Documenti di Didattica
Documenti di Professioni
Documenti di Cultura
Site2Site IPSec VPN With Dynamic IP PDF
Caricato da
Prakash RayTitolo originale
Copyright
Formati disponibili
Condividi questo documento
Condividi o incorpora il documento
Hai trovato utile questo documento?
Questo contenuto è inappropriato?
Segnala questo documentoCopyright:
Formati disponibili
Site2Site IPSec VPN With Dynamic IP PDF
Caricato da
Prakash RayCopyright:
Formati disponibili
Site-to-site IPSec VPN by using dynamic IP
example
Technical Note
Site-to-site IPSec VPN by using dynamic IP example Technical Note
Document Version: Version 2
Publication Date: 24 August 2012
Description: This technical note features a detailed configuration example that demonstrates
how to set up a basic site-to-site IPSec VPN that uses preshared keys to
authenticate the two VPN peers.
Product: FortiGate v4.00 MR3
Document Number: 09-28006-0119-20100605
Fortinet Inc. 09-28006-0119-20100605 Page 1 of 15
© Copyright 2012 Fortinet Inc. All rights reserved.
No part of this publication including text, examples, diagrams or illustrations
may be reproduced, transmitted, or translated in any form or by any means,
electronic, mechanical, manual, optical or otherwise, for any purpose, without
prior written permission of Fortinet Inc.
Site-to-site IPSec VPN by using dynamic IP example Technical Note
FortiGate v4.00 MR3
24 August 2012
09-28006-0119-20100605
Trademarks
Products mentioned in this document are trademarks or registered trademarks of their respective
holders.
Fortinet Inc. 09-28006-0119-20100605 Page 2 of 15
Contents
Table of Contents
Network topology ... .................................................................................................................... 4
Infrastructure requirements .................................................................................................4
Setup Firewall-Address on FortiGate_1... .................................................................................. 5
Define the IP/Netmask or FQDN... ......................................................................................... 5
Setup Firewall-Address on FortiGate_2... .................................................................................. 6
Define the IP/Netmask or FQDN... ......................................................................................... 6
Configuring IPSEC VPN on FortiGate_1... ................................................................................ 7
Define the phase 1 parameters... ........................................................................................... 7
Define the phase 2 parameters... ........................................................................................... 8
Configuring IPSEC VPN on FortiGate_2... ................................................................................ 9
Define the phase 1 parameters... ........................................................................................... 9
Define the phase 2 parameters... ........................................................................................... 10
Define Policy and Router on FortiGate_1... ............................................................................... 11
Define Policy and Router on FortiGate_2... ............................................................................... 13
Finalize Policy and VPN... .......................................................................................................... 15
Fortinet Inc. 09-28006-0119-20100605 Page 3 of 15
Site-to-site IPSec VPN by using dynamic IP example
This technical note features a detailed configuration example that demonstrates how to set up a basic
site-to-site IPSec VPN that uses preshared keys to
authenticate the two VPN peers. The following sections are included:
• Network topology
• Setup Firewall-Address on FortiGate_1
• Setup Firewall-Address on FortiGate_2
• Configuring FortiGate_1
• Configuring FortiGate_2
• Define Policy and Router on FortiGate_1
• Define Policy and Router on FortiGate_2
• Finalize
Network topology
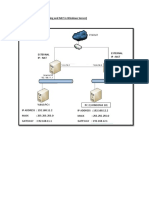
In a site-to-site configuration, two FortiGate units create an IPSec tunnel between two separate
private networks. All traffic between the two networks is encrypted and protected by FortiGate
firewall policies. See Figure 1.
Figure 1: Example Site-to-site configuration
Site_1 Site_2
FortiGate_1 FortiGate_2
Internet
111.111.111.111 222.222.222.222
us.dyndns.org tw.dyndns.org
(WAN1) (WAN1)
US Network TW Network
192.168.11.0/24 192.168.22.0/24
(Internal) (Internal)
In the examples throughout this technical bulletin, the network devices are assigned IP
addresses as shown in Figure 1.
Infrastructure requirements
• The FortiGate units at both ends of the tunnel must be operating in NAT mode and have public
IP addresses by static or dynamic with www.dyndns.org as service.
Fortinet Inc. 09-28006-0119-20100605 Page 4 of 15
Site-to-site IPSec VPN by using dynamic IP Example
Setup Firewall-Address on FortiGate_1
Define the IP/netmask or FQDN
To define the IP/netmask
1 Go to Firewall > Address > Address.
2-1 Select (Create New), enter the following information, and select OK:
Address Name Type a name for the local network (e.g., US_Network)
Type Subnet / IP Range
Subnet / IP Range 192.168.11.0/255.255.255.0
Interface Internal
2-2 Select (Create New), enter the following information, and select OK:
Address Name Type a name for the local network (e.g., TW_Network)
Type Subnet / IP Range
Subnet / IP Range 192.168.22.0/255.255.255.0
Interface WAN1(ADSL)
To define the FQDN
1 Go to Firewall > Address > Address.
2 Select (Create New), enter the following information, and select OK:
Address Name Type a name for the local network (e.g., TW_Network)
Type FQDN
FQDN tw.dyndns.org
Interface WAN1(ADSL)
Fortinet Inc. 09-28006-0119-20100605 Page 5 of 15
Site-to-site IPSec VPN by using dynamic IP Example
Setup Firewall-Address on FortiGate_2
Define the IP/netmask or FQDN
To define the IP/netmask
1 Go to Firewall > Address > Address.
2-1 Select (Create New), enter the following information, and select OK:
Address Name Type a name for the local network (e.g., TW_Network)
Type Subnet / IP Range
Subnet / IP Range 192.168.22.0/255.255.255.0
Interface Internal
2-2 Select (Create New), enter the following information, and select OK:
Address Name Type a name for the local network (e.g., US_Network)
Type Subnet / IP Range
Subnet / IP Range 192.168.11.0/255.255.255.0
Interface WAN1(ADSL)
To define the FQDN
1 Go to Firewall > Address > Address.
2 Select (Create New), enter the following information, and select OK:
Address Name Type a name for the local network (e.g., US_Network)
Type FQDN
FQDN us.dyndns.org
Interface WAN1(ADSL)
Fortinet Inc. 09-28006-0119-20100605 Page 6 of 15
Site-to-site IPSec VPN by using dynamic IP Example
Configuring FortiGate_1
Define the phase 1 parameters
Before you define the phase 1 parameters, you need to:
• Reserve a name for the remote gateway.
• Obtain the IP address of the public interface to the remote peer.
• Reserve a unique value for the preshared key (e.g. passkey1$).
The key must contain at least 6 printable characters and should only be known by
network administrators. For optimum protection against currently known attacks, the
key should consist of a minimum of 16 randomly chosen alphanumeric characters.
To define the phase 1 parameters
1 Go to VPN > IPsec > Auto Key (IKE).
2-1 Select (Create Phase 1), enter the following information, and select OK:
Gateway Name Type a name for the remote gateway (e.g., ToFortiGate2).
Remote Gateway Dynamic DNS
Dynamic DNS tw.dyndns.org
Local Interface WAN1(ADSL)
Mode Main (ID protection)
Authentication Method Preshared Key
Pre-shared Key Enter the preshared key (e.g., passkey$).
Peer Options Accept any peer ID
2-2 Select (Advanced…), enter the following information, and select OK:
Local Gateway IP Main Interface IP
P1 Proposal 1- Encryption: 3DES Authentication: SHA1
2- Encryption: 3DES Authentication: MD5
DH Group 5
Keylife 28800
XAUTH Disable
NAT Traversal Enable
Keepalive Frequency 10
Dead Peer Detection Enable
Fortinet Inc. 09-28006-0119-20100605 Page 7 of 15
Site-to-site IPSec VPN by using dynamic IP example
Configuring FortiGate_1 (continue…)
Define the phase 2 parameters
The basic phase 2 settings associate IPSec phase 2 parameters with the phase 1
configuration and specify the remote end point of the VPN tunnel. Before you define the
phase 2 parameters, you need to reserve a name for the tunnel.
To define the phase 2 parameters
1 Go to VPN > IPSEC > Auto Key (IKE).
2-1 Select (Create Phase 2), enter the following information and select OK:
Name Enter a name for the tunnel (e.g., ToFortigate2-ph2).
Phase 1 Select the gateway that you defined previously (e.g., ToFortigate2).
2-2 Select (Advanced…), enter the following information and select OK:
P2 Proposal 1-Encryption: 3DES Authentication: SHA1
1-Encryption: 3DES Authentication: MD5
[v] Enable replay detection
[v] Enable perfect forward secrecy (PFS)
DH Group: 5
Keylife Seconds 1800
Autokey Keep Alive Enable
Quick Mode Selector Source address: (*)select: 192.168.11.0/24 or US_NETWORK
Source port:0
Destination port: (*)select: 192.168.22.0/24 or TW_NETWORK
Destination port: 0
Protocol: 0
Fortinet Inc. 09-28006-0119-20100605 Page 8 of 15
Site-to-site IPSec VPN by using dynamic IP example
Configuring FortiGate_2
Define the phase 1 parameters
Before you define the phase 1 parameters, you need to:
• Reserve a name for the remote gateway.
• Obtain the IP address of the public interface to the remote peer.
• Reserve a unique value for the preshared key (e.g. passkey1$).
The key must contain at least 6 printable characters and should only be known by
network administrators. For optimum protection against currently known
attacks, the key should consist of a minimum of 16 randomly chosen
alphanumeric characters.
To define the phase 1 parameters
1 Go to VPN > IPSEC > Auto Key (IKE).
2-1 Select (Create Phase 1), enter the following information, and select OK:
Gateway Name Type a name for the remote gateway (e.g., ToFortiGate1).
Remote Gateway Dynamic DNS
Dynamic DNS us.dyndns.org
Local Interface WAN1(ADSL)
Mode Main (ID protection)
Authentication Method Preshared Key
Pre-shared Key Enter the preshared key (e.g., passkey$).
Peer Options Accept any peer ID
2-2 Select (Advanced…), enter the following information, and select OK:
Local Gateway IP Main Interface IP
P1 Proposal 1- Encryption: 3DES Authentication: SHA1
2- Encryption: 3DES Authentication: MD5
DH Group 5
Keylife 28800
XAUTH Disable
NAT Traversal Enable
Keepalive Frequency 10
Dead Peer Detection Enable
Fortinet Inc. 09-28006-0119-20100605 Page 9 of 15
Site-to-site IPSec VPN by using dynamic IP example
Configuring FortiGate_2 (continue…)
Define the phase 2 parameters
The basic phase 2 settings associate IPSec phase 2 parameters with the phase 1
configuration and specify the remote end point of the VPN tunnel. Before you define the
phase 2 parameters, you need to reserve a name for the tunnel.
To define the phase 2 parameters
1 Go to VPN > IPSEC > Auto Key (IKE).
2-1 Select (Create Phase 2), enter the following information and select OK:
Name Enter a name for the tunnel (e.g., ToFortigate1-ph2).
Phase 1 Select the gateway that you defined previously (e.g., ToFortigate1).
2-2 Select (Advanced…), enter the following information and select OK:
P2 Proposal 1-Encryption: 3DES Authentication: SHA1
1-Encryption: 3DES Authentication: MD5
[v] Enable replay detection
[v] Enable perfect forward secrecy (PFS)
DH Group: 5
Keylife: Seconds 1800
Autokey Keep Alive Enable
Quick Mode Selector Source address: (*)select: 192.168.22.0/24 or TW_NETWORK
Source port:0
Destination port: (*)select: 192.168.11.0/24 or US_NETWORK
Destination port: 0
Protocol: 0
Fortinet Inc. 09-28006-0119-20100605 Page 10 of 15
Site-to-site IPSec VPN by using dynamic IP example
Define Policy and Router on FortiGate_1
Define the firewall encryption policy
Firewall policies control all IP traffic passing between a source address and a
destination address. A firewall encryption policy is needed to allow the
transmission of encrypted packets, specify the permitted direction of VPN
traffic, and select the VPN tunnel that will be subject to the policy. A single
encryption policy is needed to control both inbound and outbound IP traffic
through a VPN tunnel.
Before you define the policy, you must first specify the IP source and
destination addresses. In a Site-to-site configuration:
• The source IP address corresponds to the private network behind the local FortiGate
unit.
• The destination IP address refers to the private network behind the remote VPN peer.
To define the firewall encryption policy for a policy-based VPN
1 Go to Firewall > Policy > Policy.
2 Select (Create New), enter the following information, and select OK:
Source Interface/Zone Internal
Source Address US_Network or 192.168.11.0/24
Destination Interface/Zone WAN1 (ADSL)
Destination Address TW_Network or 192.168.22.0/24
Schedule Always
Service ANY
Action IPSEC
VPN Tunnel 2Fortigate2
Allow inbound [v]
Allow outbound [v]
Inbound NAT Disable
Outbound NAT Disable
3 Place the policy in the policy list above any other policies having similar source and
destination addresses.
Fortinet Inc. 09-28006-0119-20100605 Page 11 of 15
Site-to-site IPSec VPN by using dynamic IP example
Define Policy and Router on FortiGate_1 (continue…)
To define the firewall encryption policy for a route-based VPN
1 Go to Firewall > Policy > Policy.
2 Select (Create New), enter the following information, and select OK:
Source Interface/Zone Internal
Source Address US_Network or 192.168.11.0/24
Destination Interface/Zone 2Fortigate2
Destination Address TW_Network or 192.168.22.0/24
Schedule Always
Service ANY
Action ACCEPT
Inbound NAT Disable
3 Select (Create New), enter the following information, and select OK:
Source Interface/Zone 2Fortigate2
Source Address TW_Network or 192.168.22.0/24
Destination Interface/Zone Internal
Destination Address US_Network or 192.168.11.0/24
Schedule Always
Service ANY
Action ACCEPT
Inbound NAT Disable
4 Place the policy in the policy list above any other policies having similar source and
destination addresses.
5 Go to Router > Static.
6 Select (Create New), enter the following information, and select OK:
Destination IP / Mask 192.168.22.0/24
Service 2Fortigate2
Gateway Leave as default: 0.0.0.0
Distance Leave this as its default
Fortinet Inc. 09-28006-0119-20100605 Page 12 of 15
Site-to-site IPSec VPN by using dynamic IP example
Define Policy and Router on FortiGate_2
Define the firewall encryption policy
Firewall policies control all IP traffic passing between a source address and a
destination address. A firewall encryption policy is needed to allow the
transmission of encrypted packets, specify the permitted direction of VPN
traffic, and select the VPN tunnel that will be subject to the policy. A single
encryption policy is needed to control both inbound and outbound IP traffic
through a VPN tunnel.
Before you define the policy, you must first specify the IP source and
destination addresses. In a Site-to-site configuration:
• The source IP address corresponds to the private network behind the local FortiGate
unit.
• The destination IP address refers to the private network behind the remote VPN peer.
To define the firewall encryption policy
1 Go to Firewall > Policy > Policy.
2 Select (Create New), enter the following information, and select OK:
Source Interface/Zone Internal
Source Address TW_Network or 192.168.22.0/24
Destination Interface/Zone WAN1 (ADSL)
Destination Address US_Network or 192.168.11.0/24
Schedule Always
Service ANY
Action IPSEC
VPN Tunnel 2Fortigate1
Allow inbound [v]
Allow outbound [v]
Inbound NAT Disable
Outbound NAT Disable
3 Place the policy in the policy list above any other policies having similar source and
destination addresses.
Fortinet Inc. 09-28006-0119-20100605 Page 13 of 15
Site-to-site IPSec VPN by using dynamic IP example
Define Policy and Router on FortiGate_2 (continue…)
To define the firewall encryption policy for a route-based VPN
1 Go to Firewall > Policy > Policy.
2 Select (Create New), enter the following information, and select OK:
Source Interface/Zone Internal
Source Address TW_Network or 192.168.22.0/24
Destination Interface/Zone 2Fortigate1
Destination Address US_Network or 192.168.11.0/24
Schedule Always
Service ANY
Action ACCEPT
Inbound NAT Disable
3 Select (Create New), enter the following information, and select OK:
Source Interface/Zone 2Fortigate1
Source Address US_Network or 192.168.11.0/24
Destination Interface/Zone Internal
Destination Address TW_Network or 192.168.22.0/24
Schedule Always
Service ANY
Action ACCEPT
Inbound NAT Disable
4 Place the policy in the policy list above any other policies having similar source and
destination addresses.
5 Go to Router > Static.
6 Select (Create New), enter the following information, and select OK:
Destination IP / Mask 192.168.11.0/24
Service 2Fortigate1
Gateway Leave as default: 0.0.0.0
Distance Leave this as its default
Fortinet Inc. 09-28006-0119-20100605 Page 14 of 15
Site-to-site IPSec VPN by using dynamic IP example
Finalize
Policy and VPN
To Move up the firewall encryption policy on top
1 Go to Firewall > Policy > select internal -> wan1 policy.
2 Click the Move To and move the policy to the very top.
(If you don’t put it on top, you are unable to ping site’s IP from the other site’s client PC)
To Bring Up the site-to-site VPN
1 Go to VPN > IPSEC > Monitor
Click on Bring Up under Status.
SOURCE:
http://docs.fortinet.com/fgt/handbook/40mr3/fortigate-ipsec-40-mr3.pdf
http://docs.fortinet.com/cookbook.html
Fortinet Inc. 09-28006-0119-20100605 Page 15 of 15
Potrebbero piacerti anche
- Computer Networking: An introductory guide for complete beginners: Computer Networking, #1Da EverandComputer Networking: An introductory guide for complete beginners: Computer Networking, #1Valutazione: 4.5 su 5 stelle4.5/5 (2)
- Cisco CCNA Command Guide: An Introductory Guide for CCNA & Computer Networking Beginners: Computer Networking, #3Da EverandCisco CCNA Command Guide: An Introductory Guide for CCNA & Computer Networking Beginners: Computer Networking, #3Nessuna valutazione finora
- Network with Practical Labs Configuration: Step by Step configuration of Router and Switch configurationDa EverandNetwork with Practical Labs Configuration: Step by Step configuration of Router and Switch configurationNessuna valutazione finora
- Mikrotik Firewall Training Router (Computing) PDFDocumento39 pagineMikrotik Firewall Training Router (Computing) PDFPhạm Đức HạnhNessuna valutazione finora
- BGP and The InternetDocumento11 pagineBGP and The InternetJaved HashmiNessuna valutazione finora
- Detail Scope of Work For Network Redesign Security For Internal and External Access WorkDocumento1 paginaDetail Scope of Work For Network Redesign Security For Internal and External Access WorkSon Tran Hong NamNessuna valutazione finora
- Configuring and Testing The VPN ClientDocumento8 pagineConfiguring and Testing The VPN Clientonlycisco.tkNessuna valutazione finora
- sp00-000 843 30 02 02Documento112 paginesp00-000 843 30 02 02Vlady Lopez CastroNessuna valutazione finora
- AZ 104T00A ENU PowerPoint - 04Documento36 pagineAZ 104T00A ENU PowerPoint - 04Prakash Ray100% (1)
- Configuring Route Based IPSec With Overlapping NetworksDocumento13 pagineConfiguring Route Based IPSec With Overlapping NetworksRyanb378Nessuna valutazione finora
- 1.1.4.6 Lab - Configuring Basic Router Settings With IOS CLIDocumento10 pagine1.1.4.6 Lab - Configuring Basic Router Settings With IOS CLIUser Ale100% (1)
- AZ-104T00A Intersite ConnectivityDocumento31 pagineAZ-104T00A Intersite ConnectivityPrakash Ray100% (2)
- AZ 104T00A ENU PowerPoint - 01Documento25 pagineAZ 104T00A ENU PowerPoint - 01Johan Johan100% (1)
- AZ 104T00A ENU PowerPoint - 09Documento44 pagineAZ 104T00A ENU PowerPoint - 09Prakash Ray100% (1)
- BGP Short Note FileDocumento60 pagineBGP Short Note FileTabarez Ahmed100% (1)
- Fortigate Firewall How To InternetDocumento8 pagineFortigate Firewall How To InternetKaushal KishorNessuna valutazione finora
- Cisco FTDV Anyconnect VPN Lab G Eve-Ng Lab GuideDocumento18 pagineCisco FTDV Anyconnect VPN Lab G Eve-Ng Lab GuideciscoNessuna valutazione finora
- Protecting A Web Server On A DMZ NetworkDocumento8 pagineProtecting A Web Server On A DMZ NetworkAnonymous k2SY4zdI3Nessuna valutazione finora
- AZ-104T00A Azure Virtual MachinesDocumento36 pagineAZ-104T00A Azure Virtual MachinesPrakash Ray100% (1)
- AZ-104T00A Governance and ComplianceDocumento34 pagineAZ-104T00A Governance and ComplianceJohan Johan100% (1)
- ACI Muti-PodDocumento59 pagineACI Muti-PodAlisamiirNessuna valutazione finora
- AZ 104T00A ENU PowerPoint - 11Documento42 pagineAZ 104T00A ENU PowerPoint - 11Prakash Ray100% (1)
- 10ICTCSS q3 Module1 MaintainingNetworksDocumento52 pagine10ICTCSS q3 Module1 MaintainingNetworksjayson yamonganNessuna valutazione finora
- Packet Tracer 1.3.1Documento11 paginePacket Tracer 1.3.13qtrtymNessuna valutazione finora
- AZ-104T00A Network Traffic ManagementDocumento34 pagineAZ-104T00A Network Traffic ManagementPrakash Ray100% (1)
- Basic Fortigate Firewall Configuration: Content at A GlanceDocumento17 pagineBasic Fortigate Firewall Configuration: Content at A GlanceDenisa PriftiNessuna valutazione finora
- IP Addressing and SubDocumento9 pagineIP Addressing and SubSeyhaSunNessuna valutazione finora
- AZ 104T00A ENU PowerPoint - 07Documento50 pagineAZ 104T00A ENU PowerPoint - 07Prakash Ray100% (1)
- AZ 104T00A ENU PowerPoint - 10Documento24 pagineAZ 104T00A ENU PowerPoint - 10Prakash Ray100% (1)
- AZ 104T00A ENU PowerPoint - 03Documento33 pagineAZ 104T00A ENU PowerPoint - 03Prakash RayNessuna valutazione finora
- FortiGate To SonicWall VPN SDocumento3 pagineFortiGate To SonicWall VPN SFabricio Soares BiccaNessuna valutazione finora
- Provisioning Oracle Database Appliance Bare Metal System PDFDocumento10 pagineProvisioning Oracle Database Appliance Bare Metal System PDFPicon Valqui EisenNessuna valutazione finora
- RTN 320 Introduction: Security LevelDocumento20 pagineRTN 320 Introduction: Security LevelJohn Ray Manao100% (1)
- Cisco Certified Network Associate 200-301: Download Tracer-For-Windows-And-Linux - HTMLDocumento18 pagineCisco Certified Network Associate 200-301: Download Tracer-For-Windows-And-Linux - HTMLasifyasinNessuna valutazione finora
- LINKSYS E1200 Configuration Guide For MRG Ver - 1.0 - FinalDocumento30 pagineLINKSYS E1200 Configuration Guide For MRG Ver - 1.0 - Finalalberto VasquezNessuna valutazione finora
- CTM-200 IPsec VPN QuestionnaireDocumento12 pagineCTM-200 IPsec VPN Questionnairemohammedakbar880% (1)
- Fortigate Configuration Guide For MRG Ver - 1.0 - FinalDocumento60 pagineFortigate Configuration Guide For MRG Ver - 1.0 - Finalalberto VasquezNessuna valutazione finora
- Lab 1.3.1Documento12 pagineLab 1.3.1Alondra CarmonaNessuna valutazione finora
- Wireless Bridge - DD-WRT WikiDocumento10 pagineWireless Bridge - DD-WRT WikicardreadreNessuna valutazione finora
- Configuring and Deploying NAT (Network Address Translation) On A Cisco RouterDocumento6 pagineConfiguring and Deploying NAT (Network Address Translation) On A Cisco RoutercursoNessuna valutazione finora
- Ipsec VPN Application GuideDocumento19 pagineIpsec VPN Application Guidedania kusmayaniNessuna valutazione finora
- Radio Setup Procedures - Remote - ACMDocumento10 pagineRadio Setup Procedures - Remote - ACMEdwin RincónNessuna valutazione finora
- Lo2 Security AashaDocumento6 pagineLo2 Security AashawayneNessuna valutazione finora
- Netmanais.2013.09.03.NAT Overview (En) PDFDocumento8 pagineNetmanais.2013.09.03.NAT Overview (En) PDFFiras Ibrahim Al-HamdanyNessuna valutazione finora
- Lab 2 10 4aDocumento3 pagineLab 2 10 4asilindeanNessuna valutazione finora
- How To Configure NAT (Network Address Translation) in Mikrotik ??Documento2 pagineHow To Configure NAT (Network Address Translation) in Mikrotik ??fargermNessuna valutazione finora
- FortiNAC Configuration Wizard Rev92Documento37 pagineFortiNAC Configuration Wizard Rev92Jagjeet SinghNessuna valutazione finora
- Step-by-Step Guide: Deploy Remote Access With VPN Reconnect in A Test LabDocumento38 pagineStep-by-Step Guide: Deploy Remote Access With VPN Reconnect in A Test LabNakul SinghalNessuna valutazione finora
- IM7200 Quick Start Guide: 01. Check The Kit's Contents Are CompleteDocumento4 pagineIM7200 Quick Start Guide: 01. Check The Kit's Contents Are CompleteMiro JanosNessuna valutazione finora
- NAT 10 Lab TasksDocumento4 pagineNAT 10 Lab Tasksmuhammad.mursleen025Nessuna valutazione finora
- Networking Basics For Automation Engineers: Page 1 of 10 Mac-Solutions - Co.uk v1.0 Oct 2014Documento10 pagineNetworking Basics For Automation Engineers: Page 1 of 10 Mac-Solutions - Co.uk v1.0 Oct 2014VenkataRameshKumarNessuna valutazione finora
- ESwitching Lab 1 3 1Documento12 pagineESwitching Lab 1 3 1Derek Ang Yew PinNessuna valutazione finora
- How Configure NatDocumento5 pagineHow Configure NatAbhinav MishraNessuna valutazione finora
- Great Great Soniwall NattingDocumento8 pagineGreat Great Soniwall NattingfqtsysNessuna valutazione finora
- Configure and Verify NATDocumento21 pagineConfigure and Verify NATJose L. RodriguezNessuna valutazione finora
- TG589vac Assigning A Block of IPsDocumento6 pagineTG589vac Assigning A Block of IPscharuvilNessuna valutazione finora
- Fortinet Security Fabric Fortigate 60FDocumento11 pagineFortinet Security Fabric Fortigate 60FJconnorNessuna valutazione finora
- Lab Report - 7 - EditedDocumento5 pagineLab Report - 7 - EditedAbdullah bin zahirNessuna valutazione finora
- Hadr Tsa WinDocumento52 pagineHadr Tsa Windani nabeelNessuna valutazione finora
- LABSEC-2020 ASA 8.3 (Or Higher) Lab Guide PDFDocumento11 pagineLABSEC-2020 ASA 8.3 (Or Higher) Lab Guide PDFRiadh MadhourNessuna valutazione finora
- Firewall Design and Deployment: BRKSEC-2020Documento107 pagineFirewall Design and Deployment: BRKSEC-2020djdylan78Nessuna valutazione finora
- Documento Huawei USG6000 Como DHCP-inglesDocumento17 pagineDocumento Huawei USG6000 Como DHCP-inglesSantiagoUChileNessuna valutazione finora
- Guia de Configuracion de Firewall Avanzado en GWN7000 Grandstream PDFDocumento12 pagineGuia de Configuracion de Firewall Avanzado en GWN7000 Grandstream PDFmiguel pcNessuna valutazione finora
- How To Configure VLAN and Route FailoverDocumento5 pagineHow To Configure VLAN and Route FailoverwebpcnetlinkNessuna valutazione finora
- Network Address Translation (NAT) : Barracuda Web Application FirewallDocumento3 pagineNetwork Address Translation (NAT) : Barracuda Web Application FirewallMiodrag CeperkovicNessuna valutazione finora
- Presentation 6612 1548663883 PDFDocumento36 paginePresentation 6612 1548663883 PDFRami AssafNessuna valutazione finora
- Using Policy-Based Ipsec VPN For Communication Between OfficesDocumento7 pagineUsing Policy-Based Ipsec VPN For Communication Between OfficesNgọc Duy VõNessuna valutazione finora
- 04.NGFW Firewall FeatureDocumento32 pagine04.NGFW Firewall FeaturedikaNessuna valutazione finora
- Dataone Configuration: Huawei MT880/882 Dare Global DB108 Huawei WA1003A Huawei MT841 Huawei MT800Documento27 pagineDataone Configuration: Huawei MT880/882 Dare Global DB108 Huawei WA1003A Huawei MT841 Huawei MT800joshimanan01Nessuna valutazione finora
- NETGEAR ProSafe VPN Firewall FVS338 ServerDocumento8 pagineNETGEAR ProSafe VPN Firewall FVS338 ServerDragan MilakovicNessuna valutazione finora
- Mcit - Ethio Joint Team Training MaterialDocumento56 pagineMcit - Ethio Joint Team Training MaterialMuhammedYeshaw67% (3)
- Rule To Communicate: TCP/IP (Transmission Control Protocol / Internet Protocol)Documento12 pagineRule To Communicate: TCP/IP (Transmission Control Protocol / Internet Protocol)lia_azaliaNessuna valutazione finora
- Fusion Gateway PC Installation Rev CDocumento28 pagineFusion Gateway PC Installation Rev CPatricio Villarroel GaticaNessuna valutazione finora
- Fortinet Fortigate 60Documento2 pagineFortinet Fortigate 60Davor Mendizabal TapiaNessuna valutazione finora
- Lab Exercise 3.3 Static Routing and NAT PDFDocumento13 pagineLab Exercise 3.3 Static Routing and NAT PDFSherine AnneNessuna valutazione finora
- NAT TutorialDocumento8 pagineNAT TutorialJuan Matias DamelioNessuna valutazione finora
- FortiClient 6.0.0 Administration Guide PDFDocumento136 pagineFortiClient 6.0.0 Administration Guide PDFPrakash RayNessuna valutazione finora
- Escalation Matrix For Enterprise Accounts: PNS Ver29. February 2018Documento3 pagineEscalation Matrix For Enterprise Accounts: PNS Ver29. February 2018Prakash RayNessuna valutazione finora
- Simple Step by Step Guide For Configuration of SSLVPN On Fortigate 100a Using MR4 00 PDFDocumento3 pagineSimple Step by Step Guide For Configuration of SSLVPN On Fortigate 100a Using MR4 00 PDFPrakash RayNessuna valutazione finora
- FortiGate 200D PDFDocumento4 pagineFortiGate 200D PDFPrakash RayNessuna valutazione finora
- FortiGate 200D PDFDocumento5 pagineFortiGate 200D PDFPrakash RayNessuna valutazione finora
- Fortigate Managing Devices 60 PDFDocumento14 pagineFortigate Managing Devices 60 PDFPrakash RayNessuna valutazione finora
- Default Schedule Default 2018 07-17-000100Documento19 pagineDefault Schedule Default 2018 07-17-000100Prakash RayNessuna valutazione finora
- Nokia Price ListDocumento18 pagineNokia Price ListPrakash RayNessuna valutazione finora
- Lecture 1 - Introduction To NetworkingDocumento37 pagineLecture 1 - Introduction To NetworkingAdam MuizNessuna valutazione finora
- Solo MOTOMESH Solo 2 2 Network Setup and Installation GuideDocumento142 pagineSolo MOTOMESH Solo 2 2 Network Setup and Installation Guidelanceloth741671100% (1)
- Final - Présentation5.0 - enDocumento43 pagineFinal - Présentation5.0 - enoffice engitechNessuna valutazione finora
- Pass Cisco 500-230 Exam With 100% GuaranteeDocumento4 paginePass Cisco 500-230 Exam With 100% GuaranteeOleg BosiukNessuna valutazione finora
- 452 Internet Protocol TelivisionDocumento22 pagine452 Internet Protocol TelivisionRam VBITNessuna valutazione finora
- Evalute The Trading System of Dhaka Stock ExchangeDocumento62 pagineEvalute The Trading System of Dhaka Stock ExchangeLikhon MiyaNessuna valutazione finora
- 5.2.1.4 Packet Tracer - Configuring Static Frame Relay Maps InstructionsDocumento3 pagine5.2.1.4 Packet Tracer - Configuring Static Frame Relay Maps InstructionsBRYAN ALEJANDRO GONZALES CAMPOSNessuna valutazione finora
- Windows and Networking Basic Questions and AnswerDocumento14 pagineWindows and Networking Basic Questions and AnswerCinema HungerNessuna valutazione finora
- CCNA Security PT Practice SBADocumento9 pagineCCNA Security PT Practice SBAkokiccna2012Nessuna valutazione finora
- Implementing Routing Facilities For Branch Offices and Mobile WorkersDocumento180 pagineImplementing Routing Facilities For Branch Offices and Mobile WorkersAlejandro Cordero OrdoñezNessuna valutazione finora
- CCNA2. Chapter 1Documento11 pagineCCNA2. Chapter 1sashii09100% (1)
- Setup A Guess Wireless Hotspot Using A DDWRT RouterDocumento3 pagineSetup A Guess Wireless Hotspot Using A DDWRT RouterJM TSRNessuna valutazione finora
- 02a BACnet IP Fundamentals May2022 v02 HANDOUTDocumento25 pagine02a BACnet IP Fundamentals May2022 v02 HANDOUTWalter BarbaNessuna valutazione finora
- Network Operating Systems and Service 4Documento9 pagineNetwork Operating Systems and Service 4Moi EricksonNessuna valutazione finora
- Cisco Configuring The RouterDocumento3 pagineCisco Configuring The Routerkuku2008Nessuna valutazione finora
- l2 Mpls VPN ConfigDocumento68 paginel2 Mpls VPN ConfigSorabh MohindruNessuna valutazione finora
- 5.1.2.4 Lab - Configuring Per-Interface Inter-VLAN RoutingDocumento5 pagine5.1.2.4 Lab - Configuring Per-Interface Inter-VLAN RoutingMuhammad AfNanzNessuna valutazione finora
- Configuring Ip Sla PBR Object Tracking PDFDocumento8 pagineConfiguring Ip Sla PBR Object Tracking PDFAamir RazaNessuna valutazione finora
- HP MSR930 Router Series - HP A-MSR20 - A-MSR30 - A-MSR50 - A-MSR900 - MSR93X-CMW520-R2509-SI Release Notes-C03926564Documento90 pagineHP MSR930 Router Series - HP A-MSR20 - A-MSR30 - A-MSR50 - A-MSR900 - MSR93X-CMW520-R2509-SI Release Notes-C03926564Ivan RamirezNessuna valutazione finora
- Setting Up Site-To-Site IPsec VPN On TP-LINK RouterDocumento8 pagineSetting Up Site-To-Site IPsec VPN On TP-LINK RouterArjo BoledNessuna valutazione finora
- Instructor Materials Chapter 1: WAN Concepts: CCNA Routing and Switching Connecting NetworksDocumento29 pagineInstructor Materials Chapter 1: WAN Concepts: CCNA Routing and Switching Connecting NetworksAsy LpanNessuna valutazione finora
- CH 01 - DCC10e Data Communications, Data Network and InternetDocumento33 pagineCH 01 - DCC10e Data Communications, Data Network and InternetDaya Ruano ChuldeNessuna valutazione finora
- How To Build Your Own Mikrotik WifiDocumento14 pagineHow To Build Your Own Mikrotik WifiHafidz Jazuli LuthfiNessuna valutazione finora
- DLINK 819 ManualDocumento155 pagineDLINK 819 ManualNacib NemeNessuna valutazione finora