Documenti di Didattica
Documenti di Professioni
Documenti di Cultura
Web Application Audit Report: Demo Account
Caricato da
Samuel KonanTitolo originale
Copyright
Formati disponibili
Condividi questo documento
Condividi o incorpora il documento
Hai trovato utile questo documento?
Questo contenuto è inappropriato?
Segnala questo documentoCopyright:
Formati disponibili
Web Application Audit Report: Demo Account
Caricato da
Samuel KonanCopyright:
Formati disponibili
Web Application Audit Report
Demo Account
http://tes thtml5.vulnweb.com/#/popular
Confidential
Scan Date: 2017-01-16
Scope
Application Audit for URL http://tes thtml5.vulnweb.com/#/popular
Limitations
1. The entire tes t was carried out with no prior knowledge of the s ys tems and applications .
2. All tes t were carried out without any known credentials to s ys tems and applications .
3. Indus Guard does not allowed to carry out any DoS attacks or to run any exploits which can affect s ys tems
availability.
Confidentiality
This document contains s ens itive and/or confidential information, do not dis tribute, email, fax or trans fer via any
electronic mechanis m without proper authorization. Information contained with in this document s hould be handled with
appropriate caution. While reas onable attempts have been made to confirm the accuracy of the data contained herein,
Indus Guard, as s umes no liability for the completenes s , us e of, or conclus ions drawn from s uch data.
Disclaimer
This , or any other, Security Audit cannot and does not guarantee s ecurity. Indus Guard makes no warranty or claim of any
kind, whats oever, about the accuracy or us efulnes s of any information provided herein. By us ing this information you
agree that Indus Guard s hall be held harmles s in any event. Indus Guard makes this information available s olely under its
Terms of Service Agreement publis hed at s oc.indus guard.com.
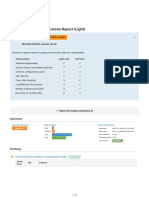
Executive Summary
Total number of vulnerability(s ) identified are 13
Page 2 of 12
Scan Date: 2017-01-16
Vulnerability v/s Severity Pie Chart Vulnerability v/s Open Status Pie Chart
Vulnerability v/s Severity Bar Chart Vulnerability Summary
Severity Total
Critical 1
High 1
Medium 1
Low 9
Info 1
Page 3 of 12
Scan Date: 2017-01-16
Vulnerability Details
Title Total
HTTP Bas ic Authentication Enabled 1
Cros s Site Scripting Vulnerability 1
Form action s ubmits s ens itive data in the 1
clear
Autocomplete enabled for s ens itive HTML 1
form fields
Predictable res ource location 8
Web s erver vers ion dis clos ure 1
Vulnerabilities
Alert ID: 481472 Found on: 2017-01-16 Severity: Critical
HTTP Basic Authentication Enabled
Open Status: NEW First Found: 2017-01-16
URL: http://tes thtml5.vulnweb.com/admin
Method: get
Cvss Score: 6.5
Cvss Vector: (AV:N/AC:L/Au:S/C:P/I:P/A:P)
PCI Compliance: Fail
Description:
The HTTP Bas ic Authentication s cheme is not cons idered to be a s ecure method of us er authentication (unles s us ed in
conjunction with s ome external s ecure s ys tem s uch as TLS/SSL), as the us er name and pas s word are pas s ed over the
network as cleartext.
Solution:
Us e Bas ic Authentication over TLS/SSL (HTTPS)
Enable HTTPS on the Web s erver. The TLS/SSL protocol will protect cleartext Bas ic Authentication credentials .
Us e Diges t Authentication
Replace Bas ic Authentication with the alternative Diges t Authentication s cheme. By modern cryptographic
s tandards Diges t Authentication is weak. But for a large range of purpos es it is valuable as a replacement for Bas ic
Authentication. It remedies s ome, but not all, weaknes s es of Bas ic Authentication. See RFC 2617, s ection 4. Security
Cons iderations for more information.
Request Header:
GET /admin HTTP/1.1 Referer: http://tes thtml5.vulnweb.com Us er-Agent: Mozilla/5.0 (Windows NT 6.1)
AppleWebKit/537.31 (KHTML, like Gecko) Chrome/26.0.1410.64 Safari/537.31 Accept: */* Hos t:
tes thtml5.vulnweb.com Connection: Clos e
Response Header:
HTTP/1.1 401 Unauthorized Connection: clos e Content-Length: 90 Content-Type: text/html; chars et=utf-8
Date: Mon, 16 Jan 2017 10:21:29 GMT Server: nginx/1.4.1 WWW-Authenticate: Bas ic realm="Login
Required"
Result:
Line No:6 Server: nginx/1.4.1
Line No:7 WWW-Authenticate: Basic realm ="Login Required"
Page 4 of 12
Scan Date: 2017-01-16
Line No:8
References:
http://tools .ietf.org/html/rfc2617
Alert ID: 481470 Found on: 2017-01-16 Severity: High
Cross Site Scripting Vulnerability
Open Status: NEW First Found: 2017-01-16
URL: http://tes thtml5.vulnweb.com/login
Method: POST
Vector: "><s CrIpT>alert(391700)</s CrIpT>
Cvss Score: 6.4
Cvss Vector: (AV:N/AC:L/Au:N/C:P/I:P/A:N)
PCI Compliance: Fail
Description:
The Web application is vulnerable to cros s -s ite s cripting (XSS), which allows attackers to take advantage of Web s erver
s cripts to inject JavaScript or HTML code that is executed on the client-s ide brows er. This vulnerability is often caus ed by
s erver-s ide s cripts written in languages s uch as PHP, ASP, .NET, Perl or Java, which do not adequately filter data s ent
along with page reques ts or by vulnerable HTTP s ervers . This malicious code appears to come from your Web
application when it runs in the brows er of an uns us pecting us er.
An attacker can do the following damage with an expoloit s cript:
acces s other s ites ins ide another client's private intranet
s teal another client's cookie(s )
modify another client's cookie(s )
s teal another client's s ubmitted form data
modify another client's s ubmitted form data before it reaches the s erver
s ubmit a form to your Web application on the us er's behalf that modifies pas s words or other application data
The two mos t common methods of attack are:
Having a us er click a URL link s ent in an e-mail
Having a us er click a URL link while vis iting a Web s ite
In both s cenarios , the URL will generally link to the trus ted s ite, but will contain additional data that is us ed to trigger the
XSS attack.
Note that SSL connectivity does not protect agains t this is s ue.
Solution:
Fix Cros s Site Scripting Vulnerability
Audit the affected url and other s imilar dynamic pages or s cripts that could be relaying untrus ted malicious data from
the us er input. In general, the following practices s hould be followed while developing dynamic web content:
Explicitly s et the character s et encoding for each page generated by the web s erver
Identify s pecial characters
Encode dynamic output elements
Filter s pecific characters in dynamic elements
Page 5 of 12
Scan Date: 2017-01-16
Examine cookies
For more information on the above practices , read the following CERT advis ory: CERT Advis ory CA-2000-02
For ASP.NET applications , the validateReques t attribute can be added to the page or the web.config. For example:
<%@ Page ... validateRequest="true" %>
OR
<system.web>
<pages validateRequest="true" />
</system.web>
In addition, all dynamic content s hould be HTML encoded us ing HTTPUtility.HTMLEncode.
For PHP applications , input data s hould be validated us ing functions s uch as s trip_tags and utf8_decode. Dynamic
content s hould be HTML encoded us ing htmlentities .
For Perl applications , input data s hould be validated whenever pos s ible us ing regular expres s ions . Dynamic content
s hould be HTML encoded us ing HTML::Entities ::encode or Apache::Util::html_encode (when us ing mod_perl).
Request Header:
POST /login HTTP/1.1 Referer: http://tes thtml5.vulnweb.com Us er-Agent: Mozilla/5.0 (Windows NT 6.1)
AppleWebKit/537.31 (KHTML, like Gecko) Chrome/26.0.1410.64 Safari/537.31 Accept: */* Content-Type:
application/x-www-form-urlencoded Hos t: tes thtml5.vulnweb.com Cookie:
us ername="\"><s CrIpT>alert(391700)</s CrIpT>" Connection: Clos e
us ername="><s CrIpT>alert(391700)</s CrIpT>&pas s word=tes tpas s @1234&s ubmit=Submit
Response Header:
HTTP/1.1 200 OK Connection: clos e Acces s -Control-Allow-Origin: * Content-Length: 6011 Content-Type:
text/html; chars et=utf-8 Date: Mon, 16 Jan 2017 10:21:02 GMT Server: nginx/1.4.1
Response URL:
http://tes thtml5.vulnweb.com/
Result:
Line No:53
Line No:54 Welcom e <b>"><sC rIpT>alert(391700)</sC rIpT></b> | <a href='/logout'>Logout</a>
Line No:55
References:
http://www.us -cert.gov/cas /techalerts /CA-2000-02.html
http://en.wikipedia.org/wiki/Cros s _s ite_s cripting
Alert ID: 481468 Found on: 2017-01-16 Severity: Medium
Form action submits sensitive data in the clear
Open Status: NEW First Found: 2017-01-16
URL: http://tes thtml5.vulnweb.com
Method: POST
Cvss Score: 4.3
Cvss Vector: (AV:N/AC:M/Au:N/C:P/I:N/A:N)
PCI Compliance: Fail
Description:
A web form contains fields with data that is probably s ens itive in nature. This form data is s ubmitted over an unencrypted
connection, which could allow hackers to s niff the network and view the data in plaintext.
Page 6 of 12
Scan Date: 2017-01-16
Solution:
Us e the HTTPS (HTTP over SSL) protocol to s ubmit s ens itive form data
Enable the HTTPS protocol on the s erver. Change the "action" URL of the form tag to us e the HTTPS protocol ("https ://...")
ins tead of jus t the HTTP protocol ("http://..."). All s ens itive data s hould be s ent over HTTPS ins tead of over HTTP.
Request Header:
GET / HTTP/1.1 Hos t: tes thtml5.vulnweb.com Referer: http://tes thtml5.vulnweb.com Us er-Agent: Mozilla/4.0
(compatible; MSIE 7.0; Windows NT 6.1; Trident/4.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET
CLR 3.0.30729; Media Center PC 6.0; MDDS; InfoPath.2; .NET4.0C; .NET4.0E; Tablet PC 2.0)
Result:
Sensitive input transm itted without SSL: password
Alert ID: 481467 Found on: 2017-01-16 Severity: Low
Autocomplete enabled for sensitive HTML form fields
Open Status: NEW First Found: 2017-01-16
URL: http://tes thtml5.vulnweb.com
Method: get
Cvss Score: 4.3
Cvss Vector: (AV:N/AC:M/Au:N/C:P/I:N/A:N)
PCI Compliance: Fail
Description:
The Web form contains pas s words or other s ens itive text fields for which the brows er auto-complete feature is enabled.
Auto-complete s tores completed form field and pas s words locally in the brows er, s o that thes e fields are filled
automatically when the us er vis its the s ite again.
Sens itive data and pas s words can be s tolen if the us er's s ys tem is compromis ed.
Note, however, that form auto-complete is a non-s tandard, brows er-s ide feature that each brows er handles differently.
Opera, for example, dis regards the feature, requiring the us er to enter credentials for each Web s ite vis it.
Solution:
Dis able autocomplete for all s ens itive fields
For each s ens itive field in the HTML, s et the "autocomplete" attribute to "off". For example:
<input type="password" autocomplete="off" name="pw">
If there are many fields , it may be fas ter to s et the "autocomplete" attribute to "off" in the outer <form> tag. For example:
<form action="/login.jsp" autocomplete="off" name="pw">
<input type="password" name="pw">
</form>
Request Header:
GET / HTTP/1.1 Hos t: tes thtml5.vulnweb.com Referer: http://tes thtml5.vulnweb.com Us er-Agent: Mozilla/4.0
(compatible; MSIE 7.0; Windows NT 6.1; Trident/4.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET
CLR 3.0.30729; Media Center PC 6.0; MDDS; InfoPath.2; .NET4.0C; .NET4.0E; Tablet PC 2.0)
Result:
Autocom plete enabled for sensitive form field: password
Alert ID: 481471 Found on: 2017-01-16 Severity: Low
Predictable resource location
Open Status: NEW First Found: 2017-01-16
URL: http://tes thtml5.vulnweb.com/cgi-bin/
Page 7 of 12
Scan Date: 2017-01-16
Method: get
Cvss Score: 6.4
Cvss Vector: (AV:N/AC:L/Au:N/C:P/I:P/A:N)
PCI Compliance: Fail
Description:
Rather than an actual vulnerability, this attack is informational, indicating that acces s to s ome res ource is not granted.
The res ource is predictable and although it is not acces s ible via any URL links in the web application, probing us ing
intelligent brute force methods or commonly us ed res ource names indicates pres ence of the res ource.
Solution:
A cus tom error page s hould be dis played to handle all s uch reques ts .
Request Header:
GET /cgi-bin HTTP/1.1 Referer: http://tes thtml5.vulnweb.com Us er-Agent: Mozilla/5.0 (Windows NT 6.1)
AppleWebKit/537.31 (KHTML, like Gecko) Chrome/26.0.1410.64 Safari/537.31 Accept: */* Hos t:
tes thtml5.vulnweb.com Connection: Clos e
Response Header:
HTTP/1.1 403 Forbidden Connection: clos e Vary: Accept-Encoding Content-Length: 263 Content-Type:
text/html; chars et=is o-8859-1 Date: Mon, 16 Jan 2017 10:21:07 GMT Server: nginx/1.4.1
Result:
http://testhtm l5.vulnweb.com /cgi-bin/
References:
http://projects .webapps ec.org/w/page/13246953/Predictable%20Res ource%20Location
Alert ID: 481473 Found on: 2017-01-16 Severity: Low
Predictable resource location
Open Status: NEW First Found: 2017-01-16
URL: http://tes thtml5.vulnweb.com/cgi-bin
Method: get
Cvss Score: 6.4
Cvss Vector: (AV:N/AC:L/Au:N/C:P/I:P/A:N)
PCI Compliance: Fail
Description:
Rather than an actual vulnerability, this attack is informational, indicating that acces s to s ome res ource is not granted.
The res ource is predictable and although it is not acces s ible via any URL links in the web application, probing us ing
intelligent brute force methods or commonly us ed res ource names indicates pres ence of the res ource.
Solution:
A cus tom error page s hould be dis played to handle all s uch reques ts .
Request Header:
GET /cgi-bin HTTP/1.1 Referer: http://tes thtml5.vulnweb.com Us er-Agent: Mozilla/5.0 (Windows NT 6.1)
AppleWebKit/537.31 (KHTML, like Gecko) Chrome/26.0.1410.64 Safari/537.31 Accept: */* Hos t:
tes thtml5.vulnweb.com Connection: Clos e
Response Header:
HTTP/1.1 403 Forbidden Connection: clos e Vary: Accept-Encoding Content-Length: 263 Content-Type:
text/html; chars et=is o-8859-1 Date: Mon, 16 Jan 2017 10:21:35 GMT Server: nginx/1.4.1
Result:
http://testhtm l5.vulnweb.com /cgi-bin
References:
http://projects .webapps ec.org/w/page/13246953/Predictable%20Res ource%20Location
Page 8 of 12
Scan Date: 2017-01-16
Alert ID: 481474 Found on: 2017-01-16 Severity: Low
Predictable resource location
Open Status: NEW First Found: 2017-01-16
URL: http://tes thtml5.vulnweb.com/s tatic/app/
Method: get
Cvss Score: 6.4
Cvss Vector: (AV:N/AC:L/Au:N/C:P/I:P/A:N)
PCI Compliance: Fail
Description:
Rather than an actual vulnerability, this attack is informational, indicating that acces s to s ome res ource is not granted.
The res ource is predictable and although it is not acces s ible via any URL links in the web application, probing us ing
intelligent brute force methods or commonly us ed res ource names indicates pres ence of the res ource.
Solution:
A cus tom error page s hould be dis played to handle all s uch reques ts .
Request Header:
GET /s tatic/app HTTP/1.1 Referer: http://tes thtml5.vulnweb.com Us er-Agent: Mozilla/5.0 (Windows NT 6.1)
AppleWebKit/537.31 (KHTML, like Gecko) Chrome/26.0.1410.64 Safari/537.31 Accept: */* Hos t:
tes thtml5.vulnweb.com Connection: Clos e
Response Header:
HTTP/1.1 403 Forbidden Connection: clos e Content-Length: 570 Content-Type: text/html Date: Mon, 16 Jan
2017 10:21:39 GMT Server: nginx/1.4.1
Result:
http://testhtm l5.vulnweb.com /static/app/
References:
http://projects .webapps ec.org/w/page/13246953/Predictable%20Res ource%20Location
Alert ID: 481475 Found on: 2017-01-16 Severity: Low
Predictable resource location
Open Status: NEW First Found: 2017-01-16
URL: http://tes thtml5.vulnweb.com/s tatic/cs s /
Method: get
Cvss Score: 6.4
Cvss Vector: (AV:N/AC:L/Au:N/C:P/I:P/A:N)
PCI Compliance: Fail
Description:
Rather than an actual vulnerability, this attack is informational, indicating that acces s to s ome res ource is not granted.
The res ource is predictable and although it is not acces s ible via any URL links in the web application, probing us ing
intelligent brute force methods or commonly us ed res ource names indicates pres ence of the res ource.
Solution:
A cus tom error page s hould be dis played to handle all s uch reques ts .
Request Header:
GET /s tatic/cs s HTTP/1.1 Referer: http://tes thtml5.vulnweb.com Us er-Agent: Mozilla/5.0 (Windows NT 6.1)
AppleWebKit/537.31 (KHTML, like Gecko) Chrome/26.0.1410.64 Safari/537.31 Accept: */* Hos t:
tes thtml5.vulnweb.com Connection: Clos e
Response Header:
Page 9 of 12
Scan Date: 2017-01-16
HTTP/1.1 403 Forbidden Connection: clos e Content-Length: 570 Content-Type: text/html Date: Mon, 16 Jan
2017 10:21:42 GMT Server: nginx/1.4.1
Result:
http://testhtm l5.vulnweb.com /static/css/
References:
http://projects .webapps ec.org/w/page/13246953/Predictable%20Res ource%20Location
Alert ID: 481476 Found on: 2017-01-16 Severity: Low
Predictable resource location
Open Status: NEW First Found: 2017-01-16
URL: http://tes thtml5.vulnweb.com/s tatic/app/libs /
Method: get
Cvss Score: 6.4
Cvss Vector: (AV:N/AC:L/Au:N/C:P/I:P/A:N)
PCI Compliance: Fail
Description:
Rather than an actual vulnerability, this attack is informational, indicating that acces s to s ome res ource is not granted.
The res ource is predictable and although it is not acces s ible via any URL links in the web application, probing us ing
intelligent brute force methods or commonly us ed res ource names indicates pres ence of the res ource.
Solution:
A cus tom error page s hould be dis played to handle all s uch reques ts .
Request Header:
GET /s tatic/app/libs HTTP/1.1 Referer: http://tes thtml5.vulnweb.com Us er-Agent: Mozilla/5.0 (Windows NT
6.1) AppleWebKit/537.31 (KHTML, like Gecko) Chrome/26.0.1410.64 Safari/537.31 Accept: */* Hos t:
tes thtml5.vulnweb.com Connection: Clos e
Response Header:
HTTP/1.1 403 Forbidden Connection: clos e Content-Length: 570 Content-Type: text/html Date: Mon, 16 Jan
2017 10:21:45 GMT Server: nginx/1.4.1
Result:
http://testhtm l5.vulnweb.com /static/app/libs/
References:
http://projects .webapps ec.org/w/page/13246953/Predictable%20Res ource%20Location
Alert ID: 481477 Found on: 2017-01-16 Severity: Low
Predictable resource location
Open Status: NEW First Found: 2017-01-16
URL: http://tes thtml5.vulnweb.com/s tatic/app/controllers /
Method: get
Cvss Score: 6.4
Cvss Vector: (AV:N/AC:L/Au:N/C:P/I:P/A:N)
PCI Compliance: Fail
Description:
Rather than an actual vulnerability, this attack is informational, indicating that acces s to s ome res ource is not granted.
The res ource is predictable and although it is not acces s ible via any URL links in the web application, probing us ing
intelligent brute force methods or commonly us ed res ource names indicates pres ence of the res ource.
Solution:
Page 10 of 12
Scan Date: 2017-01-16
A cus tom error page s hould be dis played to handle all s uch reques ts .
Request Header:
GET /s tatic/app/controllers HTTP/1.1 Referer: http://tes thtml5.vulnweb.com Us er-Agent: Mozilla/5.0
(Windows NT 6.1) AppleWebKit/537.31 (KHTML, like Gecko) Chrome/26.0.1410.64 Safari/537.31 Accept: */*
Hos t: tes thtml5.vulnweb.com Connection: Clos e
Response Header:
HTTP/1.1 403 Forbidden Connection: clos e Content-Length: 570 Content-Type: text/html Date: Mon, 16 Jan
2017 10:21:45 GMT Server: nginx/1.4.1
Result:
http://testhtm l5.vulnweb.com /static/app/controllers/
References:
http://projects .webapps ec.org/w/page/13246953/Predictable%20Res ource%20Location
Alert ID: 481478 Found on: 2017-01-16 Severity: Low
Predictable resource location
Open Status: NEW First Found: 2017-01-16
URL: http://tes thtml5.vulnweb.com/s tatic/app/s ervices /
Method: get
Cvss Score: 6.4
Cvss Vector: (AV:N/AC:L/Au:N/C:P/I:P/A:N)
PCI Compliance: Fail
Description:
Rather than an actual vulnerability, this attack is informational, indicating that acces s to s ome res ource is not granted.
The res ource is predictable and although it is not acces s ible via any URL links in the web application, probing us ing
intelligent brute force methods or commonly us ed res ource names indicates pres ence of the res ource.
Solution:
A cus tom error page s hould be dis played to handle all s uch reques ts .
Request Header:
GET /s tatic/app/s ervices HTTP/1.1 Referer: http://tes thtml5.vulnweb.com Us er-Agent: Mozilla/5.0 (Windows
NT 6.1) AppleWebKit/537.31 (KHTML, like Gecko) Chrome/26.0.1410.64 Safari/537.31 Accept: */* Hos t:
tes thtml5.vulnweb.com Connection: Clos e
Response Header:
HTTP/1.1 403 Forbidden Connection: clos e Content-Length: 570 Content-Type: text/html Date: Mon, 16 Jan
2017 10:21:50 GMT Server: nginx/1.4.1
Result:
http://testhtm l5.vulnweb.com /static/app/services/
References:
http://projects .webapps ec.org/w/page/13246953/Predictable%20Res ource%20Location
Alert ID: 481479 Found on: 2017-01-16 Severity: Low
Predictable resource location
Open Status: NEW First Found: 2017-01-16
URL: http://tes thtml5.vulnweb.com/s tatic/img/
Method: get
Cvss Score: 6.4
Cvss Vector: (AV:N/AC:L/Au:N/C:P/I:P/A:N)
Page 11 of 12
Scan Date: 2017-01-16
Cvss Vector: (AV:N/AC:L/Au:N/C:P/I:P/A:N)
PCI Compliance: Fail
Description:
Rather than an actual vulnerability, this attack is informational, indicating that acces s to s ome res ource is not granted.
The res ource is predictable and although it is not acces s ible via any URL links in the web application, probing us ing
intelligent brute force methods or commonly us ed res ource names indicates pres ence of the res ource.
Solution:
A cus tom error page s hould be dis played to handle all s uch reques ts .
Request Header:
GET /s tatic/img HTTP/1.1 Referer: http://tes thtml5.vulnweb.com Us er-Agent: Mozilla/5.0 (Windows NT 6.1)
AppleWebKit/537.31 (KHTML, like Gecko) Chrome/26.0.1410.64 Safari/537.31 Accept: */* Hos t:
tes thtml5.vulnweb.com Connection: Clos e
Response Header:
HTTP/1.1 403 Forbidden Connection: clos e Content-Length: 570 Content-Type: text/html Date: Mon, 16 Jan
2017 10:21:52 GMT Server: nginx/1.4.1
Result:
http://testhtm l5.vulnweb.com /static/im g/
References:
http://projects .webapps ec.org/w/page/13246953/Predictable%20Res ource%20Location
Alert ID: 481469 Found on: 2017-01-16 Severity: Info
Web server version disclosure
Open Status: NEW First Found: 2017-01-16
URL: http://tes thtml5.vulnweb.com/Cros s domain.xml
Method: get
Cvss Base: 1.0
Cvss Score: 1.0
PCI Compliance: Pas s
Description:
HTTP web s erver information is dis clos ed in HTTP headers . This information may revel s oftware name, vers ion etc. It may
help an attacker to look for s pecific web s erver vers ion related vulnerabilities .
Solution:
Vers ions and types information s hould be omitted where pos s ible.
Request Header:
GET /Cros s domain.xml HTTP/1.1 Referer: http://tes thtml5.vulnweb.com Us er-Agent: Mozilla/5.0 (Windows
NT 6.1) AppleWebKit/537.31 (KHTML, like Gecko) Chrome/26.0.1410.64 Safari/537.31 Accept: */* Hos t:
tes thtml5.vulnweb.com Connection: Clos e
Response Header:
HTTP/1.1 404 NotFound Connection: clos e Content-Length: 238 Content-Type: text/html Date: Mon, 16 Jan
2017 10:20:56 GMT Server: nginx/1.4.1
Result:
nginx/1.4.1
References:
http://os vdb.org/91
Page 12 of 12
Scan Date: 2017-01-16
Potrebbero piacerti anche
- Security Sample VAPT ReportDocumento28 pagineSecurity Sample VAPT ReportRavi GiriNessuna valutazione finora
- Web Vulnerability ReportDocumento7 pagineWeb Vulnerability ReporthitcaNessuna valutazione finora
- Vuln ScanDocumento12 pagineVuln ScanBrijendra Pratap SinghNessuna valutazione finora
- Website Vulnerability Scanner Report (Light)Documento4 pagineWebsite Vulnerability Scanner Report (Light)MasBaNessuna valutazione finora
- Web Application Defender's Cookbook: Battling Hackers and Protecting UsersDa EverandWeb Application Defender's Cookbook: Battling Hackers and Protecting UsersNessuna valutazione finora
- Snyk Top 10: Code Vulnerabilities in 2022Documento6 pagineSnyk Top 10: Code Vulnerabilities in 2022gavam63877Nessuna valutazione finora
- Astra Security Sample VAPT ReportDocumento28 pagineAstra Security Sample VAPT Reporthanuman1999Nessuna valutazione finora
- Astra Security - Sample Report For VAPTDocumento30 pagineAstra Security - Sample Report For VAPTIndian OpinionNessuna valutazione finora
- PentestTools WebsiteScanner ReportDocumento5 paginePentestTools WebsiteScanner ReportmiguelNessuna valutazione finora
- Comprehensive Report: Acunetix Threat Level 3Documento38 pagineComprehensive Report: Acunetix Threat Level 3Yudha Trias RusmanaNessuna valutazione finora
- PentestTools WebsiteScanner ReportDocumento4 paginePentestTools WebsiteScanner Reportcatalina nicolinNessuna valutazione finora
- ZAP Scanning: Project 2Documento24 pagineZAP Scanning: Project 2Sabyasachi duttaNessuna valutazione finora
- Web Application Penetration Testing Report of Juice ShopDocumento15 pagineWeb Application Penetration Testing Report of Juice ShopPavan Reddy50% (2)
- Website Vulnerability Scanner Report (Light)Documento5 pagineWebsite Vulnerability Scanner Report (Light)Ilija DodevskiNessuna valutazione finora
- Website Vulnerability Scanner Report (Light)Documento6 pagineWebsite Vulnerability Scanner Report (Light)Stevi NangonNessuna valutazione finora
- Sample Report WebDocumento19 pagineSample Report WebMuhammad AwaisNessuna valutazione finora
- 10a - Web SecurityDocumento14 pagine10a - Web SecurityAlif FaisalNessuna valutazione finora
- Website Vulnerability Scanner Report (Light)Documento6 pagineWebsite Vulnerability Scanner Report (Light)alex681219Nessuna valutazione finora
- ZAP Scanning Report: Site: Https://webapps - Bps.go - IdDocumento4 pagineZAP Scanning Report: Site: Https://webapps - Bps.go - Idyoga_wpNessuna valutazione finora
- ETHICAL HACKING GUIDE-Part 3: Comprehensive Guide to Ethical Hacking worldDa EverandETHICAL HACKING GUIDE-Part 3: Comprehensive Guide to Ethical Hacking worldNessuna valutazione finora
- Static Detection of Cross-Site Scripting VulnerabilitiesDocumento10 pagineStatic Detection of Cross-Site Scripting VulnerabilitiesLeo LopezNessuna valutazione finora
- Delhi Ford 1Documento18 pagineDelhi Ford 1Vivek GautamNessuna valutazione finora
- PentestTools WebsiteScanner ReportDocumento5 paginePentestTools WebsiteScanner ReportSunil Kumar SharmaNessuna valutazione finora
- PentestTools WebsiteScanner ReportDocumento7 paginePentestTools WebsiteScanner ReportMauricio CerratoNessuna valutazione finora
- Comprehensive Report: Acunetix Threat Level 3Documento37 pagineComprehensive Report: Acunetix Threat Level 3Yudha Trias RusmanaNessuna valutazione finora
- Report For Foophones: by Utkarsh MunraDocumento37 pagineReport For Foophones: by Utkarsh Munrasuraj fbNessuna valutazione finora
- Lab Fat: CSE3501 Information Security Analysis and AuditDocumento21 pagineLab Fat: CSE3501 Information Security Analysis and AuditSona SharmaNessuna valutazione finora
- Detailed Scan ReportDocumento23 pagineDetailed Scan ReportAnas YogieNessuna valutazione finora
- WebStrike PDF ReportDocumento4 pagineWebStrike PDF ReportBiswajitNessuna valutazione finora
- Security+ 601 Test 2Documento61 pagineSecurity+ 601 Test 2Kalen StarNessuna valutazione finora
- Cargill Web Application Scanning ReportDocumento27 pagineCargill Web Application Scanning ReportHari KingNessuna valutazione finora
- Website Vulnerability Scanner Report (Light)Documento5 pagineWebsite Vulnerability Scanner Report (Light)Muhammad LuludNessuna valutazione finora
- ReportDocumento22 pagineReportappu12245Nessuna valutazione finora
- 2011 IEEE Symposium On Security and Privacy 2011 IEEE Symposium On Security and PrivacyDocumento9 pagine2011 IEEE Symposium On Security and Privacy 2011 IEEE Symposium On Security and PrivacyRahul PaulNessuna valutazione finora
- Developer Report: Acunetix Website Audit 23 December, 2021Documento7 pagineDeveloper Report: Acunetix Website Audit 23 December, 2021BAGAS TRI RAMADANA -Nessuna valutazione finora
- Vulnerability Report Https Enam - Gov.in May 2023Documento31 pagineVulnerability Report Https Enam - Gov.in May 2023project.adminNessuna valutazione finora
- PentestTools WebsiteScanner ReportDocumento4 paginePentestTools WebsiteScanner ReportdeldengcNessuna valutazione finora
- 1705 09044 PDFDocumento7 pagine1705 09044 PDFtradofNessuna valutazione finora
- Scor 350-701-V6Documento135 pagineScor 350-701-V6adebangaNessuna valutazione finora
- Owasp Top 10Documento41 pagineOwasp Top 10Nebula BotsNessuna valutazione finora
- Analyzing Web TrafficDocumento16 pagineAnalyzing Web TraffichugocelaNessuna valutazione finora
- Developer ReportDocumento7 pagineDeveloper ReportRaheelNessuna valutazione finora
- Assignment No 4Documento18 pagineAssignment No 4Jusil T. GaiteNessuna valutazione finora
- Va PT ReportDocumento16 pagineVa PT ReportRobinNessuna valutazione finora
- Scan Session Summary: Web Application Security ReportDocumento13 pagineScan Session Summary: Web Application Security ReportMondher GamNessuna valutazione finora
- Practical Risk Analysis and Threat Modeling v.1.0Documento85 paginePractical Risk Analysis and Threat Modeling v.1.0Nayana SavalaNessuna valutazione finora
- With Emphasis On Web Applications Security Related IssuesDocumento28 pagineWith Emphasis On Web Applications Security Related IssuesFsohailNessuna valutazione finora
- Developer Report PDFDocumento65 pagineDeveloper Report PDFAnonymous JyKPfbZBQNessuna valutazione finora
- HTML5 Security Cheat SheetDocumento7 pagineHTML5 Security Cheat SheetNikolaMilosevicNessuna valutazione finora
- Web Security Interview QuestionDocumento34 pagineWeb Security Interview Questionarunika palNessuna valutazione finora
- Web Security Interview QuestionDocumento8 pagineWeb Security Interview Questionvenkat1034Nessuna valutazione finora
- XSS Attacks and Defenses: John MitchellDocumento44 pagineXSS Attacks and Defenses: John MitchellHanef SamsudinNessuna valutazione finora
- Suip - Biz: Localbitcoins Vds Donation FeedbackDocumento1 paginaSuip - Biz: Localbitcoins Vds Donation Feedbackryo020288Nessuna valutazione finora
- Validating SSL Certificates in Non-Browser SoftwareDocumento12 pagineValidating SSL Certificates in Non-Browser SoftwareJohnny AlexNessuna valutazione finora
- 1 - Threat Modeling ReportDocumento4 pagine1 - Threat Modeling ReportSagar SaklaniNessuna valutazione finora
- WebApp ReportDocumento9 pagineWebApp ReportRavi GiriNessuna valutazione finora
- Passive Reflective Active: DistributiveDocumento7 paginePassive Reflective Active: DistributiveAnkur RajputNessuna valutazione finora
- XSS ScriptingDocumento3 pagineXSS Scriptingchrispapantoniou4828Nessuna valutazione finora
- Report Web AuditDocumento17 pagineReport Web Auditanupprakash36Nessuna valutazione finora
- Frequently Asked Questions: Reminder Notifications', and Send Notifications For Purchasing DocumentsDocumento2 pagineFrequently Asked Questions: Reminder Notifications', and Send Notifications For Purchasing DocumentsNadipalliNessuna valutazione finora
- Banana KongDocumento4 pagineBanana KongDuke TogoNessuna valutazione finora
- Bail Bonds Costa Mesa Goog 230208 C US L en A9P1AS GMWDocumento726 pagineBail Bonds Costa Mesa Goog 230208 C US L en A9P1AS GMWAlexNessuna valutazione finora
- Florin Olariu: "Alexandru Ioan Cuza", University of Iași Department of Computer ScienceDocumento117 pagineFlorin Olariu: "Alexandru Ioan Cuza", University of Iași Department of Computer ScienceGigi FloricaNessuna valutazione finora
- MSQL For Pentester - Nmap - 1Documento9 pagineMSQL For Pentester - Nmap - 1huskybroyi.vo.j.1.1.04Nessuna valutazione finora
- Nessus ScriptDocumento1 paginaNessus Scriptapi-385391462Nessuna valutazione finora
- Developing Android Apps On Ubuntu: Executive SummaryDocumento17 pagineDeveloping Android Apps On Ubuntu: Executive SummaryRohman FathoniNessuna valutazione finora
- Siebel Web ServicesDocumento20 pagineSiebel Web Servicesyomero1986Nessuna valutazione finora
- Issues ORA 0054 Resource BusyDocumento5 pagineIssues ORA 0054 Resource BusymyworldmyrulesNessuna valutazione finora
- ControlsFX FeaturesDocumento22 pagineControlsFX Featurespradhan.neeladriNessuna valutazione finora
- Software Design SpecificationDocumento2 pagineSoftware Design Specificationragamenon100% (1)
- HackpageDocumento5 pagineHackpagekarthikNessuna valutazione finora
- Geovision Diagnosis Local-ErrorMessageDocumento2 pagineGeovision Diagnosis Local-ErrorMessage2j88Nessuna valutazione finora
- A Project Report On Online Banking SolutionDocumento75 pagineA Project Report On Online Banking Solutionadiall4u0% (2)
- Event Driven Programming in VB Net PDFDocumento2 pagineEvent Driven Programming in VB Net PDFHolly100% (1)
- On Object Detection Using YOLODocumento17 pagineOn Object Detection Using YOLOSukanya N100% (1)
- Plant Maintenance and Sales and Distribution TablesDocumento4 paginePlant Maintenance and Sales and Distribution Tablesjuan_saavedra_18Nessuna valutazione finora
- TAF J With Jboss Browser and DebuggingDocumento9 pagineTAF J With Jboss Browser and DebuggingsajibarafatsiddiquiNessuna valutazione finora
- Spring IOC Container Class NotesDocumento16 pagineSpring IOC Container Class NotesHoussam Edine El jazouliNessuna valutazione finora
- Arcgis Desktop Tips (1) - EsriDocumento10 pagineArcgis Desktop Tips (1) - EsriSyiro MarsyikidNessuna valutazione finora
- Lab1 HPDocumento9 pagineLab1 HPVictor Hugo Garay SaezNessuna valutazione finora
- Linux Booting ProcessDocumento18 pagineLinux Booting ProcessPrashant RawatNessuna valutazione finora
- اساسيات تكنولوجيا المعلومات للمدققين الداخليينDocumento66 pagineاساسيات تكنولوجيا المعلومات للمدققين الداخليينmodi4ukNessuna valutazione finora
- Logix Ap007b en PDocumento56 pagineLogix Ap007b en PRoyal Ritesh SharmaNessuna valutazione finora
- Mentor Graphics Corporation, Graphical Editors User Manual, Release v2018.2Documento578 pagineMentor Graphics Corporation, Graphical Editors User Manual, Release v2018.2dupipiNessuna valutazione finora
- Vcp-Practice Test 1 Simulator 1Documento60 pagineVcp-Practice Test 1 Simulator 1SkillTrầnNessuna valutazione finora
- Data Flow Diagram Opening A New Room: CustomerDocumento5 pagineData Flow Diagram Opening A New Room: CustomerAyushNessuna valutazione finora
- Javascript - How To Change Css Style in Typescript - Stack OverflowDocumento2 pagineJavascript - How To Change Css Style in Typescript - Stack OverflowIlhan KalačNessuna valutazione finora
- How To Upload Your AssignmentDocumento9 pagineHow To Upload Your AssignmentMd Ashiqul Hoq AbdullahNessuna valutazione finora
- BKP 101 SVMDocumento8 pagineBKP 101 SVMMohamad Nadzri YahayaNessuna valutazione finora