, freD!ency, and mi5t!re of
their ad $lacements
R!les4(ased
-olla(orative filtering
6emogra$hic filtering
-onte5t!al commerce
Platform for Privacy Preferences =P"P?
Shields !sers from sites that don:t $rovide the level of
$rivacy $rotection desired
Ethics in Information Technology, Second Edition ";
Consu!er Profi)ing .
Strong meas!res are reD!ired to avoid c!stomer
relationshi$ $ro(lems
-ode of #air Information Practices
1,+; >E-6 $rivacy g!idelines
-hief $rivacy officer =-P>?
E5ec!tive to oversee data $rivacy $olicies and initiatives
Ethics in Information Technology, Second Edition "1
Treating Consu!er 'ata Responsib)y
Em$loyers monitor or*ers
Ens!res that cor$orate IT !sage $olicy is folloed
#o!rth 3mendment cannot (e !sed to limit ho a
$rivate em$loyer treats its em$loyees
P!(lic4sector em$loyees have far greater $rivacy rights
than in the $rivate ind!stry
Privacy advocates ant federal legislation
To *ee$s em$loyers from infringing !$on $rivacy rights of
em$loyees
Ethics in Information Technology, Second Edition "2
0or3p)ace 4onitoring
Transmission of the same e4mail message to a
large n!m(er of $eo$le
E5tremely ine5$ensive method of mar*eting
Csed (y many legitimate organiFations
-an contain !nanted and o(0ectiona(le
materials
Ethics in Information Technology, Second Edition ""
pa!!ing .
-ontrolling the 3ssa!lt of <on4Solicited
Pornogra$hy and /ar*eting =-3<SP3/?
Says it is legal to s$am (!t
S$ammers cannot disg!ise their identity
There m!st (e a la(el in the message s$ecifying that the e4
mail is an ad or solicitation
They m!st incl!de a ay for reci$ients to indicate they do not
ant f!t!re mass mailings
Ethics in Information Technology, Second Edition "%
pa!!ing
-amera s!rveillance
C.S. cities $lan to e5$and s!rveillance systems
7Smart s!rveillance system9
#acial recognition softare
Identifies criminal s!s$ects and other !ndesira(le
characters
Iields mi5ed res!lts
Alo(al Positioning System =APS? chi$s
Placed in many devices
Precisely locate !sers
Ethics in Information Technology, Second Edition "&
+dvanced urvei))ance Techno)ogy
-ha$ter % Page 1"%
Ethics in Information Technology, Second Edition "'
u!!ary +ssess!ent 5uestions
2/2&' L-'&
#R>/ TEJTB>>1
Ethics in Information Technology, Second Edition ")
What is the right of $rivacy, and hat is the (asis
for $rotecting $ersonal $rivacy !nder the la?
What are some of the las that a!thoriFe
electronic s!rveillance (y the government, and
hat are the associated ethical iss!es?
What are the to f!ndamental forms of data
encry$tion, and ho does each or*?
Ethics in Information Technology, Second Edition "+
Objectives
What is identity theft, and hat techniD!es do
identity thieves !se?
What are the vario!s strategies for cons!mer
$rofiling and the associated ethical iss!es?
What m!st organiFations do to treat cons!mer
data res$onsi(ly?
Ethics in Information Technology, Second Edition ",
Objectives (continued)
Why and ho are em$loyers increasingly !sing
or*$lace monitoring?
What is s$amming, and hat ethical iss!es are
associated ith its !se?
What are the ca$a(ilities of advanced s!rveillance
technologies, and hat ethical iss!es do they
raise?
Ethics in Information Technology, Second Edition %;
Objectives (continued)
Ethics in Information Technology, Second Edition %1
,ey Provisions of the 2+ Patriot +ct ubject
to unset
Ethics in Information Technology, Second Edition %2
,ey Provisions of the 2+ Patriot +ct ubject
to unset (continued)
Ethics in Information Technology, Second Edition %"
4anager6s Chec3)ist for Treating
Consu!er 'ata Responsib)y
The legal conce$t of the right to $rivacy has fo!r
as$ects
3 n!m(er of las have (een enacted over the
$ast %; years that affect a $erson:s $rivacy
Las a!thoriFe electronic s!rveillance (y the
government
6ata encry$tion
P!(lic *ey encry$tion system
Private *ey encry$tion system
Identity theft
Ethics in Information Technology, Second Edition %%
u!!ary
-ons!mer (ehavior data is collected (oth online
and offline
-ode of #air Information Practices and 1,+;
>E-6 $rivacy g!idelines
Em$loyers record and revie em$loyee
comm!nications and activities on the 0o(
3dvances in information technology
S!rveillance cameras
#acial recognition softare
APS systems
Ethics in Information Technology, Second Edition %&
u!!ary (continued)
Potrebbero piacerti anche
- Social and Professional EthicsDocumento5 pagineSocial and Professional EthicsJenyll MabborangNessuna valutazione finora
- THC6 - Module1Documento7 pagineTHC6 - Module1Neil CutterNessuna valutazione finora
- THC6 - Module 3Documento6 pagineTHC6 - Module 3Neil CutterNessuna valutazione finora
- THC6 - Module1Documento7 pagineTHC6 - Module1Neil CutterNessuna valutazione finora
- Part 4 - The Netiquette and Computer EthicsDocumento12 paginePart 4 - The Netiquette and Computer EthicsPolane GumiranNessuna valutazione finora
- Santos UtilitarianismDocumento11 pagineSantos UtilitarianismKyo AmiNessuna valutazione finora
- Module Iii Cyber CrimesDocumento198 pagineModule Iii Cyber CrimesGuru CharanNessuna valutazione finora
- GEd 107 ETHICS - FINAL PROJECTDocumento2 pagineGEd 107 ETHICS - FINAL PROJECTAubrey Ramilo100% (1)
- Personal and Professional Ethics: Unit IDocumento21 paginePersonal and Professional Ethics: Unit IJagadeesh Putturu100% (1)
- Cybercrime OffensesDocumento20 pagineCybercrime Offensescamille capalacNessuna valutazione finora
- #2 Ethics For IT Professionals and IT UsersDocumento36 pagine#2 Ethics For IT Professionals and IT UsersShoggi Lalog0% (1)
- Euthenics Prelims CoverageDocumento14 pagineEuthenics Prelims CoverageDarlene De PazNessuna valutazione finora
- Electrify Real-Time Analysis of Electricity Consumption and Bill PredictionDocumento3 pagineElectrify Real-Time Analysis of Electricity Consumption and Bill PredictionInternational Journal of Innovative Science and Research TechnologyNessuna valutazione finora
- Lesson 4 - Ethical TheoriesDocumento33 pagineLesson 4 - Ethical TheoriesqhaireenaNessuna valutazione finora
- Discrimination Against Law Enforcement Officers On The Basis of Sexual Orientation and Gender Identity: 2000 To 2013Documento51 pagineDiscrimination Against Law Enforcement Officers On The Basis of Sexual Orientation and Gender Identity: 2000 To 2013therepubliq.comNessuna valutazione finora
- Character Formation With LeadershipDocumento132 pagineCharacter Formation With LeadershipMaria AnnaNessuna valutazione finora
- What Is A Computer NetworkDocumento22 pagineWhat Is A Computer NetworkAakash DashNessuna valutazione finora
- Chapter 1 - The HumanDocumento45 pagineChapter 1 - The HumanMD HOSSAINNessuna valutazione finora
- Cyber EthicsDocumento16 pagineCyber EthicsDeepali RaniNessuna valutazione finora
- Introduction To Computers and ComputingDocumento31 pagineIntroduction To Computers and ComputingAdedotun J. AgbemukoNessuna valutazione finora
- Validated Survey QuestionnairesDocumento4 pagineValidated Survey QuestionnairesAnthonyNessuna valutazione finora
- Ethics in Information Technology, Fourth Edition: PrivacyDocumento42 pagineEthics in Information Technology, Fourth Edition: PrivacyJohn Carlo Lalap100% (1)
- SyllabusDocumento2 pagineSyllabusporseenaNessuna valutazione finora
- An Overview of Ethics: Source: Thomson Course Technology Ethics in Information Technology 2 EditionDocumento26 pagineAn Overview of Ethics: Source: Thomson Course Technology Ethics in Information Technology 2 EditionGary TeongNessuna valutazione finora
- Introduction To Intelligent SystemsDocumento3 pagineIntroduction To Intelligent SystemsOana MunteanuNessuna valutazione finora
- SD3 1 1Documento3 pagineSD3 1 1Monica EnescuNessuna valutazione finora
- Chapter1 Orientation To The NSTP-CWTDocumento39 pagineChapter1 Orientation To The NSTP-CWTRizzy UgayNessuna valutazione finora
- CF 101Documento25 pagineCF 101Johnpatrick Dejesus100% (1)
- ICT Application in Everyday LifeDocumento2 pagineICT Application in Everyday LifeGHSNessuna valutazione finora
- Factors Influencing Organizational Change EffortsDocumento10 pagineFactors Influencing Organizational Change EffortsYudha WidyantoroNessuna valutazione finora
- Ethical Issue in Organisational CultureDocumento21 pagineEthical Issue in Organisational CulturevishnuastpNessuna valutazione finora
- A Guide To APA CitationDocumento31 pagineA Guide To APA CitationHabiba RostomNessuna valutazione finora
- Area Iv: Support To StudentsDocumento17 pagineArea Iv: Support To Studentsmary jane lutianNessuna valutazione finora
- National SecurityDocumento2 pagineNational SecurityArchie CuyacotNessuna valutazione finora
- Computers in Our Daily LifeDocumento27 pagineComputers in Our Daily Lifeleah manuelNessuna valutazione finora
- Final Research On Culture, Value and Ethics - 4Documento18 pagineFinal Research On Culture, Value and Ethics - 4api-284404479Nessuna valutazione finora
- Test For EthicsDocumento1 paginaTest For EthicsShaggy SamNessuna valutazione finora
- Syllabus in Group Dynamics PsychologyDocumento7 pagineSyllabus in Group Dynamics PsychologyCristina LolosNessuna valutazione finora
- Ethics' Exam QuestionsDocumento2 pagineEthics' Exam QuestionsJackylou BlancoNessuna valutazione finora
- Industrial and Organizational Psychology-SLM2Documento12 pagineIndustrial and Organizational Psychology-SLM2CHESSCA ERA100% (2)
- Chapter 3 - UTS (Anthropological Perspective)Documento26 pagineChapter 3 - UTS (Anthropological Perspective)James CancinoNessuna valutazione finora
- Chapter 5 Anonymity, Security, Privacy and Civil LibertiesDocumento13 pagineChapter 5 Anonymity, Security, Privacy and Civil LibertiesFidelRomasanta100% (1)
- How The Experimental Method Works in Psychology-1Documento55 pagineHow The Experimental Method Works in Psychology-1Paul MorakinyoNessuna valutazione finora
- Ethics Updated Im 1 2Documento75 pagineEthics Updated Im 1 2onasakenNessuna valutazione finora
- Sikolohiyang PilipinoDocumento9 pagineSikolohiyang PilipinoMargielane AcalNessuna valutazione finora
- Software Project Softpro: Course Learning PlanDocumento8 pagineSoftware Project Softpro: Course Learning PlanRommel L. DorinNessuna valutazione finora
- Communication in Managment AyaDocumento19 pagineCommunication in Managment AyaAya EyadNessuna valutazione finora
- IT, Culture and The SocietyDocumento88 pagineIT, Culture and The SocietyZꪖʀᥴʜTɀꪗ.100% (1)
- Ethics in A Computing Culture: Computing and Vulnerable GroupsDocumento15 pagineEthics in A Computing Culture: Computing and Vulnerable GroupsJoseph CailaoNessuna valutazione finora
- IT, Culture, and The Society: Group 5Documento20 pagineIT, Culture, and The Society: Group 5Maria Paz GanotNessuna valutazione finora
- Computer Ethics and Legal IssuesDocumento7 pagineComputer Ethics and Legal IssuesdeenincNessuna valutazione finora
- Experimental Psychology & The Scientific MethodDocumento73 pagineExperimental Psychology & The Scientific MethodRuru LavariasNessuna valutazione finora
- Module 2 Moral AgentDocumento18 pagineModule 2 Moral AgentEcho MartinezNessuna valutazione finora
- Activity Matrix For Taps and MoldDocumento5 pagineActivity Matrix For Taps and MoldNilo ZolinaNessuna valutazione finora
- Effective and Responsible Use of Computer and InternetDocumento23 pagineEffective and Responsible Use of Computer and InternetSheena BustargaNessuna valutazione finora
- Sex and Gender RolesDocumento25 pagineSex and Gender RolesMaharu MathewosNessuna valutazione finora
- Experimental Psychology Lecture Activity Worksheet No. 1 Module 2: Research EthicsDocumento1 paginaExperimental Psychology Lecture Activity Worksheet No. 1 Module 2: Research EthicsCarollyne cruzNessuna valutazione finora
- Political Self PDFDocumento39 paginePolitical Self PDFANGELICA TALOSIGNessuna valutazione finora
- Cyber ForensicsDocumento35 pagineCyber ForensicsNilesh Telore100% (1)
- Faza 2Documento6 pagineFaza 2MIHAIL ALEXANDRU MOLDOVANNessuna valutazione finora
- PPP Feature Config Guide Rev CDocumento29 paginePPP Feature Config Guide Rev CSai Kyaw HtikeNessuna valutazione finora
- Effectivekotlin PDFDocumento486 pagineEffectivekotlin PDFNghia Nguyen100% (6)
- Booking of Expenses To Correct Account HeadDocumento2 pagineBooking of Expenses To Correct Account HeadVinay SinghNessuna valutazione finora
- Particle Flow OrbazDocumento159 pagineParticle Flow OrbazAna QuintanaNessuna valutazione finora
- Reimage FTDDocumento46 pagineReimage FTDgica hagiNessuna valutazione finora
- P Median ModelDocumento26 pagineP Median ModelLeonardo CetreNessuna valutazione finora
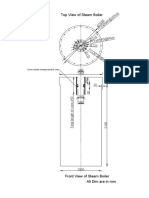
- Top View of Steam Boiler: PCDØ270@6NosDocumento1 paginaTop View of Steam Boiler: PCDØ270@6NosAnkur SinghNessuna valutazione finora
- Iiyama 19LJ2 Service ManualDocumento41 pagineIiyama 19LJ2 Service ManualRoger Martínez BermúdezNessuna valutazione finora
- Computational GraphDocumento17 pagineComputational GraphRam MurthyNessuna valutazione finora
- Distillation Operation, Control, Design and Troubleshooting Course For Maintenance PersonnelDocumento8 pagineDistillation Operation, Control, Design and Troubleshooting Course For Maintenance PersonnelBadiuzzama AzmiNessuna valutazione finora
- Indigo ManualDocumento232 pagineIndigo Manualjasopanev100% (2)
- HPE ProLiant DL345 Gen11 QuickSpecs - A50004298enw - 2024-03 - v15Documento54 pagineHPE ProLiant DL345 Gen11 QuickSpecs - A50004298enw - 2024-03 - v15Franck JOLYNessuna valutazione finora
- Jacob's ResumeDocumento3 pagineJacob's ResumeJohn BolzeniusNessuna valutazione finora
- OSF - Open-Source Miniature Spectrophotometer WikiDocumento3 pagineOSF - Open-Source Miniature Spectrophotometer WikibiznizNessuna valutazione finora
- BST106-M10 (FB) Weighing Controller: Operation Manual V5.0Documento61 pagineBST106-M10 (FB) Weighing Controller: Operation Manual V5.029374925morNessuna valutazione finora
- Service Manual Lex MX 310 410 510.PDF 2Documento394 pagineService Manual Lex MX 310 410 510.PDF 2Wellington SantosNessuna valutazione finora
- 1945 To Spy Chase TutorialDocumento21 pagine1945 To Spy Chase TutorialMagda GarzaNessuna valutazione finora
- Unit 3 - NormalizationDocumento59 pagineUnit 3 - NormalizationNimish MakhariaNessuna valutazione finora
- Service Manual: - CD6000 / CD6000OSEDocumento28 pagineService Manual: - CD6000 / CD6000OSELeonardo SantanaNessuna valutazione finora
- Iso 10083 2006 en FR PDFDocumento11 pagineIso 10083 2006 en FR PDFGiovanni BalderramaNessuna valutazione finora
- HEC-ResSim 30 UsersManual PDFDocumento512 pagineHEC-ResSim 30 UsersManual PDFvitensaNessuna valutazione finora
- Java Mock3Documento19 pagineJava Mock3rishiimcaNessuna valutazione finora
- Tra 41a Servo Drive Mitsubishi ManualDocumento28 pagineTra 41a Servo Drive Mitsubishi Manualsasa mitic100% (1)
- 2012 Asean GsdaaDocumento319 pagine2012 Asean GsdaaMenandro AmbanlocNessuna valutazione finora
- Kumbharana CK Thesis CsDocumento243 pagineKumbharana CK Thesis CsYadu KrishnanNessuna valutazione finora
- AS400 Questions SDocumento21 pagineAS400 Questions SNaveen SaharanNessuna valutazione finora
- ZNC Die Sinking Edm MachineDocumento73 pagineZNC Die Sinking Edm MachineCommecha SYSNessuna valutazione finora
- AB350M Pro4Documento72 pagineAB350M Pro4DanReteganNessuna valutazione finora
- 4004 Installation & Operating Manual Rev CDocumento36 pagine4004 Installation & Operating Manual Rev Cmannyb2000Nessuna valutazione finora