Documenti di Didattica
Documenti di Professioni
Documenti di Cultura
Crypto Slides 05 BC Tutor.4x2
Caricato da
Faraz Best0 valutazioniIl 0% ha trovato utile questo documento (0 voti)
25 visualizzazioni2 pagineTitolo originale
Crypto Slides 05 Bc Tutor.4x2
Copyright
© Attribution Non-Commercial (BY-NC)
Formati disponibili
PDF, TXT o leggi online da Scribd
Condividi questo documento
Condividi o incorpora il documento
Hai trovato utile questo documento?
Questo contenuto è inappropriato?
Segnala questo documentoCopyright:
Attribution Non-Commercial (BY-NC)
Formati disponibili
Scarica in formato PDF, TXT o leggi online su Scribd
0 valutazioniIl 0% ha trovato utile questo documento (0 voti)
25 visualizzazioni2 pagineCrypto Slides 05 BC Tutor.4x2
Caricato da
Faraz BestCopyright:
Attribution Non-Commercial (BY-NC)
Formati disponibili
Scarica in formato PDF, TXT o leggi online su Scribd
Sei sulla pagina 1di 2
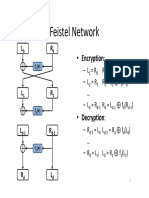
A Known Plaintext Attack on 1-Round DES
After removing the permutations IP and FP we get:
32 L 32 R 48 32 K=?
Block Ciphers Tutorial
L 32
R 32
c Eli Biham - May 3, 2005
146
Block Ciphers Tutorial (5)
c Eli Biham - May 3, 2005
147
Block Ciphers Tutorial (5)
A Known Plaintext Attack on 1-Round DES (cont.)
We are given a pair (M, C ) where M = (L, R) and C = (L , R) and we want to nd the 48-bit key K . We know that: F (R, K ) = L L
A Known Plaintext Attack on 2-Round DES
32 L 32 R 48 32 K1
1. Why is the output of all S -boxes known? 2. Given the 4 bits output of S1 how many 6-bit combinations are possible as input to S1? 3. How many 6-bit combinations are possible as the 6 bit key which takes part in the creation of the input to S1? 4. How many 48-bit combinations are possible for K ?
L 32 R 32 48 32 K2
c Eli Biham - May 3, 2005
148
Block Ciphers Tutorial (5)
c Eli Biham - May 3, 2005
149
Block Ciphers Tutorial (5)
A Known Plaintext Attack on 2-Round DES (cont.)
Thus, we have: F (R, K1) = L R F (R , K2) = L R As in the attack on one round, the rst expression reduces the number of possibilities for the 48 bits of K1 to 48 = 216 (as only a fraction of 232 of the keys pass the test). The second expression reduces the number of possibilities for the 48 bits of K2 to 48 = 216 as well. The set of possibilities for K1 and K2 intersects on 40 bits, as there are 40 key bits which are common to both round keys K1, K2. Thus, thus we get that the average number of possible 56-bit keys is slightly above 1.
A Known Plaintext Attack on 4-Round DES
After 4 rounds there are still bits which are unaected by some key bits. For example: Original key bit 46 is not used in round 1. It is used in round 2 (in K2) for the creation of the input to S5, thus it aects the 4 bits at the output of S5. These 4 bits become bits 8, 14, 25 and 3 after the permutation P. Key bit 46 is not used in round 3. Bits 8, 14, 25, 3 aect the output of S1, S2, S3, S4, S6, S7 in round 3, thus leaving the output bits of S5 and S8 unaected by key bit 46. There are 8 bits in the left 32-bit output of round 3 unaected from key bit 46. There are 8 bits in the right 32-bit output of round 4. unaected from key bit 46 (but they are aected by the other key bits and by the plaintext).
c Eli Biham - May 3, 2005
150
Block Ciphers Tutorial (5)
c Eli Biham - May 3, 2005
151
Block Ciphers Tutorial (5)
A Known Plaintext Attack on 4-Round DES (cont.)
This property can be used for a known plaintext attack: 1. Fix key bit 46 to be zero. 2. For every key K 1 with the key bit 46 set to zero (there are 255 such keys): (a) Encrypt the plaintext: C = EK 1 (P ). (b) Compare the 8 bits which are unaected by key bit 46 in C to the same 8 bits in the given ciphertext C . (c) If those bits are the same: Denote K 1 with the 46th bit set to one by K 2. If EK 1 (P ) = C then K 1 is probably the key. If EK 2 (P ) = C then K 2 is probably the key. If neither, continue to next key.
A Known Plaintext Attack on 4-Round DES (cont.)
Analysis: We encrypt the plaintext with all 255 possibilities for the key K 1. 247 keys on average agree with the ciphertext on the 8 bits. Therefore, we encrypt 247 possible K 2 values in order to nd the original key. The resulting time complexity is 255 + 247 encryptions instead of 256. Remark: When using the complementation property with this attack we get 254 + 246 encryptions in the worst case, and 253 + 245 encryptions in the average case.
c Eli Biham - May 3, 2005
152
Block Ciphers Tutorial (5)
c Eli Biham - May 3, 2005
153
Block Ciphers Tutorial (5)
A Known Plaintext Attack On 5-Round DES
Key bit 52 can be also used for an attack on 4 rounds: Original key bit 52 is not used in round 1. It is used in round 2 (in K2) for the creation of the input to S1, thus it aects the 4 bits at the output of S1. These 4 bits become bits 9, 17, 23 and 31 after the permutation P. Key bit 52 is not used in round 3. Bits 9, 17, 23, 31 aect the output of S2, S3, S4, S5, S6, S8 in round 3, thus leaving the output bits of S1 and S7 unaected by key bit 52. There are 8 bits in the left 32 bit output of round 3 unaected from key bit 52. There are 8 bits in the right 32 bit output of round 4 unaected from key bit 52.
c Eli Biham - May 3, 2005 154 Block Ciphers Tutorial (5)
A Known Plaintext Attack On 5-Round DES (cont.)
Key bit 52 has another property it is not used in the 5th round.
c Eli Biham - May 3, 2005
155
Block Ciphers Tutorial (5)
A Known Plaintext Attack On 5-Round DES (cont.)
Thus, we can use it for the following known plaintext attack: 1. Fix key bit 52 to be zero. 2. For every key K 1 with the key bit 52 set to zero (there are 255 such keys):
4 (a) Encrypt the plaintext up to round 4: EK 1 (P ). 1 (b) Decrypt the ciphertext one round: DK 1 (C ). 4 (c) Compare the 8 bits which are unaected by key bit 52 in EK 1 (P ) to 1 the same 8 bits in DK 1 (C ).
A Known Plaintext Attack On 5-Round DES (cont.)
Analysis: We encrypt the plaintext with all 255 possibilities for the key K 1 with key bit 52 set to zero. We are left with 247 keys on average. We also encrypt these 247 possible K 2 in order to nd the original key. Thus, we perform 255 +247 encryptions instead of 256. Remark: As in the attack on 4 rounds when using the complementation property we get 254 + 246 encryptions in the worst case, and 253 + 245 encryptions in the average case.
(d) If those bits are the same: Denote K 1 with the 52th bit set to one by K 2. If EK 1 (P ) = C then K 1 is probably the key. If EK 2 (P ) = C then K 2 is probably the key.
c Eli Biham - May 3, 2005
156
Block Ciphers Tutorial (5)
c Eli Biham - May 3, 2005
157
Block Ciphers Tutorial (5)
Potrebbero piacerti anche
- January 23, 2011: C 2011 Avinash Kak, Purdue UniversityDocumento32 pagineJanuary 23, 2011: C 2011 Avinash Kak, Purdue Universitymoon_manNessuna valutazione finora
- Ch3 Block Ciphers and DES - BlackboardDocumento37 pagineCh3 Block Ciphers and DES - BlackboardYazanAlomariNessuna valutazione finora
- DesDocumento58 pagineDesHarneet Singh ChuggaNessuna valutazione finora
- WINSEM2017-18 - CSE4003 - ETH - SJT505 - VL2017185003783 - Reference Material I - 005IDEADocumento3 pagineWINSEM2017-18 - CSE4003 - ETH - SJT505 - VL2017185003783 - Reference Material I - 005IDEAgovindNessuna valutazione finora
- Cryptography CS 555: Topic 10: Block Cipher Security & AESDocumento26 pagineCryptography CS 555: Topic 10: Block Cipher Security & AESAswini KnairNessuna valutazione finora
- Conventional Encryption AlgorithmsDocumento41 pagineConventional Encryption AlgorithmsSwapna DollyNessuna valutazione finora
- Symmetric Cryptography: Block Ciphers Lecture 4 (May 7, 2012)Documento58 pagineSymmetric Cryptography: Block Ciphers Lecture 4 (May 7, 2012)Agajan TorayevNessuna valutazione finora
- c03 Crypto DES AES UtcDocumento72 paginec03 Crypto DES AES UtcSunil SenNessuna valutazione finora
- Lecture 3: Block Ciphers and The Data Encryption Standard Lecture Notes On "Computer and Network Security"Documento51 pagineLecture 3: Block Ciphers and The Data Encryption Standard Lecture Notes On "Computer and Network Security"Majid BasharatNessuna valutazione finora
- Lecture 3Documento42 pagineLecture 3Ashwani JhaNessuna valutazione finora
- ICT 5301 Lecture3Documento36 pagineICT 5301 Lecture3voccubdNessuna valutazione finora
- Unit2: Data Encryption StandardDocumento78 pagineUnit2: Data Encryption StandardAbhishek RaoNessuna valutazione finora
- Lecture 3Documento38 pagineLecture 3Salman HabibNessuna valutazione finora
- Data Encryption StandardDocumento44 pagineData Encryption StandardAnkur AgrawalNessuna valutazione finora
- DES and AES AlgorithmDocumento51 pagineDES and AES Algorithmsolomon gosheNessuna valutazione finora
- Is DesDocumento53 pagineIs Desbcsm-s21-005Nessuna valutazione finora
- Network Security Lec 5Documento39 pagineNetwork Security Lec 5esha zahoorNessuna valutazione finora
- Modern Block Ciphers: CSE 651: Introduction To Network SecurityDocumento52 pagineModern Block Ciphers: CSE 651: Introduction To Network SecurityVinothsaravanan RamakrishnanNessuna valutazione finora
- Data Encryption Standard (DES)Documento53 pagineData Encryption Standard (DES)resky_12Nessuna valutazione finora
- Designing Block Ciphers - DES: Dhiren PatelDocumento37 pagineDesigning Block Ciphers - DES: Dhiren PatelSudha PatelNessuna valutazione finora
- Data Encryption Standard (DES)Documento6 pagineData Encryption Standard (DES)Faraz BestNessuna valutazione finora
- C3-Cryptography Block Cipher and Modes of OperationsDocumento29 pagineC3-Cryptography Block Cipher and Modes of OperationsTrần HiếuNessuna valutazione finora
- TE Mini-Project PPT Template 2019-20Documento16 pagineTE Mini-Project PPT Template 2019-20asmita dagadeNessuna valutazione finora
- Lecture 3: Block Ciphers and The Data Encryption Standard Lecture Notes On "Computer and Network Security"Documento51 pagineLecture 3: Block Ciphers and The Data Encryption Standard Lecture Notes On "Computer and Network Security"Shovit SharmaNessuna valutazione finora
- Loki 97Documento22 pagineLoki 97Diego Durán100% (1)
- The Application Layer: Algorithms)Documento19 pagineThe Application Layer: Algorithms)VinayKumarSinghNessuna valutazione finora
- Data Encryption Standard (Des)Documento28 pagineData Encryption Standard (Des)SoohailShaikhNessuna valutazione finora
- Introduction To Cryptography: Matt Mahoney Florida TechDocumento66 pagineIntroduction To Cryptography: Matt Mahoney Florida TechJboy EspinolaNessuna valutazione finora
- Ch3.Block CiphersDocumento19 pagineCh3.Block CiphersHemant MahajanNessuna valutazione finora
- Feistel AlgorithmDocumento38 pagineFeistel AlgorithmpkvlaserNessuna valutazione finora
- International Data Encryption AlgorithmDocumento8 pagineInternational Data Encryption AlgorithmAdithya VardhanNessuna valutazione finora
- Differential Cryptanalysis: C Etin Kaya Ko CDocumento48 pagineDifferential Cryptanalysis: C Etin Kaya Ko CToanNessuna valutazione finora
- Digital Encryption StandardDocumento30 pagineDigital Encryption StandardManoj SunchauriNessuna valutazione finora
- Ata Ncryption Tandard: D E S DESDocumento39 pagineAta Ncryption Tandard: D E S DESritesh sinhaNessuna valutazione finora
- Data Encryption Standard (DES)Documento52 pagineData Encryption Standard (DES)asmita dagadeNessuna valutazione finora
- S0,0 S1,0 S2,0 S3,0: S Oth Position, Oth WordDocumento3 pagineS0,0 S1,0 S2,0 S3,0: S Oth Position, Oth Wordharibabu madaNessuna valutazione finora
- 8 Des 18 01 2024Documento22 pagine8 Des 18 01 2024sankarperuriNessuna valutazione finora
- Student Solution Chap 08Documento6 pagineStudent Solution Chap 08Arshad AliNessuna valutazione finora
- Secret Key CryptographyDocumento32 pagineSecret Key Cryptographyvidhya_bineeshNessuna valutazione finora
- UNIT-2 Stream Ciphers and Block Ciphers: Cryptography and Network Security (3161606)Documento32 pagineUNIT-2 Stream Ciphers and Block Ciphers: Cryptography and Network Security (3161606)Ganesh GhutiyaNessuna valutazione finora
- Data Encryption Standard (DES)Documento19 pagineData Encryption Standard (DES)Christopher HerringNessuna valutazione finora
- Ropa EdsDocumento44 pagineRopa EdsConanNessuna valutazione finora
- Modern Block Cipher Standards (DES) : Debdeep MukhopadhyayDocumento16 pagineModern Block Cipher Standards (DES) : Debdeep Mukhopadhyayakyadav123Nessuna valutazione finora
- DBS Lecture3Documento11 pagineDBS Lecture3Trần QiNessuna valutazione finora
- Unit IiDocumento60 pagineUnit Iitalatamhari2002Nessuna valutazione finora
- Cacd 10,11Documento71 pagineCacd 10,11Ajay KumarNessuna valutazione finora
- NTC Project ReportDocumento7 pagineNTC Project ReportDhivya KarthikeyanNessuna valutazione finora
- Number Theory & CryptographyDocumento18 pagineNumber Theory & CryptographyPrateek ParashariNessuna valutazione finora
- Chapter ThreeDocumento30 pagineChapter ThreeMstafa MhamadNessuna valutazione finora
- Unit Ii: Block Ciphers & Public Key CryptographyDocumento109 pagineUnit Ii: Block Ciphers & Public Key CryptographyDhivyabharathi ANessuna valutazione finora
- Data Encryption Standard (DES)Documento15 pagineData Encryption Standard (DES)rama3191Nessuna valutazione finora
- Cys535 Lecture03Documento70 pagineCys535 Lecture03Waseem LaghariNessuna valutazione finora
- BlowfishDocumento62 pagineBlowfishDhaval DoshiNessuna valutazione finora
- CSB451 Ca4Documento8 pagineCSB451 Ca4s AgrawalNessuna valutazione finora
- DES - Secret Key Encryption: IBM/NSA 1977 - 64 Bit Blocks, 56 Bit Key, 8 Bits Parity 64 Bit Input BlockDocumento14 pagineDES - Secret Key Encryption: IBM/NSA 1977 - 64 Bit Blocks, 56 Bit Key, 8 Bits Parity 64 Bit Input BlockRock GamerNessuna valutazione finora
- MOOCs - README - MD at Master Z-A-F - MOOCs GitHub - 2 PDFDocumento7 pagineMOOCs - README - MD at Master Z-A-F - MOOCs GitHub - 2 PDFludipovaNessuna valutazione finora
- Sheet 2 DESDocumento2 pagineSheet 2 DESghaithzaza36Nessuna valutazione finora
- Unit 2Documento92 pagineUnit 2teja mNessuna valutazione finora
- Chapter 8 v8.1Documento113 pagineChapter 8 v8.1ANTONYNessuna valutazione finora
- Cns Manual No Source CodeDocumento55 pagineCns Manual No Source CodeKumar JiNessuna valutazione finora
- ProjectDocumento43 pagineProjectshraddha gholapNessuna valutazione finora
- Cryptography - New Encryption Technologies For Communications DesignersDocumento941 pagineCryptography - New Encryption Technologies For Communications Designersswim3051989Nessuna valutazione finora
- A Software For S-Box Performance Analysis and TestDocumento4 pagineA Software For S-Box Performance Analysis and TestAgustin Aboytes100% (1)
- Crypto FileDocumento27 pagineCrypto FileMunish WadhwaNessuna valutazione finora
- VPN ConceptDocumento12 pagineVPN ConceptSrijan TiwariNessuna valutazione finora
- Cryptography in Computing: Ian Perry Terence O'BrienDocumento10 pagineCryptography in Computing: Ian Perry Terence O'Brienthanhmaikmt123456Nessuna valutazione finora
- HSM Programmers Manual - 1270A514-3.DesbloqueadoDocumento289 pagineHSM Programmers Manual - 1270A514-3.DesbloqueadoBetzy Boo Vit100% (1)
- Knowledge Institute of Technology SALEM - 637504: Laboratory Manual FOR It8761 - Security LaboratoryDocumento49 pagineKnowledge Institute of Technology SALEM - 637504: Laboratory Manual FOR It8761 - Security LaboratoryCHANDRU MNessuna valutazione finora
- HSM I&O Manual 1270A513-3 PDFDocumento202 pagineHSM I&O Manual 1270A513-3 PDFrzaidi921Nessuna valutazione finora
- Data Encryption Standard (DES)Documento57 pagineData Encryption Standard (DES)Abrar Ahamad RvffptlSdjNessuna valutazione finora
- The DES Algorithm Illustrated: by J. Orlin GrabbeDocumento14 pagineThe DES Algorithm Illustrated: by J. Orlin GrabbeHaris ClovesNessuna valutazione finora
- A Comprehensive Evaluation of Cryptographic Algorithms Des 3des Aes Rsa and Blowfish PDFDocumento8 pagineA Comprehensive Evaluation of Cryptographic Algorithms Des 3des Aes Rsa and Blowfish PDFHenry Fu KeatNessuna valutazione finora
- Rsa ThesisDocumento86 pagineRsa ThesisViney BansalNessuna valutazione finora
- Computer SecurityDocumento40 pagineComputer SecuritytartarNessuna valutazione finora
- The DES Algorithm IllustratedDocumento10 pagineThe DES Algorithm IllustratedMoosa Khalid0% (1)
- " Image Encryption Using AES ": End Semester Project Report OnDocumento18 pagine" Image Encryption Using AES ": End Semester Project Report OnShivam KumarNessuna valutazione finora
- Tutorial 5-7Documento19 pagineTutorial 5-7lucyNessuna valutazione finora
- 02 - Chapter 2 - Conventional Encryption and Message ConfidentialityDocumento16 pagine02 - Chapter 2 - Conventional Encryption and Message ConfidentialityShreesha N RodriguesNessuna valutazione finora
- 6 Block Cipher CryptosystemsDocumento53 pagine6 Block Cipher CryptosystemsHasan BadirNessuna valutazione finora
- Modern Block Cipher Standards (DES) : Debdeep MukhopadhyayDocumento16 pagineModern Block Cipher Standards (DES) : Debdeep Mukhopadhyayakyadav123Nessuna valutazione finora
- IDEA and Blowfish NotesDocumento10 pagineIDEA and Blowfish NotesMukesh100% (2)
- JustificationDocumento8 pagineJustificationBiniyamNessuna valutazione finora
- Designing of AES Algorithm Using VerilogDocumento5 pagineDesigning of AES Algorithm Using VerilogAMIT VERMANessuna valutazione finora
- STM32 F-4 Series Marketing Presentation Customer PresentationDocumento97 pagineSTM32 F-4 Series Marketing Presentation Customer Presentationtrlp1712Nessuna valutazione finora
- Network SecurityDocumento52 pagineNetwork Securityswordmy2523Nessuna valutazione finora
- Scribleindia IT2352 Cryptography and Network Security Question BankDocumento7 pagineScribleindia IT2352 Cryptography and Network Security Question BankKavitha ManoharanNessuna valutazione finora
- COMP3334 Mid-Term 2223 Sample SolutionsDocumento8 pagineCOMP3334 Mid-Term 2223 Sample SolutionsFouillandNessuna valutazione finora
- Cryptography MCQDocumento4 pagineCryptography MCQShesh Narayan MishraNessuna valutazione finora