Documenti di Didattica
Documenti di Professioni
Documenti di Cultura
An SSL Decryption 4035
Caricato da
Tryphon Tso-hunterTitolo originale
Copyright
Formati disponibili
Condividi questo documento
Condividi o incorpora il documento
Hai trovato utile questo documento?
Questo contenuto è inappropriato?
Segnala questo documentoCopyright:
Formati disponibili
An SSL Decryption 4035
Caricato da
Tryphon Tso-hunterCopyright:
Formati disponibili
Application Note
SSL Decryption
Introduction
SSL encryption is the cornerstone technology that makes the Internet secure. Email, e-commerce, voice-over-IP, online banking, remote
health, and countless other services are kept secure with SSL. Unfortunately, most of that traffic goes uninspected because many
security and performance monitoring tools lack the ability to see inside the encrypted sessions. Monitoring application performance
and network usage patterns becomes impossible if you cannot determine which applications are running over the network. Even worse,
malware can create SSL sessions to hide its activity, confident that security tools will neither inspect nor block the traffic. The very
technology that makes the Web secure can become a threat vector.
Decrypting SSL traffic requires knowledge of the keys used for encryption. The public keys are clearly visible at the start of the
transaction, but access to the private keys is controlled by the administrator.
Key Customer Applications
SSL Decryption is required for a variety of applications:
Malware Detection: Once malware exploits a host, it can complete the kill chain using SSL transactions
Data Loss Prevention: Whether initiated by malware or a user from inside the corporate firewall, confidential data and files can be
encrypted and leaked using SSL connections
Application Performance Monitoring: Key business applications use SSL to ensure authentication, but this obscures data required
for proper monitoring
Cloud Services Monitoring: Secure services running in the cloud, including Web applications, all look the same at the TCP/IP layer
and it is not until the SSL sessions are decrypted that they can be differentiated and monitored
Existing Solutions
SSL decryption is available directly on some monitoring tools. However, those solutions tend to cause a severe performance degradation
and are also very expensive. Offloading SSL decryption not only allows the tool to return to full performance, but also eliminates
the need to have multiple decryption licenses for multiple tools. Furthermore, SSL decryption on a specific security appliance, for
example, does not help with other tools, such as application performance monitoring; Gigamon can supply decrypted traffic to both
simultaneously. Clearly, by delivering SSL decryption as a common service to the connected monitoring and security tools, the overall
efficiency, security and performance of the infrastructure can be maximized.
Existing inline technologies, such as SSL proxies and application load balancers, provide SSL decryption, but they are not optimized for a
visibility architecture. They lack the scalability to handle traffic from multiple TAPs across the network or to filter and replicate decrypted
to multiple monitoring tools. With limited modularity or extensibility, increasing SSL throughput often requires new hardware. Lastly,
they provide no visibility functionality or traffic intelligence for non-encrypted traffic.
2014-2015 Gigamon. All rights reserved.
Application Note: SSL Decryption
Gigamon Solution
Given that Gigamons Unified Visibility Fabric has access to the bidirectional traffic, it has the ability to observe the exchange of public
keys at the start of the transaction. Once the administrator loads the private keys, they are securely stored on the system. The power
of the GigaSMART traffic intelligence engine can then decrypt the traffic and forward it to tools for analysis. Each GigaSMART module
contains high-performance compute engines that have hardware performance accelerators to handle SSL traffic.
SSL Decryption is not limited to specific ingress ports or where the GigaSMART engine is located within the Visibility Fabric. Any traffic
received on any network port in the cluster of Gigamon Visibility Fabric nodes can take advantage of SSL Decryption. And that traffic
can be sent to any tool ports in the cluster. This is an important attribute because not every node in the cluster needs to have the SSL
Decryption capability. Additional Flow Mapping technology and/or GigaSMART applications can also be applied to decrypted traffic.
Furthermore, additional SSL Decryption throughput can be achieved by adding more GigaSMART modules to the cluster, allowing
inspection to grow as SSL processing needs increase.
Because SSL traffic can contain sensitive user data, special care must be taken to ensure that this data remains secure. After decrypting
the packets, they can be sliced to remove irrelevant or private payload data. Alternatively, fields within the payload can be masked.
In both cases, private data is never stored, read, or analyzed by the monitoring tools. This helps keep networks within regulatory
compliance and greatly simplifies the auditing process.
Proper handling of the private keys is vital to maintain security compliance. Gigamon only allows keys to be uploaded, changed,
or deleted by users designated by the administrator. Keys are encrypted using a special password which is distinct from the generic
system admin password.
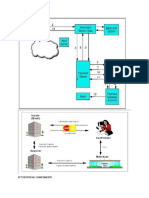
Figure 1: The steps to SSL Decryption
The Steps to SSL Decryption
3
2
Visibility Fabric
4
1. Tap the network and connect it to Gigamons
Visibility Fabric.
2. Select which flows to monitor and the
GigaSMART engine will identify the exchange
of public keys at the start of the transaction.
3. The private keys, which have been uploaded
by the administrator, are encrypted and stored
under tight password and role-based access controls.
4. GigaSMART then uses the private and public
keys to decrypt the SSL traffic.
5. The clear packets can be sent directly to your
monitoring tools or additional Flow Mapping
and GigaSMART operations can be applied.
2014-2015 Gigamon. All rights reserved.
Application Note: SSL Decryption
Key Features
First in the Industry to Integrate SSL Decryption into a Unified Visibility Fabric
Decrypt traffic from anywhere within the Visibility Fabric and send to any connected tools
With Flow Mapping technology, direct any user-defined flows, not just those on port 443, for decryption
SSL3, TLS 1.0, 1.1 and 1.2 Support
Public key: RSA
Symmetric key algorithms: AES, 3DES, DES, RC4, CAMELLIA, SEED, IDEA
Hashing algorithms: MD5, SHA1, SHA2
Supported applications: HTTPS, FTPS and SMTP, IMAP, POP3 with StartTLS
Supported key sizes: 128, 256, 512, 1024, 2048, and 4096
SSL Decryption Statistics
Idle sessions and reusable keys
Session-level Stats: packets, discards, errored packets, resumptions
Secure Storage of Private Keys
Encryption with independent password
Restricted key access based on role-based access controls
Key Benefits
Obtain Visibility to Encrypted Traffic
Enable malware detection, intrusion detection, data loss prevention, network forensics
Send clear traffic to application performance management, network performance monitoring, customer experience
management tools
Integrate SSL Inspection into a Multi-Tiered Security Solution
Prevent malware from hiding within uninspected SSL sessions
Forward any traffic that does not match known flows to GigaSMART for decryption
Decrypt traffic from the cloud and/or remote sites
Improve Tool Performance
Offload SSL Decryption to the Visibility Fabric, freeing tool resources for packet analysis
Apply decryption once for all tools rather than separately on each tool
Chain Multiple GigaSMART Applications Together
Terminate tunnels sent from GigaVUE-VM, remote sites, and/or ERSPAN
Apply Flow Mapping and SSL Decryption
Use Adaptive Packet Filtering for L7-based packet forwarding
Obscure private data with packet slicing or masking
2014-2015 Gigamon. All rights reserved.
Feature Brief: SSL Decryption
Physical
Web server connect
requests to NPM/CEM
Remote site
traffic to DLP
Virtual
Flow Mapping
GigaVUE-VM
SSL Decryption
Adaptive Packet
Filtering
Tunnel
Termination
GigaVUE-VM
East-West traffic between
virtual workloads to IPS
Visibility Fabric
Figure 2: Combine SSL Decryption with GigaSMART services such as tunnel de-encapsulation and Adaptive
Packet Filtering
Summary
SSL is a vital Internet technology upon which more and more applications will rely. However, it severely limits visibility for both
performance and security monitoring. The growing security threat posed by uninspected SSL sessions increases the urgency for
inspecting SSL traffic. By decrypting SSL traffic for out-of-band monitoring Gigamon provides visibility where none existed. Rather than
turning a blind eye to SSL traffic, the full capabilities of Flow Mapping technology and GigaSMART traffic intelligence can be applied.
Decrypting SSL is a tremendous processing burden for monitoring tools that do it themselves; this greatly inhibits tool performance
and increases the cost of monitoring. By supplying clear, decrypted traffic to multiple tools, Gigamon can be implemented to provide
immediate value and return on investment in capital expenditure, licensing fees, and management costs.
About Gigamon
Gigamon provides an intelligent Unified Visibility Fabric to enable the management of increasingly complex networks. Gigamon
technology empowers infrastructure architects, managers and operators with pervasive visibility and control of traffic across both
physical and virtual environments without affecting the performance or stability of the production network. Through patented
technologies, centralized management and a portfolio of high availability and high density fabric nodes, network traffic is intelligently
delivered to management, monitoring and security systems. Gigamon solutions have been deployed globally across enterprise, data
centers and service providers, including over half of the Fortune 100 and dozens of government and state and local agencies.
For more information about the Gigamon Unified Visibility Fabric visit: www.gigamon.com
2014-2015 Gigamon. All rights reserved. Gigamon and the Gigamon logo are trademarks of Gigamon in the United States and/or
other countries. Gigamon trademarks can be found at www.gigamon.com/legal-trademarks. All other trademarks are the trademarks
of their respective owners. Gigamon reserves the right to change, modify, transfer, or otherwise revise this publication without notice.
3300 Olcott Street, Santa Clara, CA 95054 USA | +1 (408) 831-4000 | www.gigamon.com
4035-03 07/15
Potrebbero piacerti anche
- 22 1 PDFDocumento33 pagine22 1 PDFInfluence Peddler IncNessuna valutazione finora
- Benchmemov2 01Documento64 pagineBenchmemov2 01Srijana RegmiNessuna valutazione finora
- Microwave Harassment & Mind-Control ExperimentationDocumento25 pagineMicrowave Harassment & Mind-Control ExperimentationScribdata95% (19)
- Peter Singer - Visible ManDocumento6 paginePeter Singer - Visible ManVictor Kumar100% (1)
- SSL VPN : Understanding, evaluating and planning secure, web-based remote accessDa EverandSSL VPN : Understanding, evaluating and planning secure, web-based remote accessNessuna valutazione finora
- Ata 23 Anti Hijack PDFDocumento14 pagineAta 23 Anti Hijack PDFAaron HarveyNessuna valutazione finora
- CCTV InstallationDocumento24 pagineCCTV InstallationMuhammad HabibieNessuna valutazione finora
- Securing .NET Web Services with SSL: How to Protect “Data in Transit” between Client and Remote ServerDa EverandSecuring .NET Web Services with SSL: How to Protect “Data in Transit” between Client and Remote ServerNessuna valutazione finora
- Cisco ASA V Palo Alto ComparisonDocumento1 paginaCisco ASA V Palo Alto ComparisonProdec_Networks100% (1)
- SSL Insight Hardening and Best Practices GuideDocumento16 pagineSSL Insight Hardening and Best Practices Guideradix82Nessuna valutazione finora
- Eacc Jobs AdvertDocumento39 pagineEacc Jobs AdvertLuke ShawNessuna valutazione finora
- JH143 - Shipyard Risk AssesmentDocumento5 pagineJH143 - Shipyard Risk AssesmentjgmjackNessuna valutazione finora
- Symantec SSL Visibility Appliance: Data SheetDocumento6 pagineSymantec SSL Visibility Appliance: Data SheetDebojit GoswamiNessuna valutazione finora
- SSL Visibility Appliance enDocumento4 pagineSSL Visibility Appliance enDebojit GoswamiNessuna valutazione finora
- Encrypted Threat Protection: White PaperDocumento7 pagineEncrypted Threat Protection: White PaperswsloanNessuna valutazione finora
- Bcs Ds SSL Visibility SV800-SV1800-SV2800-SV3800 en v4fDocumento3 pagineBcs Ds SSL Visibility SV800-SV1800-SV2800-SV3800 en v4fPrateek PorwalNessuna valutazione finora
- SSL Decryption - Uncovering The New Infrastructure Blind Spot - Gigamon WhitepaperDocumento6 pagineSSL Decryption - Uncovering The New Infrastructure Blind Spot - Gigamon WhitepaperGigamonNessuna valutazione finora
- The F5 SSL Orchestrator and Cisco Firepower SolutionDocumento39 pagineThe F5 SSL Orchestrator and Cisco Firepower Solutionalways_redNessuna valutazione finora
- SSL VPN CheckpointDocumento24 pagineSSL VPN CheckpointTruong LanNessuna valutazione finora
- F5 SSL Orchestrator and Symantec DLP: SSL Visibility and Content AdaptionDocumento26 pagineF5 SSL Orchestrator and Symantec DLP: SSL Visibility and Content Adaptionalways_redNessuna valutazione finora
- The F5 SSL Orchestrator and Palo Alto Networks Next-Gen Firewall SolutionDocumento39 pagineThe F5 SSL Orchestrator and Palo Alto Networks Next-Gen Firewall Solutionalways_redNessuna valutazione finora
- F5 SSL Orchestrator and Fireeye NX: SSL Visibility With Service ChainingDocumento20 pagineF5 SSL Orchestrator and Fireeye NX: SSL Visibility With Service Chainingalways_redNessuna valutazione finora
- Pa 3200 SeriesDocumento4 paginePa 3200 SeriesJackkyz RockkerzNessuna valutazione finora
- Decryption Why Where and HowDocumento6 pagineDecryption Why Where and HowfanvantanNessuna valutazione finora
- Decrypting SSL/TLS Traffic For Hidden Threats Detection: Conference PaperDocumento5 pagineDecrypting SSL/TLS Traffic For Hidden Threats Detection: Conference Paperlai khoiNessuna valutazione finora
- PA-5200 Series: HighlightsDocumento4 paginePA-5200 Series: HighlightsvlimbadiNessuna valutazione finora
- Pa 5200 SeriesDocumento4 paginePa 5200 Serieszain jamalNessuna valutazione finora
- pa-7500Documento5 paginepa-7500sonyalmafittNessuna valutazione finora
- Ixia-SV-WP-Role of Active SSL DecryptionDocumento7 pagineIxia-SV-WP-Role of Active SSL Decryptionliuyq7809Nessuna valutazione finora
- Highlights: by Palo Alto Networks - PA-220 - DatasheetDocumento4 pagineHighlights: by Palo Alto Networks - PA-220 - DatasheetvlimbadiNessuna valutazione finora
- Security ProtocolsDocumento4 pagineSecurity Protocolsapi-3701346Nessuna valutazione finora
- Bcs Ds BlueCoat Encrypted TAP en v1dDocumento2 pagineBcs Ds BlueCoat Encrypted TAP en v1dNancy DrewerNessuna valutazione finora
- Advanced Firewall 2016 Web enDocumento3 pagineAdvanced Firewall 2016 Web enAlberto FernandezNessuna valutazione finora
- Zcertificate Intelligence Center DatasheetDocumento3 pagineZcertificate Intelligence Center Datasheetcharanmann9165Nessuna valutazione finora
- pa-3400-seriesDocumento7 paginepa-3400-seriessonyalmafittNessuna valutazione finora
- Pa 3200 SeriesDocumento4 paginePa 3200 SeriesBatkhishig Tumen-OidovNessuna valutazione finora
- Ipsec and SSL VPN Deployment Considerations: in This DocumentDocumento8 pagineIpsec and SSL VPN Deployment Considerations: in This DocumentGiorgos FotopoulosNessuna valutazione finora
- pa-5450-seriesDocumento7 paginepa-5450-seriessonyalmafittNessuna valutazione finora
- Pa 5200 SeriesDocumento4 paginePa 5200 SeriesAlberto Huamani CanchizNessuna valutazione finora
- Pa 800 DatasheetDocumento4 paginePa 800 DatasheettxNessuna valutazione finora
- E-Commerce Security Best PracticesDocumento19 pagineE-Commerce Security Best PracticesNess Wadia College of Coomerce PuneNessuna valutazione finora
- SecureSpan SOA Gateway Gateway & Software AGDocumento4 pagineSecureSpan SOA Gateway Gateway & Software AGLayer7TechNessuna valutazione finora
- Pa 800Documento4 paginePa 800Batkhishig Tumen-OidovNessuna valutazione finora
- Best Practices DecryptionDocumento5 pagineBest Practices DecryptionPartha DashNessuna valutazione finora
- Pa 220Documento4 paginePa 220Abel De Los SantosNessuna valutazione finora
- SSL Offloading Relieves Server CPU LoadDocumento2 pagineSSL Offloading Relieves Server CPU Loadsyed_engrNessuna valutazione finora
- Architecture, Design, Data Storage and Network RequirementsDocumento27 pagineArchitecture, Design, Data Storage and Network RequirementsThuy PhamNessuna valutazione finora
- Pa 5200 SeriesDocumento6 paginePa 5200 SeriesnnNessuna valutazione finora
- CISSP Revision NotesDocumento36 pagineCISSP Revision NotesAman DeepNessuna valutazione finora
- Mobile App Security Checklist enDocumento30 pagineMobile App Security Checklist enTalo NguyenNessuna valutazione finora
- Secure Networking 101 MACsec, IPsec, and SSL BasicsDocumento10 pagineSecure Networking 101 MACsec, IPsec, and SSL BasicsazertyNessuna valutazione finora
- Mobile App Security Checklist EsDocumento30 pagineMobile App Security Checklist EsIsrael FloresNessuna valutazione finora
- Pa 5400 SeriesDocumento6 paginePa 5400 Seriesw.meloNessuna valutazione finora
- Globalprotect Cloud Service DsDocumento4 pagineGlobalprotect Cloud Service DssasNessuna valutazione finora
- Sa Series SSL VPN AppliancesDocumento12 pagineSa Series SSL VPN AppliancesYeng Yee NgNessuna valutazione finora
- Transport Layer Protection Cheat SheetDocumento6 pagineTransport Layer Protection Cheat SheetRoman PotapovNessuna valutazione finora
- Mobile App Security Checklist enDocumento30 pagineMobile App Security Checklist enHiko KikoNessuna valutazione finora
- Pa 5200 SeriesDocumento6 paginePa 5200 SeriesJonathan QuilacioNessuna valutazione finora
- Secure Socket LayerDocumento14 pagineSecure Socket LayerbetoplapaNessuna valutazione finora
- Blue Coat Product OverviewDocumento6 pagineBlue Coat Product OverviewBrijesh BhatiyaNessuna valutazione finora
- Ssl/Tls Trends, Practices, and Futures: Brian A. Mchenry, Security Solutions Architect @bamchenryDocumento34 pagineSsl/Tls Trends, Practices, and Futures: Brian A. Mchenry, Security Solutions Architect @bamchenryDhananjai SinghNessuna valutazione finora
- Firewall Features Overview PDFDocumento5 pagineFirewall Features Overview PDFElliott longNessuna valutazione finora
- Security in e - CommerceDocumento4 pagineSecurity in e - CommerceAlex T BinoyNessuna valutazione finora
- Achieve High-Performance SSL Visibility and Inspection With FortiadcDocumento3 pagineAchieve High-Performance SSL Visibility and Inspection With Fortiadclai khoiNessuna valutazione finora
- Mpki SSL Services Agreement Service Description PDFDocumento15 pagineMpki SSL Services Agreement Service Description PDFDlablo Auguts ThabluechaiNessuna valutazione finora
- Secure Data Exchange Via HSMDocumento3 pagineSecure Data Exchange Via HSMLayer7TechNessuna valutazione finora
- Oil Gas Industry Solution BriefDocumento3 pagineOil Gas Industry Solution BriefZahra GhNessuna valutazione finora
- Bank Reduces Security Threats by Using SSL DecryptionDocumento4 pagineBank Reduces Security Threats by Using SSL Decryptionlai khoiNessuna valutazione finora
- Inner Class in JavaDocumento15 pagineInner Class in JavaTryphon Tso-hunterNessuna valutazione finora
- A Design Oscillator Baed PUF On FPGADocumento6 pagineA Design Oscillator Baed PUF On FPGATryphon Tso-hunterNessuna valutazione finora
- Lab5 Zybo XilinxDocumento10 pagineLab5 Zybo XilinxTryphon Tso-hunterNessuna valutazione finora
- State-Of-cybersecurity Res Eng 0316Documento23 pagineState-Of-cybersecurity Res Eng 0316Tryphon Tso-hunterNessuna valutazione finora
- A Robust and Efficient Detection Model of DDoS Attack For Cloud ServicesDocumento14 pagineA Robust and Efficient Detection Model of DDoS Attack For Cloud ServicesTryphon Tso-hunterNessuna valutazione finora
- The Walrasian Output Beats The MarketsDocumento4 pagineThe Walrasian Output Beats The MarketsTryphon Tso-hunterNessuna valutazione finora
- VN Enisa Stage 2015 01Documento4 pagineVN Enisa Stage 2015 01Tryphon Tso-hunterNessuna valutazione finora
- εισαγωγή στην θεωρία του ρίσκουDocumento20 pagineεισαγωγή στην θεωρία του ρίσκουTryphon Tso-hunterNessuna valutazione finora
- Eu DirectiveDocumento3 pagineEu DirectiveTryphon Tso-hunterNessuna valutazione finora
- Social Semiotics History Is Never SureDocumento11 pagineSocial Semiotics History Is Never SureTryphon Tso-hunterNessuna valutazione finora
- νομισματική θεωρία και πολιτική μέρος βDocumento15 pagineνομισματική θεωρία και πολιτική μέρος βTryphon Tso-hunterNessuna valutazione finora
- Mobile Threat Detection SolutionDocumento2 pagineMobile Threat Detection SolutionAngel Hernando MartinezNessuna valutazione finora
- Cybercrime Moot Court Competition Problem: Cyberlaw UniversityDocumento9 pagineCybercrime Moot Court Competition Problem: Cyberlaw UniversityNehaNessuna valutazione finora
- CCTV System For Barangay San Miguel, Calumpit and Barangay Tibig, Bulakan, BulacanDocumento9 pagineCCTV System For Barangay San Miguel, Calumpit and Barangay Tibig, Bulakan, Bulacananon_726913799Nessuna valutazione finora
- CCTV Fight Classification Final Year ProjectDocumento54 pagineCCTV Fight Classification Final Year ProjectSamreen TabbasamNessuna valutazione finora
- Doc22 PDFDocumento78 pagineDoc22 PDFAmelia BrownNessuna valutazione finora
- EcardDocumento3 pagineEcardsatendra singhNessuna valutazione finora
- Mariel García-Montes, "Just Say No To 'Just Say No': Tensions in Organizational Approaches To Youth and Online Privacy in The Americas"Documento113 pagineMariel García-Montes, "Just Say No To 'Just Say No': Tensions in Organizational Approaches To Youth and Online Privacy in The Americas"MIT Comparative Media Studies/WritingNessuna valutazione finora
- Elbit Systems MSVDocumento2 pagineElbit Systems MSVWellNessuna valutazione finora
- Note: Dsc/Esign Is Not Required in Case of Verified AadhaarDocumento3 pagineNote: Dsc/Esign Is Not Required in Case of Verified AadhaarPatel PraweenNessuna valutazione finora
- 4 Undertaking SecurityDocumento3 pagine4 Undertaking SecurityMukund2288Nessuna valutazione finora
- Chapter 33 UpdateDocumento5 pagineChapter 33 UpdateArs TechnicaNessuna valutazione finora
- MND TecopDocumento4 pagineMND TecopHAMIZAN HUDYNessuna valutazione finora
- 1 Module 1 Working Within The Private Security Industry StudentDocumento32 pagine1 Module 1 Working Within The Private Security Industry StudentCelebrul DanNessuna valutazione finora
- Qualitas Global Company Presentation 2020Documento23 pagineQualitas Global Company Presentation 2020Siddharth BoseNessuna valutazione finora
- Entrepreneurial Resources 2016Documento134 pagineEntrepreneurial Resources 2016Nacho Alonso LNessuna valutazione finora
- Carlisle Police Chief Stephen Margeson's ReportDocumento20 pagineCarlisle Police Chief Stephen Margeson's ReportTherese UmerlikNessuna valutazione finora
- SIFANG Renewable Energy Automation Solutions CatalogDocumento36 pagineSIFANG Renewable Energy Automation Solutions CatalogDaniel LeeNessuna valutazione finora
- Data SecurityDocumento8 pagineData SecurityFRANCIS VIKNESHRAJ DNessuna valutazione finora
- Acknowledgement 1664110973193Documento4 pagineAcknowledgement 1664110973193CoRRex GaMingNessuna valutazione finora
- Avtech Cms User Manual v0.1bnvr CCTVDocumento81 pagineAvtech Cms User Manual v0.1bnvr CCTVfritzfmpNessuna valutazione finora
- Authorization Letter for Digital Signature CertificateDocumento1 paginaAuthorization Letter for Digital Signature CertificateChimakurthy NagarapanchayatNessuna valutazione finora
- PP Tream PaperDocumento22 paginePP Tream PapersufyanNessuna valutazione finora