Documenti di Didattica
Documenti di Professioni
Documenti di Cultura
Netstat Comm
Caricato da
Mirza CerimDescrizione originale:
Copyright
Formati disponibili
Condividi questo documento
Condividi o incorpora il documento
Hai trovato utile questo documento?
Questo contenuto è inappropriato?
Segnala questo documentoCopyright:
Formati disponibili
Netstat Comm
Caricato da
Mirza CerimCopyright:
Formati disponibili
From the man page of netstat netstat Print network connections, routing tables, interface
statistics, masquerade connections, and multicast memberships
Some examples with explanation
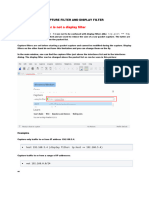
netstat -na
This display all active Internet connections to the server and only established connections are
included.
netstat -an | grep :80 | sort
Show only active Internet connections to the server on port 80, this is the http port and so its
useful if you have a web server, and sort the results. Useful in detecting a single flood by allowing
you to recognize many connections coming from one IP.
netstat -n -p|grep SYN_REC | wc -l
This command is useful to find out how many active SYNC_REC are occurring on the server. The
number should be pretty low, preferably less than 5. On DoS attack incidents or mail bombs, the
number can jump to pretty high. However, the value always depends on system, so a high value
may be average on another server.
netstat -n -p | grep SYN_REC | sort -u
List out the all IP addresses involved instead of just count.
netstat -n -p | grep SYN_REC | awk '{print $5}' | awk -F: '{print $1}'
List all the unique IP addresses of the node that are sending SYN_REC connection status.
netstat -ntu | awk '{print $5}' | cut -d: -f1 | sort | uniq -c | sort -n
Use netstat command to calculate and count the number of connections each IP address makes
to the server.
netstat -anp |grep 'tcp|udp' | awk '{print $5}' | cut -d: -f1 | sort | uniq -c | sort -n
List count of number of connections the IPs are connected to the server using TCP or UDP
protocol.
netstat -ntu | grep ESTAB | awk '{print $5}' | cut -d: -f1 | sort | uniq -c | sort -nr
Check on ESTABLISHED connections instead of all connections, and displays the connections
count for each IP.
netstat -plan|grep :80|awk {'print $5'}|cut -d: -f 1|sort|uniq -c|sort -nk 1
Show and list IP address and its connection count that connect to port 80 on the server. Port 80 is
used mainly by HTTP web page request.
How to mitigate a DOS attack
Once that you have found the IP that are attacking your server you can use the following
commands to block their connection to your server:
iptables -A INPUT 1 -s $IPADRESS -j DROP/REJECT
Please note that you have to replace $IPADRESS with the IP numbers that you have found with
netstat.
After firing the above command, KILL all httpd connections to clean your system and than restart
httpd service by
using the following commands:
killall -KILL httpd
service httpd start #For Red Hat systems
/etc/init/d/apache2 restart #For Debian systems
Potrebbero piacerti anche
- Are You Under A DoS or DDoS Attack - Find Out With Netstat !Documento4 pagineAre You Under A DoS or DDoS Attack - Find Out With Netstat !chinku85Nessuna valutazione finora
- Netstat Command and Its UsageDocumento10 pagineNetstat Command and Its Usageveera42Nessuna valutazione finora
- Linux Networking Cheat SheetDocumento2 pagineLinux Networking Cheat SheetFabiano MouraNessuna valutazione finora
- CS8581 Networks Lab Manual (R2017)Documento58 pagineCS8581 Networks Lab Manual (R2017)slogeshwariNessuna valutazione finora
- Networking ConnectivityDocumento19 pagineNetworking ConnectivityFlorie Capales-PelinNessuna valutazione finora
- Linux Ubuntu 12.04: Network Commands 2Documento14 pagineLinux Ubuntu 12.04: Network Commands 2harish sharmaNessuna valutazione finora
- Basic Network Commands LAB NAVADocumento20 pagineBasic Network Commands LAB NAVAuday kiranNessuna valutazione finora
- Ethical Hacking and Digital ForensicsDocumento92 pagineEthical Hacking and Digital ForensicsJanvi WaghmodeNessuna valutazione finora
- Iperf ManualDocumento13 pagineIperf ManualrtecnologiaNessuna valutazione finora
- Network Lab NewDocumento64 pagineNetwork Lab NewAnonymous sTUtKBbz67% (3)
- Nav CN 9Documento4 pagineNav CN 9Arshdeep SinghNessuna valutazione finora
- Firewall LinuxDocumento6 pagineFirewall LinuxDeepu MeackelNessuna valutazione finora
- Experiment No 9Documento10 pagineExperiment No 9sachinNessuna valutazione finora
- CN Assignment2Documento7 pagineCN Assignment2vedantmessi8Nessuna valutazione finora
- Netstat TutorialDocumento6 pagineNetstat TutorialAlex Moki100% (1)
- Windows Network Related CommandsDocumento7 pagineWindows Network Related Commandsmpscr100% (1)
- # Netstat - Ant - Grep 25Documento10 pagine# Netstat - Ant - Grep 25sravanNessuna valutazione finora
- Nimda (Code Blue) Virus: Problem DescriptionDocumento3 pagineNimda (Code Blue) Virus: Problem DescriptionVito KorleoneNessuna valutazione finora
- Backtrack 1Documento7 pagineBacktrack 1candrayusNessuna valutazione finora
- MikroTik Invisible ToolsDocumento66 pagineMikroTik Invisible ToolsAlex EnriquezNessuna valutazione finora
- ELearnSecurity ECPPT Notes ExamDocumento157 pagineELearnSecurity ECPPT Notes ExamAngel CabralesNessuna valutazione finora
- Sysadmin's Networking Cheat SheetDocumento2 pagineSysadmin's Networking Cheat SheetPriyansh SinghNessuna valutazione finora
- CN Lab RecordDocumento34 pagineCN Lab Recordkstorm11Nessuna valutazione finora
- DL 10 IptablesDocumento4 pagineDL 10 Iptablesdiptimehra1247Nessuna valutazione finora
- CN Assignment 2Documento6 pagineCN Assignment 2vedantmessi8Nessuna valutazione finora
- Window PC Ethernet CommandsDocumento3 pagineWindow PC Ethernet CommandsSatya PrakashNessuna valutazione finora
- CMD Commands, Also Used For Hacking Into Victims System: QuoteDocumento10 pagineCMD Commands, Also Used For Hacking Into Victims System: QuotecibigowthamNessuna valutazione finora
- CMD Commands HackingDocumento10 pagineCMD Commands Hackingsmoothysaidusharif78% (9)
- Backtrack 1Documento7 pagineBacktrack 1candrayusNessuna valutazione finora
- Testing Port Connectivity Reference GuideDocumento4 pagineTesting Port Connectivity Reference GuidedabaNessuna valutazione finora
- Computer Network Laboratory: Implement The Programs in JavaDocumento30 pagineComputer Network Laboratory: Implement The Programs in JavaShivani GajNessuna valutazione finora
- UNIX-Linux Netstat Command ExamplesDocumento12 pagineUNIX-Linux Netstat Command ExamplesAmar NeeluriNessuna valutazione finora
- 10 Iptables Rules To Help Secure Your Linux Box - TechRepublic PDFDocumento3 pagine10 Iptables Rules To Help Secure Your Linux Box - TechRepublic PDFozanalikayaNessuna valutazione finora
- Socket 2Documento20 pagineSocket 2myny BNessuna valutazione finora
- Wireshark Tcpdump CheatsheeetDocumento4 pagineWireshark Tcpdump CheatsheeetAnonymous (Akcent Hoong)Nessuna valutazione finora
- Network Scanning Using NmapDocumento6 pagineNetwork Scanning Using Nmapmillanu6275Nessuna valutazione finora
- Ping 2Documento15 paginePing 2ombidasarNessuna valutazione finora
- Networking Command: For Windows: 1. ARPDocumento24 pagineNetworking Command: For Windows: 1. ARPHemant PanwarNessuna valutazione finora
- Ping 2Documento15 paginePing 2charu73Nessuna valutazione finora
- Lab 3 ManualDocumento16 pagineLab 3 ManualDeep Narayan ChaudhuriNessuna valutazione finora
- CNE Tutorial 03 Wireshark Filter SyntaxDocumento8 pagineCNE Tutorial 03 Wireshark Filter SyntaxXuân Dương VươngNessuna valutazione finora
- Computer NetworksDocumento57 pagineComputer NetworksGouthami JukantiNessuna valutazione finora
- Enumeration Using NmapDocumento7 pagineEnumeration Using NmapFatema TahaNessuna valutazione finora
- w7 2 Lab10 Netstat Utility2 (NonCisco)Documento3 paginew7 2 Lab10 Netstat Utility2 (NonCisco)Jaden ZYNessuna valutazione finora
- Practical: - 1 Aim: - Execution of Basic TCP/IP Utilities and CommandsDocumento100 paginePractical: - 1 Aim: - Execution of Basic TCP/IP Utilities and CommandsAyushi SavaniNessuna valutazione finora
- Networking CommandDocumento12 pagineNetworking CommandDhruvik TankNessuna valutazione finora
- Monitoring Netflow With NfSenDocumento5 pagineMonitoring Netflow With NfSenThanhNN0312Nessuna valutazione finora
- Network CommandsDocumento4 pagineNetwork CommandsAli MohammadNessuna valutazione finora
- Check Network Connectivity Using Ping CommandDocumento9 pagineCheck Network Connectivity Using Ping CommandSopan sonarNessuna valutazione finora
- Netstat Ref UnixDocumento4 pagineNetstat Ref UnixBharanitharan SundaramNessuna valutazione finora
- Computer Networks, EC-803, Lab ManualDocumento24 pagineComputer Networks, EC-803, Lab ManualKaran SainiNessuna valutazione finora
- Describa Cada Uno de Los Siguientes Servicios y Mencione Su UtilidadDocumento6 pagineDescriba Cada Uno de Los Siguientes Servicios y Mencione Su UtilidadCamilo MedinaNessuna valutazione finora
- How To Troubleshoot Network Adapter Problems in WindowsDocumento41 pagineHow To Troubleshoot Network Adapter Problems in WindowsShivakumar S KadakalNessuna valutazione finora
- MoniterDocumento18 pagineMoniterapi-3798769Nessuna valutazione finora
- CN Lab ManualDocumento36 pagineCN Lab ManualSHREYAMS JAINNessuna valutazione finora
- CISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkDa EverandCISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkNessuna valutazione finora
- Network with Practical Labs Configuration: Step by Step configuration of Router and Switch configurationDa EverandNetwork with Practical Labs Configuration: Step by Step configuration of Router and Switch configurationNessuna valutazione finora
- WAN TECHNOLOGY FRAME-RELAY: An Expert's Handbook of Navigating Frame Relay NetworksDa EverandWAN TECHNOLOGY FRAME-RELAY: An Expert's Handbook of Navigating Frame Relay NetworksNessuna valutazione finora
- Primer 2. Kolokvijuma Iz Engleskog Jezika 2 (New Headway Pre-Intermediate, UNITS 7-12)Documento1 paginaPrimer 2. Kolokvijuma Iz Engleskog Jezika 2 (New Headway Pre-Intermediate, UNITS 7-12)Mirza CerimNessuna valutazione finora
- Checkpoint Test-Inside 156-215 80 v2020-09-23 by Mila 320q - QOnlyDocumento65 pagineCheckpoint Test-Inside 156-215 80 v2020-09-23 by Mila 320q - QOnlyMirza CerimNessuna valutazione finora
- NSE 3 CertificateDocumento1 paginaNSE 3 CertificateMirza CerimNessuna valutazione finora
- NSE4 - FGT-6.0 Februar 2020Documento64 pagineNSE4 - FGT-6.0 Februar 2020Mirza CerimNessuna valutazione finora
- Docker For Beginners Mumshad MannambethDocumento138 pagineDocker For Beginners Mumshad MannambethMirza Cerim100% (1)
- Activity 7.4.2 Challenge DHCP and NAT ConfigurationDocumento5 pagineActivity 7.4.2 Challenge DHCP and NAT ConfigurationMirza Cerim0% (1)
- Saray ResidenceDocumento1 paginaSaray ResidenceMirza CerimNessuna valutazione finora
- Restrict - Shutdown) Interface Subcommand: Security-Explained-With-Examples - HTMLDocumento1 paginaRestrict - Shutdown) Interface Subcommand: Security-Explained-With-Examples - HTMLMirza CerimNessuna valutazione finora
- Windows Server 2019 Product PresentationDocumento12 pagineWindows Server 2019 Product PresentationMirza CerimNessuna valutazione finora
- GT64 Terminal Datasheet R2-2Documento2 pagineGT64 Terminal Datasheet R2-2Relu123Nessuna valutazione finora
- 15 Towers - Deviation Sheet - 272000 - DATA COMMUNICATIONSDocumento3 pagine15 Towers - Deviation Sheet - 272000 - DATA COMMUNICATIONSLi LiuNessuna valutazione finora
- ZNC-514 Intelligent 14ch NMEA Combiner: User's ManualDocumento12 pagineZNC-514 Intelligent 14ch NMEA Combiner: User's ManualEvgeny YudinNessuna valutazione finora
- Perfil Anex MDocumento2 paginePerfil Anex MPazNessuna valutazione finora
- 642 785Documento56 pagine642 785Cristina JuravleNessuna valutazione finora
- Volte WPSDocumento24 pagineVolte WPSEfebmas 123Nessuna valutazione finora
- Midterm Paper Session 20-24Documento3 pagineMidterm Paper Session 20-24Syed Ali Abbas NaqviNessuna valutazione finora
- Ndpi - Quick Start Guide: Open and Extensible Lgplv3 Deep Packet Inspection LibraryDocumento15 pagineNdpi - Quick Start Guide: Open and Extensible Lgplv3 Deep Packet Inspection LibraryLinh Nguyễn VănNessuna valutazione finora
- InfographicDocumento1 paginaInfographicapi-473693776Nessuna valutazione finora
- Lab 1: Basic Router Configuration: Topology DiagramDocumento7 pagineLab 1: Basic Router Configuration: Topology DiagramDat LCNessuna valutazione finora
- 25-CCNP-Route BGP Route Reflectors and Route FiltersDocumento10 pagine25-CCNP-Route BGP Route Reflectors and Route Filterstouaiti2009Nessuna valutazione finora
- En NS2 ILM v20Documento199 pagineEn NS2 ILM v20Elquia MadridNessuna valutazione finora
- Cisco Commands Cheat Sheet PDFDocumento7 pagineCisco Commands Cheat Sheet PDFMd IrfANNessuna valutazione finora
- FMC and FTD Management NetworkDocumento48 pagineFMC and FTD Management NetworkSadiq Martin MbiyuNessuna valutazione finora
- Program'S Code & Name /: Kod Dan Nama ProgramDocumento8 pagineProgram'S Code & Name /: Kod Dan Nama ProgramhhubhgNessuna valutazione finora
- AOS-CX Simulator Lab - Spanning Tree Basics Lab GuideDocumento18 pagineAOS-CX Simulator Lab - Spanning Tree Basics Lab Guidetest testNessuna valutazione finora
- Biznet Internet Exchange - Community GuideDocumento5 pagineBiznet Internet Exchange - Community GuideAde RizkiawaludinNessuna valutazione finora
- Enarsi Chapter 10Documento31 pagineEnarsi Chapter 10kanthyadavNessuna valutazione finora
- B Cisco Nexus 9000 Series NX-OS Label Switching Configuration Guide 7x PDFDocumento154 pagineB Cisco Nexus 9000 Series NX-OS Label Switching Configuration Guide 7x PDFMao BourichaNessuna valutazione finora
- Asante FriendlyNET GX6-2400W-User ManualDocumento55 pagineAsante FriendlyNET GX6-2400W-User Manualichung819Nessuna valutazione finora
- Rubrik Complete Quick Start Guide DigitalDocumento1 paginaRubrik Complete Quick Start Guide DigitalCheap MethodNessuna valutazione finora
- 1b SDH OverviewDocumento50 pagine1b SDH OverviewGolam RasulNessuna valutazione finora
- PartDocumento3 paginePartShaina Marie JablaNessuna valutazione finora
- En Spec Tew-692gr (v1.0r)Documento3 pagineEn Spec Tew-692gr (v1.0r)Ioan AfodorceiNessuna valutazione finora
- UCCN2003 TCP/IP Internetworking UCCN2243 Internetworking Principles & PracticesDocumento10 pagineUCCN2003 TCP/IP Internetworking UCCN2243 Internetworking Principles & PracticesKahtheresh MuruganNessuna valutazione finora
- Dynamic Multipoint VPN (DMVPN) : Marc Khayat, CCIE #41288 Technical Manager, Cisco Networking AcademyDocumento6 pagineDynamic Multipoint VPN (DMVPN) : Marc Khayat, CCIE #41288 Technical Manager, Cisco Networking AcademyAmine InpticNessuna valutazione finora
- TR-4350 - FlexPod Express With Hyper-V Large ConfigurationDocumento82 pagineTR-4350 - FlexPod Express With Hyper-V Large ConfigurationPedro Daniel DVNessuna valutazione finora
- IP ServicesDocumento156 pagineIP ServicesNguyen HoangNessuna valutazione finora
- The Five Layer Network ModelDocumento32 pagineThe Five Layer Network ModelDaksh AilawadiNessuna valutazione finora
- UMTS Networks StandardizationDocumento10 pagineUMTS Networks StandardizationsurvivalofthepolyNessuna valutazione finora