Documenti di Didattica
Documenti di Professioni
Documenti di Cultura
Cyber Crime - Few Challenges and Their Solution
Caricato da
Muzhgan Athaee0 valutazioniIl 0% ha trovato utile questo documento (0 voti)
25 visualizzazioni3 pagineTitolo originale
Cyber Crime -- Few challenges and their solution
Copyright
© © All Rights Reserved
Formati disponibili
DOCX, PDF, TXT o leggi online da Scribd
Condividi questo documento
Condividi o incorpora il documento
Hai trovato utile questo documento?
Questo contenuto è inappropriato?
Segnala questo documentoCopyright:
© All Rights Reserved
Formati disponibili
Scarica in formato DOCX, PDF, TXT o leggi online su Scribd
0 valutazioniIl 0% ha trovato utile questo documento (0 voti)
25 visualizzazioni3 pagineCyber Crime - Few Challenges and Their Solution
Caricato da
Muzhgan AthaeeCopyright:
© All Rights Reserved
Formati disponibili
Scarica in formato DOCX, PDF, TXT o leggi online su Scribd
Sei sulla pagina 1di 3
Few challenges that the technology space faces in cyber security are the
following:
Digital Data Threat: Growing online transactions generate bigger incentives
for cybercriminals. Besides, establishments looking to mine data—for
instance, customer information, results of product surveys, and generic
market information—create treasured intellectual property that is in itself
an attractive target.
Supply Chain Inter-connection: The supply chains are increasingly
interconnected. Companies are urging vendors and customers to join their
networks. This makes a company’s security wall thin.
Hacking: This action is penetrating into someone’s system in unauthorized
fashion to steal or destroy data, which has grown hundred folds in the past
few years. The availability of information online makes it easier for even
non-technical people to perform hacking.
Phishing: The easiest to execute and can produce the results with very little
effort. It is the act of sending out Fake emails, text messages and create
websites to look like they're from authentic companies.
The following suggestions are recommended as
solution to the above challenges:
1. Net Security be tightened up
2. Use of Encryption Technology
3. Intrusion Management(IDS)
An intrusion detection system (IDS) is a device or software
application that monitors a network or systems for malicious activity or
policy violations. Any malicious activity or violation is typically
reported either to an administrator or collected centrally using
a security information and event management (SIEM) system. A SIEM
system combines outputs from multiple sources, and uses alarm
filtering techniques to distinguish malicious activity from false alarms.
4. False E-mail identity registration be treated as an offence
5. Use of Voice-recognizer, Filter Software and Caller ID for Protection
against Unauthorized Access
6. Development of Cyber Forensics and Biometric Techniques
7. Need to establish a Computer Crime Research and Development
Centre.
8. Need for a Universal Legal Regulatory Mechanism
9. Global Code of Digital Law for resolving Intellectual Property Rights
related disputes
10. Need for Universalization of Cyber Law
11. Interpol and Emergency Response Computer Security Team
12. Special Cyber Crime Investigation Cell for Hi-Tech Crimes
13. E-Judiciary and Video-Conferencing for Speedy Justice
14. Need for Cyber Crime Reporter or Cyber Law Journal
15. The Information Technology (Amendment) Act, 2008 – A Step in the
right direction
16. Establishment of Special Cyber Courts to try Cyber Crimes
17. Diffusion of Internet Technology in India
18. Technical Means for Blocking of Errant Websites
19. Planting of Baits in Cyberspace for Worms and Viruses
20. Regulation of Social Networking Sites
21. Decentralization of the National Informatics Centre
22. Appointments under the IT Act, 2000: Fair, Transparent and Speedy
23. Need for Increased Awareness among Victims of Cyber Crimes
24. Need for Imparting Training to Officials to Investigate Cyber Crimes
25. Need for connecting Cyber Cafes with Police Control Rooms
26. Periodical reviewing of licenses of Internet Service Providers (ISPs)
27. Need for Development of Anti-hijacking Software
28. Encouragement of Cyber Crime Victims to Lodge Complaints
29. Need for Modernization of Existing Laws and Enactment of New Laws
30. Digital timestamping
The main feature of digital time stamping is to
eliminate the possibility of forging the time of creation e.g. by
modifying the system clock of the machine used for signing.
Why it is needed We often need to prove when a piece of data (text,
document, music, art or database) was created or last modified. Areas
that need this could be : E-commerce, patent issues, betting, archiving,
journaling and when the author signs the record or when someone
approved it, or consented to it.
Potrebbero piacerti anche
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryDa EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryValutazione: 3.5 su 5 stelle3.5/5 (231)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)Da EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Valutazione: 4.5 su 5 stelle4.5/5 (120)
- Grit: The Power of Passion and PerseveranceDa EverandGrit: The Power of Passion and PerseveranceValutazione: 4 su 5 stelle4/5 (588)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaDa EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaValutazione: 4.5 su 5 stelle4.5/5 (266)
- The Little Book of Hygge: Danish Secrets to Happy LivingDa EverandThe Little Book of Hygge: Danish Secrets to Happy LivingValutazione: 3.5 su 5 stelle3.5/5 (399)
- Never Split the Difference: Negotiating As If Your Life Depended On ItDa EverandNever Split the Difference: Negotiating As If Your Life Depended On ItValutazione: 4.5 su 5 stelle4.5/5 (838)
- Shoe Dog: A Memoir by the Creator of NikeDa EverandShoe Dog: A Memoir by the Creator of NikeValutazione: 4.5 su 5 stelle4.5/5 (537)
- The Emperor of All Maladies: A Biography of CancerDa EverandThe Emperor of All Maladies: A Biography of CancerValutazione: 4.5 su 5 stelle4.5/5 (271)
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeDa EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeValutazione: 4 su 5 stelle4/5 (5794)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyDa EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyValutazione: 3.5 su 5 stelle3.5/5 (2259)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersDa EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersValutazione: 4.5 su 5 stelle4.5/5 (344)
- Team of Rivals: The Political Genius of Abraham LincolnDa EverandTeam of Rivals: The Political Genius of Abraham LincolnValutazione: 4.5 su 5 stelle4.5/5 (234)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreDa EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreValutazione: 4 su 5 stelle4/5 (1090)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceDa EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceValutazione: 4 su 5 stelle4/5 (895)
- Her Body and Other Parties: StoriesDa EverandHer Body and Other Parties: StoriesValutazione: 4 su 5 stelle4/5 (821)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureDa EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureValutazione: 4.5 su 5 stelle4.5/5 (474)
- The Unwinding: An Inner History of the New AmericaDa EverandThe Unwinding: An Inner History of the New AmericaValutazione: 4 su 5 stelle4/5 (45)
- Eleven Thousand Five Hundred Pesos (P11, 500.00)Documento2 pagineEleven Thousand Five Hundred Pesos (P11, 500.00)bhem silverio100% (4)
- The Yellow House: A Memoir (2019 National Book Award Winner)Da EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Valutazione: 4 su 5 stelle4/5 (98)
- On Fire: The (Burning) Case for a Green New DealDa EverandOn Fire: The (Burning) Case for a Green New DealValutazione: 4 su 5 stelle4/5 (73)
- First MassDocumento28 pagineFirst Masstrixie lavigne65% (23)
- Britain and The Resistance in Occupied YugoslaviaDocumento29 pagineBritain and The Resistance in Occupied YugoslaviaMarko Cvarak100% (1)
- Legal Separation - Grounds For DenialDocumento5 pagineLegal Separation - Grounds For DenialAnonymous o9q5eawTNessuna valutazione finora
- 6 Kalimas of Islam With English TranslationDocumento5 pagine6 Kalimas of Islam With English TranslationAfaz RahmanNessuna valutazione finora
- China Signposts: A Practical Guide For Multinationals in 2022Documento16 pagineChina Signposts: A Practical Guide For Multinationals in 2022APCO WorldwideNessuna valutazione finora
- Configuration of VIO On Power6 PDFDocumento39 pagineConfiguration of VIO On Power6 PDFchengabNessuna valutazione finora
- Week 4, 5, 6 Adjustments and Financial Statement Prep - ClosingDocumento61 pagineWeek 4, 5, 6 Adjustments and Financial Statement Prep - ClosingAarya SharmaNessuna valutazione finora
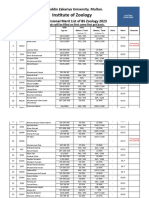
- 5953-6th Merit List BS Zool 31-8-2023Documento22 pagine5953-6th Merit List BS Zool 31-8-2023Muhammad AttiqNessuna valutazione finora
- 1st Indorsement RYAN SIMBULAN DAYRITDocumento8 pagine1st Indorsement RYAN SIMBULAN DAYRITAnna Camille TadeoNessuna valutazione finora
- Special Topics in Income TaxationDocumento78 pagineSpecial Topics in Income TaxationPantas DiwaNessuna valutazione finora
- Biotech Bo SeriesDocumento2 pagineBiotech Bo SeriesArlinda Friyanti CallistaNessuna valutazione finora
- Dasa SandhiDocumento1 paginaDasa SandhishivasudhakarNessuna valutazione finora
- Frontier Fiesta Association Scholarships: University of Houston Incoming FreshmanDocumento1 paginaFrontier Fiesta Association Scholarships: University of Houston Incoming Freshmanapi-269999191Nessuna valutazione finora
- Aff of Admission of Paternity GalacioDocumento1 paginaAff of Admission of Paternity GalacioAlfie OmegaNessuna valutazione finora
- Case Study Analysis-BusinessEthicsDilemmaDocumento1 paginaCase Study Analysis-BusinessEthicsDilemmaMeg CariñoNessuna valutazione finora
- ASME - Lessens Learned - MT or PT at Weld Joint Preparation and The Outside Peripheral Edge of The Flat Plate After WDocumento17 pagineASME - Lessens Learned - MT or PT at Weld Joint Preparation and The Outside Peripheral Edge of The Flat Plate After Wpranav.kunte3312Nessuna valutazione finora
- Homework For Non Current Assets Held For SaleDocumento2 pagineHomework For Non Current Assets Held For Salesebosiso mokuliNessuna valutazione finora
- Prom 2015: The Great GatsbyDocumento14 pagineProm 2015: The Great GatsbyMaple Lake MessengerNessuna valutazione finora
- FM Cia 3Documento14 pagineFM Cia 3MOHAMMED SHAHIDNessuna valutazione finora
- Tax Invoice/Bill of Supply/Cash Memo: (Original For Recipient)Documento1 paginaTax Invoice/Bill of Supply/Cash Memo: (Original For Recipient)MelbinGeorgeNessuna valutazione finora
- CPC Foriegn JudgmentDocumento13 pagineCPC Foriegn JudgmentmehakNessuna valutazione finora
- Ivory L. Haislip v. Attorney General, State of Kansas and Raymond Roberts, 992 F.2d 1085, 10th Cir. (1993)Documento5 pagineIvory L. Haislip v. Attorney General, State of Kansas and Raymond Roberts, 992 F.2d 1085, 10th Cir. (1993)Scribd Government DocsNessuna valutazione finora
- WWRPL Oct-19Documento12 pagineWWRPL Oct-19Sanjay KumarNessuna valutazione finora
- First Church of Seventh-Day Adventists Weekly Bulletin (Spring 2013)Documento12 pagineFirst Church of Seventh-Day Adventists Weekly Bulletin (Spring 2013)First Church of Seventh-day AdventistsNessuna valutazione finora
- Ficha Tecnica Gato Big Red 30tonDocumento16 pagineFicha Tecnica Gato Big Red 30tonCesar Augusto Arias CastroNessuna valutazione finora
- Pastor Bonus Seminary: Fr. Ramon Barua, S.J. Street, Tetuan, P.O. Box 15 7000 Zamboanga City PhilippinesDocumento2 paginePastor Bonus Seminary: Fr. Ramon Barua, S.J. Street, Tetuan, P.O. Box 15 7000 Zamboanga City PhilippinesJeremiah Marvin ChuaNessuna valutazione finora
- Motion For Preliminary InjunctionDocumento4 pagineMotion For Preliminary InjunctionElliott SchuchardtNessuna valutazione finora
- NEW GL Archiving of Totals and DocumentsDocumento5 pagineNEW GL Archiving of Totals and Documentsantonio xavierNessuna valutazione finora
- Chapter Eight Cross-National Cooperation and Agreements: ObjectivesDocumento13 pagineChapter Eight Cross-National Cooperation and Agreements: ObjectivesSohni HeerNessuna valutazione finora