Documenti di Didattica
Documenti di Professioni
Documenti di Cultura
Content Filtering On Social Networking S PDF
Caricato da
smael bantiyanTitolo originale
Copyright
Formati disponibili
Condividi questo documento
Condividi o incorpora il documento
Hai trovato utile questo documento?
Questo contenuto è inappropriato?
Segnala questo documentoCopyright:
Formati disponibili
Content Filtering On Social Networking S PDF
Caricato da
smael bantiyanCopyright:
Formati disponibili
ISSN 2278-3091
Volume 2, No.6, November - December 2013
G.N.Purohit. et al.,International Journal of Advanced Trends in Computer Science and Engineering, 2(6), November-December 2013, 119-121
International Journal of Advanced Trends in Computer Science and Engineering
Available Online at http://warse.org/pdfs/2013/ijatcse01262013.pdf
CONTENT FILTERING ON SOCIAL NETWORKING SITES
Prof. G.N.Purohit (Dean, AIM &ACT), Banasthali University, Jaipur, Rajasthan, gn_purohitjaipur@yahoo.co.in
Dr. Priti Singh (HOD, ECE), Amity University, Gurgaon, Haryana, psingh@ggn.amity.edu
Mrs. Praveen Dangi (Ph.D*), Banasthali University, Jaipur, Rajasthan, praveenchoudhary09@gmail.com
ABSTRACT There are also many potential threats to privacy associated
with these SNS such as identity theft and disclosure of
A social networking service is a platform to build social sensitive information. However, many users still are not
networks or social relations among people. A social aware of these threats and the privacy settings provided by
network service consists of a representation of each user SNS are not flexible enough to protect user’s data. In
(often a profile), his/her social links, and a variety of addition, users do not have any control over what others
additional services. Most social network services are web- reveal about them. Privacy concerns with social
based and provide means for users to interact over networking services have been raised growing concerns
the Internet. Online community services are sometimes amongst users on the dangers of giving out too much
considered as a social network service, though in a broader personal information. In addition, there is a perceived
sense, social network service usually means an individual- privacy threat in relation to placing too much personal
centered service whereas online community services are information in the hands of large corporations or
group-centered. Web-based social networking services governmental bodies, allowing a profile to be produced on
make it possible to connect people who share interests and an individual's behavior on which decisions, detrimental to
activities across political, economic, and geographic an individual, may be taken.
borders.
This paper presents the security risks of online social Privacy on Social Networking sites can be undermined by
media networking system. many factors. For example, users may disclose personal
information, sites may not take adequate steps to protect
user privacy, and third parties frequently use information
Key Words : Vulnerability, Social Networking Sites, posted on social networks for a variety of purposes. Users
Security, Privacy. also provide security for Image Filtering. When an image
is acquired by a camera or other imaging system, often the
vision system for which it is intended is unable to use it
I. INTRODUCTION directly. The image may be corrupted by random
The Social Networking Sites (SNS) are gaining a lot of variations in intensity, variations in illumination, or poor
popularity these days with almost all of the educated youth contrast.
using one or the other such site. Filtering: transform pixel intensity values to reveal certain
image characteristics
These have played a crucial role in bridging boundaries Enhancement: improves contrast
and crossing the seas and enabling them to communicate Smoothing: remove noises
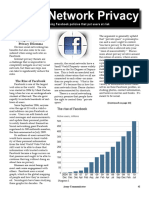
on a common platform. Figure 1 shows Social Networking Template matching: detects known patterns
websites are often designed to fit a certain type
of community such as the college community being For the Next generation, social networking sites have
mirrored by Facebook.com. become the preferred forum for social interactions, from
posturing and role playing to simply sounding off.
However, because such forums are relatively easy to
access, posted content can be reviewed by anyone with an
interest in the users' personal information.
2. CHARACTERSTICS OF SOCIAL NETWORKING
SITES
Social networking websites provide rich information about
the person and his network, which can be utilized for
various business purposes. Some of the main
characteristics of social networking sites are:
Figure 1. Social Networking Sites
119
G.N.Purohit. et al.,International Journal of Advanced Trends in Computer Science and Engineering, 2(6), November-December 2013, 119-121
They act as a resource for advertisers to promote ‘settings’ link in the top right hand corner of the website’s
their brands through word-of-mouth to targeted home page. Moreover, only 10 percent of user profiles on
customers. friendster.com accessed during our study had altered the
They promote the use of embedded privacy settings to prevent us from contacting these users,
advertisements in online videos. thus supporting our conclusion that access of privacy
Users can play games, take fun quizzes, share settings is relatively unclear.
photos and ideas with friends in social
networking sites.
3. OBJECTIVE
The basic objective of this research is to study the
vulnerability of social networking sites with respect to
security for image filtering, emails and Web Browser. Figure 2. Vague Privacy Setting
Further, the default privacy settings are not very
restricting, allowing third parties to message users and
4. SOCIAL NETWORKING SITES
view their information in the absence of privacy
awareness. It is also unclear as to which default settings
4.1. Facebook
should be altered in order to fully prevent this invasion of
privacy to occur.
In Face book, the users can easily access links to either log
out, access the home page, or alter their privacy settings.
Thus, users are typically aware that privacy settings can be
altered because the privacy settings link is highly visible. 5. MINIMIZING VULNERABILITY OF SOCIAL
Once inside the privacy settings page, a user is given NETWORKING SITES
simple options in drop down menus that guide the user into
choosing the desired privacy settings. A user must be part Every user on a social networking site can choose to reveal
of a specific network (e.g. college, high school, city, their personal information using a range of attributes. We
organization, etc.) in order to browse / search the divide these attributes into two sets, individual and
individuals that are a part of that network. Easy access to community attributes. Individual attributes (I-attributes)
the privacy link, the straight forward ability to change characterize individual user information, including
one’s privacy settings, and the limited ability to globally personal information such as gender, birthdate, phone
search are all positive aspects that help guard users’ number, home address, group memberships, etc.
information from users in other networks. Facebook.com Community attributes (C-attributes) characterize
was launched in 2004 with the intent to connect U.S. information about friends of a user, including friends that
college students, starting with Harvard College. In its first are traceable from a user's profile (i.e., user's friend list),
month, over half of the 19,500 students signed up. After tagged pictures, wall interactions, etc. These attributes are
gaining popularity, Face book opened its registration to always accessible to friends but may not to the other users.
non-college students, and in 2008, Face book surpassed A user vulnerability depends on visibility and exposure of
MySpace as the leading social networking website. a user profile through not only attributes setting but also
his friends.
4.2. Myspace.com 5.1. Individual Attributes
Myspace.com offers similar privacy setting restrictions as Individual Attributes includes personal information or user
Facebook.com, the web site has a more ambiguous privacy information such as birth date, phone number or any other
settings link that is less obvious for users to access. As information. But if the user can use these information to
seen in the pictures to the left, there is no word ‘privacy’ secure their account then the vulnerable friend can easily
anywhere on the homepage. The link ‘account settings’ hack their account, because these are very common things
sends the user to another page with the link “privacy that vulnerable friend and any other person can easily
settings.” Myspace.com does allow users to change their know user birthday, phone number, address, so the user
settings, but it is not user friendly. can use some discrete things so that no one can easily find
out or hack other user account and that should be secure or
4.3. Frienster.com minimizes vulnerability.
Users can only alter the default privacy settings(Figure 2)
of this online social networking by clicking the obscure
120
G.N.Purohit. et al.,International Journal of Advanced Trends in Computer Science and Engineering, 2(6), November-December 2013, 119-121
5.2. Community Attributes [6].Hak J. Kim. Online Social Media Networking and Assessing Its
Security Risks, International Journal of Security and Its
Applications Vol. 6, No. 3, July, 2012.
Community Attributes characterize information about [7]. Rosenblum, D. What Anyone Can Know: The Privacy Risks of
friend and also including those friends who are in user’s Social Networking Sites, IEEE Security and Privacy, Vol. 5,Issue 3,
friend list. They trace their information, pictures, and also pp. 40-49, 2007.
wall interactions. Vulnerable friend can easily hack other [8]. Ellison, N.B; Steinfield, C; & Lampe, C. The benefits of Face book
"friends:" Social capital and college students' use of online social
people information. The information you post on the
network sites, Journal of Computer-Mediated Communication.Vol
Internet is available to almost anyone who is clever enough 12, Issue 4, 2007.
to access it. Most thieves need just a few vital pieces of [9].Boyd, D; & Ellison, N. B. (2008). Social network sites: Definition,
personal information to make your life a nightmare and if history and scholarship. Journal of Computer--Mediated
they successfully steal your identity. So to minimize this Communication, Vol 13, Issue 1, pp. 210--230.
vulnerability, user and who are in user’s friend list provide [10].E-Mediat. Privacy, social media policy
some security so that another people who are not user ,http://www.bethkanter.org/privacy-security/
friend can’t see or open their data. [11]. Aboulhamid, M; Sevillano, J. Computer Systems and
Applications, IEEE/ACS International Conference on Computer
Systems and Applications, Vol 4, Issue 2, 2009.
[12].Luo, W; Xie, Q; and Hengartner. Facecloak, privacy technique for
6. CONCLUSION social networking sites , IEEE International Conference on Privacy,
Security, Risk and Trust. , pp.26-33, 2009.
Social networking websites is also one of the social media [13]. Jones, S; O'Neill, E.Feasibility of structural network clustering
tools which can be used as a tool in education industry to for group-based privacy control in social networks, ACM, Vol 5,
Issue 1, pp. 38-40, 2010.
generate on line traffic and a pipe line for new entrants. [14].Leenes, R..Sociality and Privacy in Online Social Network Sites,
The use of these websites is growing rapidly, while others Springer Boston, vol 320, pp. 48–65, 2010.
traditional online is on the decrease. There are vulnerable
friends on social networking sites and it is important to
find and unfriend vulnerable friends so that users can
improve their privacy and security. Unfriending vulnerable
friends from a user's social network can significantly
decrease the user's social utility. In this paper, we study the
novel problem of vulnerability reduction with social utility
loss constraints.
7. FUTURE WORK
While the internet does introduce significant security risks,
if policies and controls are designed appropriately,
information security can be enhanced. Our long-term
objective is to focus on various privacy barriers in SNS
and suggest methods to overcome these barriers. The
means for achieving this objective would be by developing
an agile framework for privacy design that would combine
the negotiations and conflict resolution strategies. This
privacy framework will help in making the social
networking sites more secure.
REFERENCES
[1].Ateeq Ahma.. International Journal of Advanced Computer
science and Applications, Vol. 2, No.2, February 2011.
[2]. P Gundecha, H Liu . Minimizing user vulnerability of social
networking sites, public.asu.edu, .Dec 2012.
[3].Lenhart, A; & Madden. privacy & online social network,
http://www.danah.org/papers/JCMCIntro.pdf ,2007.
[4]. Rosenblum, D., The Privacy Risks of Social Networking Sites ,
IEEE Security and Privacy, Vol. 5,Issue 3, pp. 40-49, May 2007.
[5]. Ellison, N.B; Steinfield, C; & Lampe, C. The benefits of Face book
"friends:" Social capital and college students' use of online social
network site, Journal of Computer-Mediated Communication.Vol
12, Issue 4.july 2007.
121
Potrebbero piacerti anche
- Unraveling the Fediverse: A Journey into Decentralized Social NetworkingDa EverandUnraveling the Fediverse: A Journey into Decentralized Social NetworkingNessuna valutazione finora
- Security and Privacy in Social NetworksDocumento4 pagineSecurity and Privacy in Social Networkskatherinsania23Nessuna valutazione finora
- 2011 Vol 36 No 1 Sub 10Documento7 pagine2011 Vol 36 No 1 Sub 10Gonzalo SalcedoNessuna valutazione finora
- Ahn, Shehab, Squicciarini - 2011 - Security and Privacy in Social Networks PDFDocumento3 pagineAhn, Shehab, Squicciarini - 2011 - Security and Privacy in Social Networks PDFClaudia MachadoNessuna valutazione finora
- Internet Based Social Networking ServicesDocumento3 pagineInternet Based Social Networking ServicesEditor IJRITCCNessuna valutazione finora
- Privacy Preserving Social Media Data Publishing For Personalized RecommendationsDocumento14 paginePrivacy Preserving Social Media Data Publishing For Personalized RecommendationsRajNessuna valutazione finora
- Privacy Issues On Social Networking Websites: January 2021Documento11 paginePrivacy Issues On Social Networking Websites: January 2021mohammpooyaNessuna valutazione finora
- A Detailed Dominant Data Mining Approach For Predictive Modeling of Social Networking Data Using WEKADocumento8 pagineA Detailed Dominant Data Mining Approach For Predictive Modeling of Social Networking Data Using WEKAEditor IJRITCCNessuna valutazione finora
- How Much Privacy We Still Have On Social NetworkDocumento5 pagineHow Much Privacy We Still Have On Social NetworkShane TaylorNessuna valutazione finora
- Multiparty Access Control For Online Social Networks: Model and MechanismsDocumento15 pagineMultiparty Access Control For Online Social Networks: Model and Mechanismsعلو الدوريNessuna valutazione finora
- SSRN Id3793386Documento27 pagineSSRN Id3793386Dhanush Reddy RollaNessuna valutazione finora
- Social Media Security Risks, Cyber Threats and Risks Prevention and Mitigation TechniquesDocumento6 pagineSocial Media Security Risks, Cyber Threats and Risks Prevention and Mitigation TechniquesgurkanNessuna valutazione finora
- Security in Social NetworksDocumento32 pagineSecurity in Social NetworksChutiya InsaanNessuna valutazione finora
- Privacy Inference Attack Against Users in Online Social Networks A Literature ReviewDocumento15 paginePrivacy Inference Attack Against Users in Online Social Networks A Literature ReviewMOHNessuna valutazione finora
- Chapter - 1: Privacy and Security in Social NetworksDocumento15 pagineChapter - 1: Privacy and Security in Social NetworksSoumyaNessuna valutazione finora
- Security in Social NetworksDocumento32 pagineSecurity in Social NetworksChutiya InsaanNessuna valutazione finora
- Impact of Trust, Security and Privacy Concerns in Social Networking: An Exploratory Study To Understand The Pattern of Information Revelation in FacebookDocumento6 pagineImpact of Trust, Security and Privacy Concerns in Social Networking: An Exploratory Study To Understand The Pattern of Information Revelation in FacebookVanisa AliNessuna valutazione finora
- Security Aspects and Future Trends of Social NetworksDocumento20 pagineSecurity Aspects and Future Trends of Social NetworkspjayasingheNessuna valutazione finora
- Survey Sample Report PDFDocumento20 pagineSurvey Sample Report PDFUmer FarooqNessuna valutazione finora
- Prevention of Privacy Leaks in Social Networking Post Using NLPDocumento16 paginePrevention of Privacy Leaks in Social Networking Post Using NLPfareesaNessuna valutazione finora
- p531 ZhelevaDocumento10 paginep531 ZhelevatestNessuna valutazione finora
- Privacy Shield: Securing Privacy in Social NetworksDocumento4 paginePrivacy Shield: Securing Privacy in Social NetworksNairouz AlzinNessuna valutazione finora
- My Privacy My Decision: Control of Photo Sharing On Online Social NetworksDocumento84 pagineMy Privacy My Decision: Control of Photo Sharing On Online Social NetworksGowri ShankarNessuna valutazione finora
- IJSARTV4I422235Documento6 pagineIJSARTV4I422235Arnold AndamNessuna valutazione finora
- Quantitative Evaluation of Security and Privacy Perceptions in Online Social Networks A Case StudyDocumento9 pagineQuantitative Evaluation of Security and Privacy Perceptions in Online Social Networks A Case StudyShane TaylorNessuna valutazione finora
- Privacy & Security Concerns Over Social Networking Sites - Does It Really Matter?Documento6 paginePrivacy & Security Concerns Over Social Networking Sites - Does It Really Matter?jongkiljNessuna valutazione finora
- Review and Analysis of Perception of Cyber Threats and Cyber Security Solutions To Achieve Trustworthy Online Social NetworkingDocumento9 pagineReview and Analysis of Perception of Cyber Threats and Cyber Security Solutions To Achieve Trustworthy Online Social Networkingvogel21cryNessuna valutazione finora
- Alkeinay, Norwawi - 2014 - User Oriented Privacy Model For Social Networks PDFDocumento7 pagineAlkeinay, Norwawi - 2014 - User Oriented Privacy Model For Social Networks PDFClaudia MachadoNessuna valutazione finora
- Privacy-Preserving Social Media Data Publishing For Personalized Ranking-Based RecommendationDocumento15 paginePrivacy-Preserving Social Media Data Publishing For Personalized Ranking-Based RecommendationKiran KumarNessuna valutazione finora
- New Access Control Methodology For Online Social NetworkDocumento3 pagineNew Access Control Methodology For Online Social NetworkIJCERT PUBLICATIONSNessuna valutazione finora
- Privacy and Security On Social MediaDocumento5 paginePrivacy and Security On Social MediaEditor IJTSRDNessuna valutazione finora
- Social NetworkingDocumento2 pagineSocial NetworkingLEONG CHEE MENG MoeNessuna valutazione finora
- Data Security Approach For Online Social Network: Subashini.KDocumento5 pagineData Security Approach For Online Social Network: Subashini.KganapathyNessuna valutazione finora
- Social MediaDocumento10 pagineSocial MediaSarafa AbdulazeezNessuna valutazione finora
- Analysis of The Impact of Social Networking SitesDocumento8 pagineAnalysis of The Impact of Social Networking SitesSin CatNessuna valutazione finora
- DDDMP 201532 A FINALPRINTDocumento12 pagineDDDMP 201532 A FINALPRINTAliNessuna valutazione finora
- Cyber Attacks Impacting On Communication Using Social Media: Systematic Review Using Data Cluster BallDocumento9 pagineCyber Attacks Impacting On Communication Using Social Media: Systematic Review Using Data Cluster BallWARSE JournalsNessuna valutazione finora
- Social Networking Website For College: A Social Website Based ApproachDocumento8 pagineSocial Networking Website For College: A Social Website Based ApproachAtul KumarNessuna valutazione finora
- The Impact of Cyber Threats On Social Networking SitesDocumento10 pagineThe Impact of Cyber Threats On Social Networking Sitesプリンシペ カールNessuna valutazione finora
- Chap 1 & 2Documento12 pagineChap 1 & 2RoshiniNessuna valutazione finora
- An Enhanced Graph-Based Semi-Supervised Learning Algorithm To Detect Fake Users On TwitterDocumento22 pagineAn Enhanced Graph-Based Semi-Supervised Learning Algorithm To Detect Fake Users On Twitterkaran kallaNessuna valutazione finora
- Tokunaga 2011 CHBDocumento10 pagineTokunaga 2011 CHBOti VuraNessuna valutazione finora
- Preventing Private Information Inference Attacks On Social NetworksDocumento14 paginePreventing Private Information Inference Attacks On Social NetworksjayamrcvinothNessuna valutazione finora
- TTL 1 Module 2 Casano Beed 3-CDocumento4 pagineTTL 1 Module 2 Casano Beed 3-CRica Julea DacaraNessuna valutazione finora
- MSN PaperDocumento6 pagineMSN PaperMadan PatilNessuna valutazione finora
- Social Media and Security: How To Ensure Safe Social NetworkingDocumento3 pagineSocial Media and Security: How To Ensure Safe Social NetworkingIshfaq MajidNessuna valutazione finora
- Privacy Issues in Social NetworkingDocumento12 paginePrivacy Issues in Social NetworkingAN NANessuna valutazione finora
- Social Networks Have Become So Ugly That They Will Be The #1 Source of Malware InfectionsDocumento2 pagineSocial Networks Have Become So Ugly That They Will Be The #1 Source of Malware InfectionsNatalia BalcazasNessuna valutazione finora
- Computer Science ProjectDocumento15 pagineComputer Science ProjectAishwarya MaheshNessuna valutazione finora
- A Privacy-Preserving Model To Control Social Interaction Behaviors inDocumento8 pagineA Privacy-Preserving Model To Control Social Interaction Behaviors inSabrina YusupNessuna valutazione finora
- PXC 3881014Documento6 paginePXC 3881014rayan.alshami153Nessuna valutazione finora
- Social Networking Privacy How To Be Safe, Secure and SocialDocumento17 pagineSocial Networking Privacy How To Be Safe, Secure and SocialRafael AlemanNessuna valutazione finora
- The Paradox of Social Media Security Users Perceptions Versus BehaviorsDocumento6 pagineThe Paradox of Social Media Security Users Perceptions Versus BehaviorsShane TaylorNessuna valutazione finora
- (4.1) Social Media Privacy Issues For 2020 - Threats & RisksDocumento7 pagine(4.1) Social Media Privacy Issues For 2020 - Threats & RisksIman NabeehaNessuna valutazione finora
- 1579-Article Text PDF-5195-1-10-20130303Documento5 pagine1579-Article Text PDF-5195-1-10-20130303Adrian GiscaNessuna valutazione finora
- Social Media and DataDocumento13 pagineSocial Media and DatasaleemNessuna valutazione finora
- Collaborative Final PDFDocumento13 pagineCollaborative Final PDFAhmed MohamedNessuna valutazione finora
- Implementation of Privacy Policy Specification System For User Uploaded Images Over Popular Content Sharing SitesDocumento5 pagineImplementation of Privacy Policy Specification System For User Uploaded Images Over Popular Content Sharing SitesEditor IJRITCCNessuna valutazione finora
- S4 Employers Use of Social Networking Sites A SocialDocumento20 pagineS4 Employers Use of Social Networking Sites A SocialKatherine Figlie MacedoNessuna valutazione finora
- DocDocumento68 pagineDocSushma GajjalaNessuna valutazione finora
- Pemphigus Subtypes Clinical Features Diagnosis andDocumento23 paginePemphigus Subtypes Clinical Features Diagnosis andAnonymous bdFllrgorzNessuna valutazione finora
- Literature Review LichenDocumento7 pagineLiterature Review LichenNur Fazrina CGNessuna valutazione finora
- An Improved Version of The Skin Chapter of Kent RepertoryDocumento6 pagineAn Improved Version of The Skin Chapter of Kent RepertoryHomoeopathic PulseNessuna valutazione finora
- Statistical TestsDocumento47 pagineStatistical TestsUche Nwa ElijahNessuna valutazione finora
- Vocabulary Ladders - Grade 3 - Degree of FamiliarityDocumento6 pagineVocabulary Ladders - Grade 3 - Degree of FamiliarityfairfurNessuna valutazione finora
- FORTRESS EUROPE by Ryan BartekDocumento358 pagineFORTRESS EUROPE by Ryan BartekRyan Bartek100% (1)
- Appendix H Sample of Coded Transcript PDFDocumento21 pagineAppendix H Sample of Coded Transcript PDFWahib LahnitiNessuna valutazione finora
- Zone Raiders (Sci Fi 28mm)Documento49 pagineZone Raiders (Sci Fi 28mm)Burrps Burrpington100% (3)
- 39 - Riyadhah Wasyamsi Waduhaha RevDocumento13 pagine39 - Riyadhah Wasyamsi Waduhaha RevZulkarnain Agung100% (18)
- Acc 106 Ebook Answer Topic 4Documento13 pagineAcc 106 Ebook Answer Topic 4syifa azhari 3BaNessuna valutazione finora
- IPA Digital Media Owners Survey Autumn 2010Documento33 pagineIPA Digital Media Owners Survey Autumn 2010PaidContentUKNessuna valutazione finora
- Art of Insight PDFDocumento409 pagineArt of Insight PDF31482Nessuna valutazione finora
- Thailand Day 2Documento51 pagineThailand Day 2Edsel BuletinNessuna valutazione finora
- Role LibrariesDocumento57 pagineRole LibrariesGiovanni AnggastaNessuna valutazione finora
- InfoVista Xeus Pro 5 TMR Quick GuideDocumento76 pagineInfoVista Xeus Pro 5 TMR Quick GuideNguyen Dang KhanhNessuna valutazione finora
- Map Index: RD - To CE MP AR KDocumento1 paginaMap Index: RD - To CE MP AR KswaggerboxNessuna valutazione finora
- RH Control - SeracloneDocumento2 pagineRH Control - Seraclonewendys rodriguez, de los santosNessuna valutazione finora
- Womack - Labor History, Industrial Work, Economics, Sociology and Strategic Position PDFDocumento237 pagineWomack - Labor History, Industrial Work, Economics, Sociology and Strategic Position PDFhmaravilloNessuna valutazione finora
- Sample Programs in CDocumento37 pagineSample Programs in CNoel JosephNessuna valutazione finora
- Microsoft Official Course: Installing and Configuring Windows Server 2012Documento18 pagineMicrosoft Official Course: Installing and Configuring Windows Server 2012jttodorovNessuna valutazione finora
- Tfa Essay RubricDocumento1 paginaTfa Essay Rubricapi-448269753Nessuna valutazione finora
- Early Pregnancy and Its Effect On The Mental Health of Students in Victoria Laguna"Documento14 pagineEarly Pregnancy and Its Effect On The Mental Health of Students in Victoria Laguna"Gina HerraduraNessuna valutazione finora
- Sample ProposalDocumento2 pagineSample ProposaltoupieNessuna valutazione finora
- Introduction and Overview: "Calculus I" Is Divided Into Five Chapters. Sequences and Series Are Introduced in Chapter 1Documento1 paginaIntroduction and Overview: "Calculus I" Is Divided Into Five Chapters. Sequences and Series Are Introduced in Chapter 1mangalvao2009Nessuna valutazione finora
- Reviewer in Auditing Problems by Reynaldo Ocampo PDFDocumento1 paginaReviewer in Auditing Problems by Reynaldo Ocampo PDFCarlo BalinoNessuna valutazione finora
- Bahasa Inggris XIIDocumento1 paginaBahasa Inggris XIIclaudiaomega.pNessuna valutazione finora
- A Management and Leadership TheoriesDocumento43 pagineA Management and Leadership TheoriesKrezielDulosEscobarNessuna valutazione finora
- History of AIDocumento27 pagineHistory of AImuzammalNessuna valutazione finora
- TreeAgePro 2013 ManualDocumento588 pagineTreeAgePro 2013 ManualChristian CifuentesNessuna valutazione finora
- Counter-Example NLPDocumento8 pagineCounter-Example NLPRafaelBluskyNessuna valutazione finora