Documenti di Didattica
Documenti di Professioni
Documenti di Cultura
01 - 7225-IJWCS - PP 1-6
Caricato da
Hemant RajakDescrizione originale:
Titolo originale
Copyright
Formati disponibili
Condividi questo documento
Condividi o incorpora il documento
Hai trovato utile questo documento?
Questo contenuto è inappropriato?
Segnala questo documentoCopyright:
Formati disponibili
01 - 7225-IJWCS - PP 1-6
Caricato da
Hemant RajakCopyright:
Formati disponibili
International Journal of Wireless Communication and Simulation Volume 3 Number 1 (2011), pp. 1-6 Research India Publications http://www.ripublication.com/ijwcs.
htm
Simulation and Analysis of Chaotic Sequence based Encryption Method for Different Wireless Communication Systems
1
Swapnil Shrivastava and 2Sumit Sharma
1
M.Tech., SRIT, Jabalpur, M.P., India E-mail: swapnilmtech@yahoo.in 2 H.O.D., EC Deptt., SRIT Jabalpur, M.P., India
Abstract Security is an important issue in all communications systems for the users and providers of such systems. Although mobile application have special requirements because it is accessible for every one within the range of transmitter and are therefore of special concern. Encryption of the data by some way is one of the simplest solutions for stated problem but for the proper operation of the system the method must be fast enough and should be simple so that it can implemented on the low resources mobile devices, also it should not increase the power requirements of the systems. In this paper we proposed and analyzed the chaotic sequence based encryption technique for different types of communication systems like OFDM, CDMA, QPSK and GMSK, and we also simulated the BER of each system with respect to SNR. The simulation of all techniques is done on MATLAB. Keywords: Wireless Communication, Encryption, Chaotic Sequence.
Introduction
Mobile devices are designed to be portable, i.e., light and small. Until a more suitable alternative is found, mobile devices will more than likely be battery powered within the foreseeable future. In order to conserve energy, processing speeds need to be slower and processor cycles reduced. Data transmissions also consume energy therefore it must be reduced. The former imposes limits on the computational complexity of encryption algorithms and the number of messages involved in security protocols. Even though using special purpose circuitry or encryption chips can
Swapnil Shrivastava and Sumit Sharma
alleviate this problem. Faxed business letters can be intercepted at will through tapped phone lines or intercepted microwave transmissions without the knowledge of the sender or receiver. To increase the security of this and other data communications, including digitized telephone conversations, the binary codes representing data may be scrambled in such a way that unauthorized interception will produce an indecipherable sequence of characters. Authorized receive stations will be equipped with a decoder that enables the message to be restored. The process of scrambling, transmitting, and descrambling is known as encryption. This paper presents the chaotic sequence based encryption technique which can be easily programmed in main processor or can be implemented on integrated circuits at low cost. In some cases, it can be incorporated into the main circuitry of a data communications device and function without operator knowledge. In other cases, an external circuit can also be used so that the device, and its encrypting/decrypting technique, may be transported easily.
Chaotic Sequences
Chaos is a deterministic, random-like process found in non-linear, dynamical system, which is non-period, non-converging and bounded. Moreover, it has a very sensitive dependence upon its initial condition and parameter. Chaotic signals can be used in communication. A chaotic map is a discrete-time dynamical system
x k +1 = f ( x k ), 0 < x k < 1, k = 0, 1, 2,
running in chaotic state. The chaotic sequence
{x k :
k = 0, 1, 2,
can be used as spread-spectrum sequence in place of PN sequence in conventional CDMA DS/SS communication systems or as encrypting sequence in any digital communication system. Chaotic sequences are uncorrelated when their initial values are different, so in chaotic spread-spectrum systems, a user corresponds to an initial value. In addition, it is possible to synchronize two copies of a discrete-time chaotic system, in the sense that their state trajectories tend asymptotically to be identical when one system is suitably driven by the other. If the driving signal is selected appropriately, the discrete-time synchronization will be immediate.
OFDM
Orthogonal frequency division multiplexing, (OFDM), essentially identical to coded OFDM (COFDM) and discrete multi-tone modulation (DMT), is a frequency-division
Simulation and Analysis of Chaotic Sequence
multiplexing (FDM) scheme used as a digital multi-carrier modulation method. A large number of closely-spaced orthogonal sub-carriers are used to carry data. The data is divided into several parallel data streams or channels, one for each sub-carrier. Each sub-carrier is modulated with a conventional modulation scheme (such as quadrature amplitude modulation or phase-shift keying) at a low symbol rate, maintaining total data rates similar to conventional single carrier modulation schemes in the same bandwidth. OFDM has developed into a popular scheme for wideband digital communication, whether wireless or over copper wires, used in applications such as digital television and audio broadcasting, wireless networking and broad band internet access. The primary advantage of OFDM over single-carrier schemes is its ability to cope with severe channel conditions (for example attenuation of high frequencies in a long copper wire, narrowband interference and frequency-selective fading due to multipath) without complex equalization filters. Channel equalization is simplified because OFDM may be viewed as using many slowly-modulated narrowband signals rather than one rapidly-modulated wideband signal. The low symbol rate makes the use of a guard interval between symbols affordable, making it possible to eliminate intersymbol interference (ISI) and utilize echoes and time-spreading (that shows up as ghosting on analogue TV) to achieve a diversity gain, i.e. a signal-to-noise ratio improvement. This mechanism also facilitates the design of single frequency networks (SFNs), where several adjacent transmitters send the same signal simultaneously at the same frequency, as the signals from multiple distant transmitters may be combined constructively, rather than interfering as would typically occur in a traditional single-carrier system.
CDMA
In telecommunications, direct-sequence spread spectrum (DSSS) is a modulation technique. As with other spread spectrum technologies, the transmitted signal takes up more bandwidth than the information signal that is being modulated. The name 'spread spectrum' comes from the fact that the carrier signals occur over the full bandwidth (spectrum) of a device's transmitting frequency. 802.11b use DSSS signaling. DSSS phase-modulates a sine wave pseudo randomly with a continuous string of pseudo noise (PN) code symbols called "chips", each of which has a much shorter duration than an information bit. That is, each information bit is modulated by a sequence of much faster chips. Therefore, the chip rate is much higher than the information signal bit rate. DSSS uses a signal structure in which the sequence of chips produced by the transmitter is known a priori by the receiver. The receiver can then use the same PN sequence to counteract the effect of the PN sequence on the received signal in order to reconstruct the information signal.
Swapnil Shrivastava and Sumit Sharma
GMSK
In digital modulation, minimum-shift keying (MSK) is a type of continuousphase frequency-shift keying that was developed in the late 1950s and 1960s.Similar to OQPSK, MSK is encoded with bits alternating between quadature components, with the Q component delayed by half the symbol period. However, instead of square pulses as OQPSK uses, MSK encodes each bit as a half sinusoid. This results in a constant-modulus signal, which reduces problems caused by non-linear distortion. In addition to being viewed as related to OQPSK, MSK can also be viewed as a continuous phase frequency shift keyed (CPFSK) signal with a frequency separation of one-half the bit rate.
QPSK
Sometimes this is known as quaternary PSK, quadriphase PSK, 4-PSK, or 4-QAM. (Although the root concepts of QPSK and 4-QAM are different, the resulting modulated radio waves are exactly the same.) QPSK uses four points on the constellation diagram, equispaced around a circle. With four phases, QPSK can encode two bits per symbol, shown in the diagram with gray coding to minimize the bit error rate (BER) sometimes misperceived as twice the BER of BPSK. The mathematical analysis shows that QPSK can be used either to double the data rate compared with a BPSK system while maintaining the same bandwidth of the signal, or to maintain the data-rate of BPSK but halving the bandwidth needed. In this latter case, the BER of QPSK is exactly the same as the BER of BPSK - and deciding differently is a common confusion when considering or describing QPSK. Given that radio communication channels are allocated by agencies such as the Federal Communication Commission giving a prescribed (maximum) bandwidth, the advantage of QPSK over BPSK becomes evident: QPSK transmits twice the data rate in a given bandwidth compared to BPSK - at the same BER. The engineering penalty that is paid is that QPSK transmitters and receivers are more complicated than the ones for BPSK. However, with modern electronics technology, the penalty in cost is very moderate. As with BPSK, there are phase ambiguity problems at the receiving end, and differentially encoded QPSK is often used in practice.
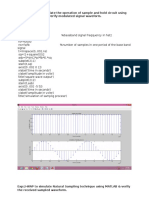
Simulation Results
Each of the above mentioned method are implemented and simulated on matlab the simulation are performed for 104 bits, and for different AWGN values, in all simulation the main data stream is firstly encrypted by using chaotic encryption technique and then at receiver side decrypted using same technique.
Simulation and Analysis of Chaotic Sequence
Figure 1: Performance of OFDM System with Chaotic sequence based encryption technique.
Figure 2: Performance of CDMA System with Chaotic sequence based encryption technique.
Figure 3: Performance of QPSK System with Chaotic sequence based encryption technique.
Swapnil Shrivastava and Sumit Sharma
Figure 4: Performance of GMSK System with Chaotic sequence based encryption technique.
Conclusion
The results shows that the encryption scheme does not affects the basic characteristics of the modulation techniques and hence it can be adopted as a fast and efficient encryption method in either in built system or with external devices.
References
[1] O. Edfors, M. Sandell, J.-J. de Beek, D. Landstrom, F.Sjoberg, \An introduction to orthogonal frequency-divisionmultiplexing," [2] E. Lawrey, \The suitability of ofdm as a modulation tech-nique for wireless telecommunications, with a cdma com-parison," MSc. thesis, James Cook University, Australia,October 1997. [3] A. Engelhart, H. Gryska, C. Sgraja, W.G. Teich, J. Lind-ner, \The discrete-time channel matrix model for general bfdm packet transmission schemes," Proceedings of 1 st In- ternational POFDM-Workshop Hamburg, 21-22 September 1999. [4] J. Proakis, Digital Communications. New York: McGraw-Hill, 3 ed., 1995. [5] N. Yee, J.P.M.G. Linnartz, \Multi-carrier CDMA in an in-door wirless radio channel," UCB/ERL, 1994. U.C. Berke-ley, UCB/ERL M94/6, Electronics Research Lab. [6] R. van Nee, R. Pasad, OFDM for Wireless Multimedia Communication. Boston London: Artech House Publishers,2000. [7] T. Keller, L. Hanzo, \Adaptive multicarrier modulation:A convencient framework for time-frequency processing in wireless communications," Procideengs of the IEEE, vol. 88,May 2000.
Potrebbero piacerti anche
- Grit: The Power of Passion and PerseveranceDa EverandGrit: The Power of Passion and PerseveranceValutazione: 4 su 5 stelle4/5 (588)
- The Yellow House: A Memoir (2019 National Book Award Winner)Da EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Valutazione: 4 su 5 stelle4/5 (98)
- Digital ComDocumento22 pagineDigital ComHemant RajakNessuna valutazione finora
- Computer As A Comonent - WolfDocumento11 pagineComputer As A Comonent - WolfHemant RajakNessuna valutazione finora
- Basic Simulation LAB ManualDocumento90 pagineBasic Simulation LAB ManualHemant RajakNessuna valutazione finora
- CH 02Documento48 pagineCH 02Hemant RajakNessuna valutazione finora
- SCFT Tracker 24-FebDocumento140 pagineSCFT Tracker 24-FebHemant RajakNessuna valutazione finora
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeDa EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeValutazione: 4 su 5 stelle4/5 (5795)
- Never Split the Difference: Negotiating As If Your Life Depended On ItDa EverandNever Split the Difference: Negotiating As If Your Life Depended On ItValutazione: 4.5 su 5 stelle4.5/5 (838)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceDa EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceValutazione: 4 su 5 stelle4/5 (895)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersDa EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersValutazione: 4.5 su 5 stelle4.5/5 (345)
- Shoe Dog: A Memoir by the Creator of NikeDa EverandShoe Dog: A Memoir by the Creator of NikeValutazione: 4.5 su 5 stelle4.5/5 (537)
- The Little Book of Hygge: Danish Secrets to Happy LivingDa EverandThe Little Book of Hygge: Danish Secrets to Happy LivingValutazione: 3.5 su 5 stelle3.5/5 (400)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureDa EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureValutazione: 4.5 su 5 stelle4.5/5 (474)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryDa EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryValutazione: 3.5 su 5 stelle3.5/5 (231)
- On Fire: The (Burning) Case for a Green New DealDa EverandOn Fire: The (Burning) Case for a Green New DealValutazione: 4 su 5 stelle4/5 (74)
- The Emperor of All Maladies: A Biography of CancerDa EverandThe Emperor of All Maladies: A Biography of CancerValutazione: 4.5 su 5 stelle4.5/5 (271)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaDa EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaValutazione: 4.5 su 5 stelle4.5/5 (266)
- The Unwinding: An Inner History of the New AmericaDa EverandThe Unwinding: An Inner History of the New AmericaValutazione: 4 su 5 stelle4/5 (45)
- Team of Rivals: The Political Genius of Abraham LincolnDa EverandTeam of Rivals: The Political Genius of Abraham LincolnValutazione: 4.5 su 5 stelle4.5/5 (234)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyDa EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyValutazione: 3.5 su 5 stelle3.5/5 (2259)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreDa EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreValutazione: 4 su 5 stelle4/5 (1091)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)Da EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Valutazione: 4.5 su 5 stelle4.5/5 (121)
- Her Body and Other Parties: StoriesDa EverandHer Body and Other Parties: StoriesValutazione: 4 su 5 stelle4/5 (821)
- East Halmahera Ferronickel Development Project (P3Fh Project)Documento2 pagineEast Halmahera Ferronickel Development Project (P3Fh Project)nailulfalah17Nessuna valutazione finora
- 994609AGDocumento93 pagine994609AGPipis FakidomitisNessuna valutazione finora
- Vikantsram SpecsDocumento9 pagineVikantsram SpecschinhctmNessuna valutazione finora
- Automation and Robotics '20-1Documento102 pagineAutomation and Robotics '20-1Raphael IbrahNessuna valutazione finora
- ACPS-610 (E) : Addressable Charger/Power SupplyDocumento2 pagineACPS-610 (E) : Addressable Charger/Power Supplyfercha589Nessuna valutazione finora
- M SCD enDocumento204 pagineM SCD enMosargt ArgNessuna valutazione finora
- C191HM Powermeter and Harmonic Manager CommunicationsDocumento30 pagineC191HM Powermeter and Harmonic Manager CommunicationsRoberto GarridoNessuna valutazione finora
- Abstract of Fiber Optic SensorsDocumento6 pagineAbstract of Fiber Optic SensorsKamal UniyalNessuna valutazione finora
- Flashing LEDDocumento5 pagineFlashing LEDrashid sharifNessuna valutazione finora
- PN-Junction Diode Characteristics: Forward BiasDocumento17 paginePN-Junction Diode Characteristics: Forward BiasyasaslitNessuna valutazione finora
- Lg+29ln450b,+450u,+457b,+457u+ch +la31r+led+tvDocumento35 pagineLg+29ln450b,+450u,+457b,+457u+ch +la31r+led+tvСтоян ДимитровNessuna valutazione finora
- Dewanto Arby Hudhaya PDFDocumento9 pagineDewanto Arby Hudhaya PDFWiddy TimursariNessuna valutazione finora
- Crystal Growth Techniques PDFDocumento30 pagineCrystal Growth Techniques PDFanisNessuna valutazione finora
- CR1000 DataloggerDocumento630 pagineCR1000 DataloggersudirmanpriyoNessuna valutazione finora
- 3 Periodical Test in Science V: Councilor Nicolas Dais Elementary SchoolDocumento6 pagine3 Periodical Test in Science V: Councilor Nicolas Dais Elementary SchoolRed MariposaNessuna valutazione finora
- D.C. Power Supply: Experiment ADocumento5 pagineD.C. Power Supply: Experiment AReddyvari VenugopalNessuna valutazione finora
- Research PaperDocumento7 pagineResearch PaperPatrick Jose Dela VegaNessuna valutazione finora
- Assembly - Manual - FELIX - 3 - 0 - Eng - V3 - B PDFDocumento45 pagineAssembly - Manual - FELIX - 3 - 0 - Eng - V3 - B PDFAnonymous JDHMOvNessuna valutazione finora
- WiFi-Card DSDocumento1 paginaWiFi-Card DSMtech ServSolNessuna valutazione finora
- Our Technology: Small Character Inkjet PrintersDocumento2 pagineOur Technology: Small Character Inkjet Printersaavr679241Nessuna valutazione finora
- ZTE UMTS UR15 License Management SolutionDocumento23 pagineZTE UMTS UR15 License Management Solutionmickyalemu100% (1)
- SCR Control of Electric HeatersDocumento3 pagineSCR Control of Electric HeatersHayden Lovett100% (2)
- Ti Tas5630 EvmDocumento1 paginaTi Tas5630 EvmTrenton Astley IslaNessuna valutazione finora
- Operating Manual: CAL ControlsDocumento39 pagineOperating Manual: CAL ControlskmpoulosNessuna valutazione finora
- RFID Door LockDocumento37 pagineRFID Door LockRika HarianyNessuna valutazione finora
- Benchmark Report Serbia 2017Documento18 pagineBenchmark Report Serbia 2017thabetNessuna valutazione finora
- Step 1: Materials Required: This Instructable Comes in 2 Parts: (I) Troubleshooting and (II) Fuse ReplacementDocumento12 pagineStep 1: Materials Required: This Instructable Comes in 2 Parts: (I) Troubleshooting and (II) Fuse ReplacementJiremy NoriegaNessuna valutazione finora
- Fundamentals of Electrical Engineering - R. PrasadDocumento303 pagineFundamentals of Electrical Engineering - R. PrasadrajkumarNessuna valutazione finora
- Reliance Electric Psc7000 Operating Instructions Manual 84Documento84 pagineReliance Electric Psc7000 Operating Instructions Manual 84Sinan OzaslanNessuna valutazione finora