Documenti di Didattica
Documenti di Professioni
Documenti di Cultura
LABSEC-2020 ASA 8.3 (Or Higher) Lab Guide PDF
Caricato da
Riadh Madhour0 valutazioniIl 0% ha trovato utile questo documento (0 voti)
119 visualizzazioni11 pagineThis document provides instructions for two exercises on a Cisco ASA firewall. The first exercise has students configure static and dynamic NAT to allow HTTP and FTP access to a web server while denying other traffic. The second exercise covers configuring authentication for firewall sessions using AAA. The exercises provide terminology, background information, requirements, step-by-step instructions, and tips for troubleshooting problems.
Descrizione originale:
Titolo originale
LABSEC-2020 ASA 8.3 (or higher) Lab Guide.pdf
Copyright
© © All Rights Reserved
Formati disponibili
PDF, TXT o leggi online da Scribd
Condividi questo documento
Condividi o incorpora il documento
Hai trovato utile questo documento?
Questo contenuto è inappropriato?
Segnala questo documentoThis document provides instructions for two exercises on a Cisco ASA firewall. The first exercise has students configure static and dynamic NAT to allow HTTP and FTP access to a web server while denying other traffic. The second exercise covers configuring authentication for firewall sessions using AAA. The exercises provide terminology, background information, requirements, step-by-step instructions, and tips for troubleshooting problems.
Copyright:
© All Rights Reserved
Formati disponibili
Scarica in formato PDF, TXT o leggi online su Scribd
0 valutazioniIl 0% ha trovato utile questo documento (0 voti)
119 visualizzazioni11 pagineLABSEC-2020 ASA 8.3 (Or Higher) Lab Guide PDF
Caricato da
Riadh MadhourThis document provides instructions for two exercises on a Cisco ASA firewall. The first exercise has students configure static and dynamic NAT to allow HTTP and FTP access to a web server while denying other traffic. The second exercise covers configuring authentication for firewall sessions using AAA. The exercises provide terminology, background information, requirements, step-by-step instructions, and tips for troubleshooting problems.
Copyright:
© All Rights Reserved
Formati disponibili
Scarica in formato PDF, TXT o leggi online su Scribd
Sei sulla pagina 1di 11
LABSEC-2020
Troubleshooting Cisco ASA 8.3 (or higher)
Firewall Capabilities
Lab Guide
1
Table of Contents
Lab Overview ................................................................................................................................................ 2
Prerequisites: ............................................................................................................................................ 2
How to Access Your Lab ................................................................................................................................ 2
Network Topology ..................................................................................................................................... 3
Access Information for your POD: ............................................................................................................ 3
Exercise 1: Configuring and Troubleshooting Basic NAT and Access Control ............................................... 5
Terminology .............................................................................................................................................. 5
Some Background Information About NAT .................................................................................................. 5
Requirements and Steps to Complete ...................................................................................................... 6
Helpful Steps If (When) You Run Into Problems ....................................................................................... 6
Exercise 2: Configuring and Troubleshooting Authentication For Firewall Sessions .................................... 9
Terminology .............................................................................................................................................. 9
Some Background Information About AAA .................................................................................................. 9
Requirements and Steps to Complete ...................................................................................................... 9
Helpful Steps If (When) You Run Into Problems ..................................................................................... 10
2
Lab Overview
In this lab participants will learn basic troubleshooting skills and techniques for diagnosing and fixing
network problems on Cisco Adaptive Security Appliance (ASA). Troubleshooting concepts and tools are
introduced by completing step-by-step lab scenarios. Students will work individually with a dedicated
lab pod containing containing the latest version of Cisco ASA Software.
Prerequisites:
Must understand firewall basics.
Must understand IP routing.
Must know how to perform basic configuration Cisco ASA via CLI or ASDM. This lab assumes that
you already know how to configure basic NAT, access control, and routing in the Cisco ASA.
If further information is needed on these topics, refer to: http://www.cisco.com/go/asa
How to Access Your Lab
This section describes how to access the lab setup and provides the addressing connections and port
scheme information for your POD.
This section describes the following:
Network Topology
Access Information
3
Network Topology
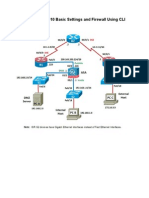
The following diagram (Figure 1) shows the network topology and setup for this lab. Your POD
information will be provided to you by the instructor/lab proctor.
Figure 1. Network Topology
Access Information for your POD:
Step 1. Using your assigned lab PC launch a remote desktop client
a. Start-> Run: mstsc.exe
b. If you are Pod 1-8, then connect to computer: 64.102.242.76:10000
c. If you are Pod 9-16 then connect to computer 64.102.242.77:10000
d. Use podXuser and podXpass for credentials, where X is your assigned pod number.
Step 2. ASDM should already be installed and have a shortcut on your desktop, launch it and
connect to 209.165.201.X, where X is your pod number.
Step 3. Alternatively, login to the ASA via SSH (i.e., using Putty).
Step 4. Login into the ASA using the following credentials:
a. Username: ciscolive
b. Password: ciscolive
4
After logging into the security appliance, make sure that it is running version 8.4, as shown below in
Figure 2:
Figure 2. Cisco ASA Version Information
Alternatively, you use the show version CLI command.
5
Exercise 1: Configuring and Troubleshooting Basic NAT and Access
Control
Terminology
This document uses the following terminology:
Real address/host/network/interface The real address is the address that is defined on the
host, before it is translated. In a typical NAT scenario where you want to translate the inside
network when it accesses the outside, then the inside network would be the "real" network.
Note that you can translate any network connected to the adaptive security appliance, not just
an inside network, Therefore if you configure NAT to translate outside addresses, "real" can
refer to the outside network when it accesses the inside network.
Mapped address/host/network/interface The mapped address is the address that the real
address is translated to. In a typical NAT scenario where you want to translate the inside
network when it accesses the outside, then the outside network would be the "mapped"
network.
Bidirectional initiation Static NAT allows connections to be initiated bidirectionally, meaning
both to the host and from the host.
Source and destination NAT For any given packet, both the source and destination IP
addresses are compared to the NAT rules, and one or both can be translated/untranslated.
Some Background Information About NAT
Each computer and device within an IP network is assigned a unique IP address that identifies the host.
Because of a shortage of public IPv4 addresses, most of these IP addresses are private, not routable
anywhere outside of the private company network. One of the main functions of NAT is to enable
private IP networks to connect to the Internet. NAT replaces a private IP address with a public IP
address, translating the private addresses in the internal private network into routable addresses that
can be used on the public Internet.
You can implement NAT using the following methods:
Static NATA consistent mapping between a real and mapped IP address. Allows bidirectional
traffic initiation.
Dynamic NATA group of real IP addresses are mapped to a (usually smaller) group of mapped
IP addresses, on a first come, first served basis. Only the real host can initiate traffic.
Dynamic Port Address Translation (PAT)A group of real IP addresses are mapped to a single IP
address using a unique source port of that IP address.
6
Identity NATStatic NAT lets you translate a real address to itself, essentially bypassing NAT.
You might want to configure NAT this way when you want to translate a large group of
addresses, but then want to exempt a smaller subset of addresses.
Requirements and Steps to Complete
A fictitious company called SecureMe is used in this lab as an example. You are now the firewall
administrator for SecureMe and must configure a new ASA to allow Web (HTTP) and FTP traffic to the
Web/FTP server shown in the network topology (Figure 1). The following are the requirements:
1. The Web/FTP server IP address (192.168.2.102) must be statically translated to the outside IP
address of 209.165.201.2XX ( XX = your POD number; for example, POD 1 will be
209.165.201.201; POD 2 will be 209.165.201.202; etc.)
2. Allow only Web (HTTP) and FTP traffic to the server.
3. All other inbound traffic must be denied.
4. All other inside hosts should be dynamically translated to the Cisco ASAs outside interfaces IP
address when accessing the Internet.
IMPORTANT: In Cisco ASA Software version 8.3(1) and later the NAT configuration was completely
redesigned to allow greater flexibility and ease of use. You can now create named network objects that
you can use in place of a host, a subnet, or a range of IP addresses in your configuration and named
service objects that you can use in place of a protocol and port in your configuration. You can then
change the object definition in one place, without having to change any other part of your configuration.
This lab uses Cisco ASA Software version 8.4 which has support for network and service objects, use
them appropriately. There is another lab that uses version 8.2, where you can use the legacy nat and
static commands.
Helpful Steps If (When) You Run Into Problems
You will most definitely run into problems in this lab. Do not assume that everything will work as
expected. The following are some helpful tips if you run into problems.
Step 1. Can you access the server using web browser (over TCP port 80)?
Step 2. Can you access the server via FTP using the CLI? If not, can you telnet to the FTP server
on port 21? (tip: you can use Putty to telnet on port 21).
Step 3. Issue the show xlate command. How do you see?
___________________________________________________________
7
Step 4. Issue the show conn command. How many connections are in use?
___________________________________________________________
Step 5. What are the connection flags?
___________________________________________________________
Step 6. What do the connection flags indicate?
___________________________________________________________
Step 7. Issue the show perfmon command. What do you notice?
___________________________________________________________
Step 8. Enable syslog to the internal buffer at debug level. Then view the syslogs.
What do you see? (commands: logging enable; logging buffered debugging; show log)
___________________________________________________________
Step 9. Enable packet capture on the outside interface, then view the capture.
What do you see? (commands: capture out interface outside, show capture out)
___________________________________________________________
Step 10. Enable packet capture on the inside interface, then view the capture. What do you see?
(commands: capture in interface inside, show capture in)
___________________________________________________________
Step 11. Specifically, what are the source IP addresses?
___________________________________________________________
8
Step 12. What is the destination IP?
___________________________________________________________
Step 13. What does this tell you about what is happening?
___________________________________________________________
9
Exercise 2: Configuring and Troubleshooting Authentication For Firewall
Sessions
Terminology
This section uses the following terminology:
AAA Authentication, Authorization, and Accounting. AAA enables the adaptive security
appliance to determine who the user is (authentication), what the user can do (authorization),
and what the user did (accounting).
Some Background Information About AAA
The Cisco ASA uses "cut-through proxy" to significantly improve performance compared to a traditional
proxy server. Although you can configure the Cisco ASA to require authentication for network access to
any protocol or service, users can authenticate directly with HTTP, HTTPS, Telnet, or FTP only. A user
must first authenticate with one of these services before the adaptive security appliance allows other
traffic requiring authentication. The authentication ports that the adaptive security appliance supports
for AAA are fixed as follows:
Port 21 for FTP
Port 23 for Telnet
Port 80 for HTTP
Port 443 for HTTPS
After you authenticate correctly, the adaptive security appliance redirects you to your original
destination. If the destination server also has its own authentication, the user enters another username
and password. If you use basic HTTP authentication and need to enter another username and password
for the destination server, then you need to configure the virtual http command.
Requirements and Steps to Complete
SecureMe has a new requirement. You must configure the Cisco ASA to authenticate all outside users
connecting to the web server. The following are the requirements:
1. All outside users must be authenticated before connecting to the web server.
2. External authentication using RADIUS must be used. You must not configure the Cisco ASA to
perform authentication using its local database.
10
Helpful Steps If (When) You Run Into Problems
You will most definitely run into problems in this lab. Do not assume that everything will work as
expected. The following are some helpful tips if you run into problems. Be aware that we expect that
you already know how to configure the Cisco ASA for authentication; the following are some
configuration and troubleshooting tips.
Step 1. Verify that you can still access the web server using web browser (over TCP port 80)
before you configure and enable authentication.
Step 2. Configure authentication. Using the aaa-server command, identify your AAA servers. If
you have already identified your AAA servers, continue to the next step. Since the server is located
toward the inside interface, select inside interface and specify the IP address of the server
(192.168.2.101). The server secret key is ciscolive.
Step 3. Using the access-list command, create an access list that identifies the source addresses
and destination addresses of traffic you want to authenticate. The permit ACEs mark matching
traffic for authentication, while deny entries exclude matching traffic from authentication. Be sure
to include the destination port for HTTP in the access list because the user must authenticate with
this service before traffic to the web server is allowed through the ASA.
Step 4. Use the aaa authentication match command to enable authentication and match the
ACL you just configured.
Step 5. Test your connection to the web server from the outside client. Do you get a prompt for
authentication?
Step 6. If you do, enter podXuser as the username and podXpass as the password.
Step 7. If not, enable debug aaa authentication. What do you see?
_________________________________________________________________________
Step 8. Enable debug radius. Does this give you more information? If so, what do you see?
_________________________________________________________________________
Step 9. What do you think thats wrong?
_________________________________________________________________________
Potrebbero piacerti anche
- Adhoc Mobile Wireless Network Enhancement Based On Cisco DevicesDocumento7 pagineAdhoc Mobile Wireless Network Enhancement Based On Cisco DeviceslakhanNessuna valutazione finora
- Ccnasv1.1 Chp10 Lab-A Asa-Fw-Cli Instructor 8.25.37 Am 8.25.57 AmDocumento35 pagineCcnasv1.1 Chp10 Lab-A Asa-Fw-Cli Instructor 8.25.37 Am 8.25.57 Amclearmoon247100% (2)
- Type The Document SubtitleDocumento12 pagineType The Document SubtitleRaj KumarNessuna valutazione finora
- CCNP Security Secure Lab GuideDocumento150 pagineCCNP Security Secure Lab Guidebkaraqa67% (3)
- SECURE10LGDocumento150 pagineSECURE10LGAzzafirNessuna valutazione finora
- 11.3.4.6 Lab - Using The CLI To Gather Network Device InformationDocumento11 pagine11.3.4.6 Lab - Using The CLI To Gather Network Device InformationRazvan Buicliu0% (4)
- Report 1Documento28 pagineReport 1zeeshan sohailNessuna valutazione finora
- 640-822 Certkiller Questions and Answers: Number: 640-822 Passing Score: 825 Time Limit: 120 Min File Version: 16.8Documento130 pagine640-822 Certkiller Questions and Answers: Number: 640-822 Passing Score: 825 Time Limit: 120 Min File Version: 16.8ﻣﺤﻤﺪ ﻭﻫﻴﺐ ﺍﻟﻌﺒﺴﻲNessuna valutazione finora
- Configuring ASA 5510 Basic Settings and Firewall Using CLIDocumento18 pagineConfiguring ASA 5510 Basic Settings and Firewall Using CLIIrfee75% (8)
- Teste Cisco 640-822Documento241 pagineTeste Cisco 640-822kappa_gNessuna valutazione finora
- Ethernet CablingDocumento8 pagineEthernet CablingOctav EnachiNessuna valutazione finora
- 11.3.4.6 Lab - Using The CLI To Gather Network Device InformationDocumento8 pagine11.3.4.6 Lab - Using The CLI To Gather Network Device InformationSuen Clarke0% (1)
- DHCP and Nat LabDocumento4 pagineDHCP and Nat LabingjaabNessuna valutazione finora
- Cisco Spiad - Labv1.3.1Documento91 pagineCisco Spiad - Labv1.3.1fernando JmzNessuna valutazione finora
- CNE Tutorial 02 - Real - LAN and LAN With Packet TracerDocumento18 pagineCNE Tutorial 02 - Real - LAN and LAN With Packet TracerThơm VũNessuna valutazione finora
- A Wireless LAN Hot SpotDocumento8 pagineA Wireless LAN Hot SpotMugluuNessuna valutazione finora
- Cisco Networking All-In-One For Dummies Cheat Sheet - For DummiesDocumento9 pagineCisco Networking All-In-One For Dummies Cheat Sheet - For DummiesGermain DgermainNessuna valutazione finora
- Network Devices & Packet Tracer Objectives:: A Router Also IncludesDocumento27 pagineNetwork Devices & Packet Tracer Objectives:: A Router Also IncludesHunter BunterNessuna valutazione finora
- Amandeep SinghDocumento15 pagineAmandeep SinghDeepak DeepNessuna valutazione finora
- 11.3.4.6 Lab - Using The CLI To Gather Network Device InformationDocumento8 pagine11.3.4.6 Lab - Using The CLI To Gather Network Device InformationSachinNessuna valutazione finora
- Lab05 - Configuring ASA Basic Settings and Firewall Using CLIDocumento26 pagineLab05 - Configuring ASA Basic Settings and Firewall Using CLIAdrián ChóezNessuna valutazione finora
- CN AssignDocumento20 pagineCN AssigngortifelteNessuna valutazione finora
- Lab 1151Documento20 pagineLab 1151Kiri RaveendrarasaNessuna valutazione finora
- PfSense FW-7551 Quick Start Guide 7-18-14Documento15 paginePfSense FW-7551 Quick Start Guide 7-18-14dionisionietoNessuna valutazione finora
- Lab 10: IDPS - Snort & Cisco IDPS Sensors: 9.1 DetailsDocumento24 pagineLab 10: IDPS - Snort & Cisco IDPS Sensors: 9.1 DetailsewNessuna valutazione finora
- 1.3.1.3 Packet Tracer - Skills Integration Challenge InstructionsDocumento4 pagine1.3.1.3 Packet Tracer - Skills Integration Challenge InstructionsCorie White17% (6)
- Ccnasv1.1 Chp10 Lab-B Asa-fw-Asdm Instructor 8.25.37 Am 8.25.57 AmDocumento52 pagineCcnasv1.1 Chp10 Lab-B Asa-fw-Asdm Instructor 8.25.37 Am 8.25.57 Amclearmoon247Nessuna valutazione finora
- Lab 1.3.1Documento12 pagineLab 1.3.1Alondra CarmonaNessuna valutazione finora
- 11.3.4.6 Lab - Using The CLI To Gather Network Device Information - ILMDocumento14 pagine11.3.4.6 Lab - Using The CLI To Gather Network Device Information - ILMKevin KimNessuna valutazione finora
- Cisco - Configuring NATDocumento7 pagineCisco - Configuring NATFrancisco Javie Ortega ÑNessuna valutazione finora
- Configuring NAT Pool Overload and PATDocumento6 pagineConfiguring NAT Pool Overload and PATahaj94Nessuna valutazione finora
- PIX/ASA: Establish and Troubleshoot Connectivity Through The Cisco Security ApplianceDocumento7 paginePIX/ASA: Establish and Troubleshoot Connectivity Through The Cisco Security AppliancetsibiNessuna valutazione finora
- 9.3.2.13 Lab - Configuring and Verifying Extended ACLsDocumento8 pagine9.3.2.13 Lab - Configuring and Verifying Extended ACLsAnonymous cW6o4f886% (14)
- 5.1.2.6 Investigating NAT OperationDocumento16 pagine5.1.2.6 Investigating NAT OperationCristianFelipeSolarteOrozcoNessuna valutazione finora
- Configure Network Address Translation - CiscoDocumento13 pagineConfigure Network Address Translation - CiscoFederacion Hip Hop DominicanaNessuna valutazione finora
- Cisco Pass4Sure 640-822 v2013-05-02 by FadiDocumento155 pagineCisco Pass4Sure 640-822 v2013-05-02 by FadiIris DebergesNessuna valutazione finora
- Configure Network Address TranslationDocumento10 pagineConfigure Network Address Translationunidad patrimonialNessuna valutazione finora
- Mini-Lab - Student GuideDocumento14 pagineMini-Lab - Student GuideDiego Fernando Solis H100% (1)
- Csc261 CCN Lab ManualDocumento125 pagineCsc261 CCN Lab ManualasadhppyNessuna valutazione finora
- 11.3.4.6 Lab - Using The CLI To Gather Network Device InformationDocumento11 pagine11.3.4.6 Lab - Using The CLI To Gather Network Device InformationRuy Pequeno CidNessuna valutazione finora
- Lab6 - 2 CiscoDocumento8 pagineLab6 - 2 CiscoMoussa MarNessuna valutazione finora
- CISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkDa EverandCISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkNessuna valutazione finora
- Building Your Own Free Home Phone System With Mikrotik: Expanding PossibilitiesDocumento44 pagineBuilding Your Own Free Home Phone System With Mikrotik: Expanding PossibilitiesRami AssafNessuna valutazione finora
- lAB 8.3.7 AND 8.5.1Documento14 paginelAB 8.3.7 AND 8.5.1Ammar Al Fukaihah0% (1)
- Lab Assignment 2018-2019Documento15 pagineLab Assignment 2018-2019tuyambaze jean claudeNessuna valutazione finora
- Ccnasv1.1 Chp10 Lab D Asa Isr s2s VPN StudentDocumento36 pagineCcnasv1.1 Chp10 Lab D Asa Isr s2s VPN Studentmuscle260% (1)
- D3 SBA StudentDocumento14 pagineD3 SBA Studentaliyilmaz100Nessuna valutazione finora
- Powerha Systemmirror For Aix V7.1 Two-Node Quick Configuration GuideDocumento34 paginePowerha Systemmirror For Aix V7.1 Two-Node Quick Configuration Guideassane baNessuna valutazione finora
- PT 8.2.5.4 Stadium Redundancy Test Plan StudentDocumento14 paginePT 8.2.5.4 Stadium Redundancy Test Plan Studentonlycisco.tkNessuna valutazione finora
- C1Lab08 PacketTracerConfigDocumento6 pagineC1Lab08 PacketTracerConfigMeo MapNessuna valutazione finora
- Cisco Spiad - LabDocumento48 pagineCisco Spiad - LabVicJ1992Nessuna valutazione finora
- ACN FileDocumento19 pagineACN FileSalil BansalNessuna valutazione finora
- Cisco CCNA Command Guide: An Introductory Guide for CCNA & Computer Networking Beginners: Computer Networking, #3Da EverandCisco CCNA Command Guide: An Introductory Guide for CCNA & Computer Networking Beginners: Computer Networking, #3Nessuna valutazione finora
- The Compete Ccna 200-301 Study Guide: Network Engineering EditionDa EverandThe Compete Ccna 200-301 Study Guide: Network Engineering EditionValutazione: 5 su 5 stelle5/5 (4)
- WAN TECHNOLOGY FRAME-RELAY: An Expert's Handbook of Navigating Frame Relay NetworksDa EverandWAN TECHNOLOGY FRAME-RELAY: An Expert's Handbook of Navigating Frame Relay NetworksNessuna valutazione finora
- CCNA Interview Questions You'll Most Likely Be AskedDa EverandCCNA Interview Questions You'll Most Likely Be AskedNessuna valutazione finora
- IPv4 Subnetting for Beginners: Your Complete Guide to Master IP Subnetting in 4 Simple Steps: Computer Networking, #1Da EverandIPv4 Subnetting for Beginners: Your Complete Guide to Master IP Subnetting in 4 Simple Steps: Computer Networking, #1Valutazione: 5 su 5 stelle5/5 (3)
- Dialogic Media Gateway Installation and Configuration Integration NoteDocumento31 pagineDialogic Media Gateway Installation and Configuration Integration NoteRiadh MadhourNessuna valutazione finora
- Application Notes For Polycom® Soundstation® Ip 7000 and Avaya Ip Office 500 V2 - Issue 1.1Documento16 pagineApplication Notes For Polycom® Soundstation® Ip 7000 and Avaya Ip Office 500 V2 - Issue 1.1Riadh MadhourNessuna valutazione finora
- Valcom SPKR IPODocumento17 pagineValcom SPKR IPORiadh MadhourNessuna valutazione finora
- Remote Dictionary Tscrack Nov - 6 - 2005Documento2 pagineRemote Dictionary Tscrack Nov - 6 - 2005Riadh MadhourNessuna valutazione finora
- Using Standard Analog Telephones With Fortivoice: VoicemailDocumento2 pagineUsing Standard Analog Telephones With Fortivoice: VoicemailRiadh MadhourNessuna valutazione finora
- FortiVoice VM Install PDFDocumento13 pagineFortiVoice VM Install PDFRiadh MadhourNessuna valutazione finora
- FortiVoice User Guide 7.31 Rev2Documento222 pagineFortiVoice User Guide 7.31 Rev2Riadh MadhourNessuna valutazione finora
- Installation Manual: BL1600A/800A Trixbox-2.8.0.3Documento14 pagineInstallation Manual: BL1600A/800A Trixbox-2.8.0.3Riadh MadhourNessuna valutazione finora
- LPI Selftesttraining 303-200 v2019-01-27 by Benjamin 36qDocumento18 pagineLPI Selftesttraining 303-200 v2019-01-27 by Benjamin 36qstephen sowahNessuna valutazione finora
- BIG-IP CGNAT ImplementationsDocumento116 pagineBIG-IP CGNAT ImplementationsAntonio Aguirre DorantesNessuna valutazione finora
- AWS CSAA Hands-On Labs SlidesDocumento142 pagineAWS CSAA Hands-On Labs Slidesnahid01Nessuna valutazione finora
- Troubleshooting MTU Size On PPOE - Router-MtuDocumento3 pagineTroubleshooting MTU Size On PPOE - Router-MtucarlosNessuna valutazione finora
- Sangfor IAM V11.9 Associate 07 FirewallDocumento19 pagineSangfor IAM V11.9 Associate 07 FirewallRandi AdipratamaNessuna valutazione finora
- Cblmcss Module 2Documento113 pagineCblmcss Module 2Rusty Ugay LumbresNessuna valutazione finora
- Working With IptablesDocumento10 pagineWorking With IptablesMordor ChaliceNessuna valutazione finora
- Firewall System OverviewDocumento61 pagineFirewall System OverviewAbdelilah CharboubNessuna valutazione finora
- SCSP Installation GuideDocumento109 pagineSCSP Installation Guidepsrikanth1176435Nessuna valutazione finora
- Ipsec VPN Troubleshooting Lab v11190816-1Documento28 pagineIpsec VPN Troubleshooting Lab v11190816-1garytj21Nessuna valutazione finora
- Pfsense Case Studies & AdvantagesDocumento4 paginePfsense Case Studies & AdvantagesShasidhar AthmakuriNessuna valutazione finora
- Trouble Ticket LabsDocumento32 pagineTrouble Ticket Labsthobzero70% (10)
- Datasheet 1100 Acme Packet Oracle SBCDocumento5 pagineDatasheet 1100 Acme Packet Oracle SBCJose AndresNessuna valutazione finora
- Satellite Router: Evolution X1 OutdoorDocumento1 paginaSatellite Router: Evolution X1 OutdoorEngineerAnoj KumarNessuna valutazione finora
- Checkpoint VPN-1 FireWall-1 NG Management II Instructors SlidesDocumento357 pagineCheckpoint VPN-1 FireWall-1 NG Management II Instructors Slidescameo001Nessuna valutazione finora
- ASR901-10G Datasheet PDFDocumento14 pagineASR901-10G Datasheet PDFVasyaNessuna valutazione finora
- CCNA 3 Case Study Spring 2022Documento7 pagineCCNA 3 Case Study Spring 2022Mohammed El-SaadiNessuna valutazione finora
- Static Policy NAT Dynamic Policy NATDocumento1 paginaStatic Policy NAT Dynamic Policy NATHai Pham VanNessuna valutazione finora
- Elfiq Linkbalancer Administrator Guide v3 04 PDFDocumento160 pagineElfiq Linkbalancer Administrator Guide v3 04 PDFPatrique Dias100% (1)
- Unit 5Documento32 pagineUnit 5Shashank RaghunathanNessuna valutazione finora
- Telstra Ultimate Gateway 3G42WT IP WAN Enterprise Setup GuideDocumento18 pagineTelstra Ultimate Gateway 3G42WT IP WAN Enterprise Setup GuideRogueOne RKNessuna valutazione finora
- Enhanced Room Management Deployment Guide v1.0.bDocumento96 pagineEnhanced Room Management Deployment Guide v1.0.blybrakissNessuna valutazione finora
- Lab 7.4.2 PDFDocumento3 pagineLab 7.4.2 PDFBridge SantosNessuna valutazione finora
- Technicolor CGM4231 User GuideDocumento126 pagineTechnicolor CGM4231 User Guidealejandro boludNessuna valutazione finora
- HG8247H Datasheet 05 PDFDocumento2 pagineHG8247H Datasheet 05 PDFAlexander PischulinNessuna valutazione finora
- Teltonika LTE ModemDocumento2 pagineTeltonika LTE ModemRyan TayNessuna valutazione finora
- FortiOS-6 0 6-HandbookDocumento2.702 pagineFortiOS-6 0 6-HandbookHumail JamalNessuna valutazione finora
- CN CS203 Lab ManualDocumento36 pagineCN CS203 Lab ManualSarthak Singh ChandelNessuna valutazione finora
- XPDP56 Release NotesDocumento140 pagineXPDP56 Release Notesdiegomatta13Nessuna valutazione finora
- Tutorials - DD-WRT WikiDocumento3 pagineTutorials - DD-WRT WikiombidasarNessuna valutazione finora