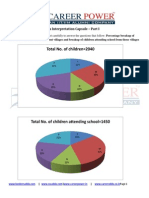
Documenti di Didattica
Documenti di Professioni
Documenti di Cultura
Active Passive
Caricato da
Tushar SaxenaCopyright
Formati disponibili
Condividi questo documento
Condividi o incorpora il documento
Hai trovato utile questo documento?
Questo contenuto è inappropriato?
Segnala questo documentoCopyright:
Formati disponibili
Active Passive
Caricato da
Tushar SaxenaCopyright:
Formati disponibili
International Journal of Computer Science and Management Research
Vol 1 Issue 2 September 2012 ISSN 2278-733X
A Survey of Cooperative Black and Gray hole Attack in MANET
B.Revathi* D.Geetha**
*Research scholar in Computer Science, Sree Saraswathi Thyagaraja College of Arts and Science Pollachi-642 107, Tamil Nadu, India **Assistant Professor in Computer Science, Sree Saraswathi Thyagaraja College of Arts and Science Pollachi-642 107, Tamil Nadu, India
Abstract Mobile ad hoc networks (MANETs) are a set of mobile nodes which are self-configuring and connected by wireless links automatically as per the defined routing protocol. Security is an essential requirement in mobile ad hoc network (MANETs). Compared to wired networks, MANETs are more vulnerable to security attacks due to the lack of a trusted centralized authority and limited resources. Attacks on ad-hoc networks can be classified as passive and active attacks, depending on whether the normal operation of the network is disrupted or not. These mobile nodes communicate with each other without any infrastructure, furthermore, all of the transmission links are established through wireless medium. In this paper we address the problem of packet forwarding misbehavior and propose a mechanism to detect and remove the black and gray hole attacks. Keywords black hole, gray hole, MANET, active attack, passive attack.
I. INTRODUCTION This Mobile Ad-hoc Networks (MANETs) differ from existing networks by the fact that they depend on no fixed infrastructure. Nodes forming the network perform all functionality of the network with each node performs the functionality of both host and router.
MANETs are vulnerable to attacks by selfish or malicious nodes, such as packet dropping (black-hole) attacks and selective forwarding (gray-hole) attacks. Another characteristic of a MANET is, limited bandwidth, limited battery power. This characteristic makes routing in a MANET an even more difficult task. Currently, several efficient routing protocols have been proposed. These protocols can be classified into two categories: reactive routing protocols and proactive routing protocols. In reactive routing protocols, such as the Ad hoc On Demand Distance Vector (AODV) protocol [1], nodes find routes only when required. In proactive routing protocols, such as the Optimized Link State Routing (OLSR) protocol [2], nodes obtain routes by periodic exchange of topology information. Gray hole attack [3] may occur due to a malicious node which is deliberately mischievous, as well as a damaged node interface we simulated the Gray hole attack node which is intentionally misbehaving, as well as a damaged node interface we simulated the Gray hole attack. We made our simulations using Network Simulator version 2 (NS-2) [4] simulation programs that consists of the collection of all network protocols to simulate many of the accessible network topologies. II. PROTOCOLS COMMONLY USED FOR MANETS There are many number of routing protocols that are proposed in MANET. The most commonly used protocols are: A. AODV (Ad Hoc On-Demand Distance Vector Routing) Ad hoc On-Demand Distance Vector (AODV) Routing is a routing protocol for MANETs and other wireless ad-hoc networks. It is a reactive routing protocol, meaning that is to establish a route to a destination only on demand. AODV is capable of both unicast and multicast routing. Route Requests (RREQs), Route Replies (RREPs), and Route Errors (RERRs) are the message types distinct by AODV. These message types are received through UDP, and normal IP header processing applies. B. DSR (Dynamic Source Routing) The Dynamic Source Routing (DSR) [5] protocol is an on demand routing protocol that is based on the concept of source routing. The DSR is a simple and efficient routing protocol
Fig.1.1 A typical MANET
A MANET is referred to as an infrastructure less network because the mobile nodes in the network dynamically set up paths among themselves to send out packets temporarily. Due to multi-hop routing and open working environment,
B.Revathi et.al.
205
www.ijcsmr.org
International Journal of Computer Science and Management Research
designed specially for use in multi-hop wireless ad hoc networks of mobile nodes. DSR allows the network to be entirely self-organizing and self-configuring, without the need for any existing network infrastructure or administration. Dynamic source routing protocol (DSR) is an on-demand protocol designed to confine the bandwidth consumed by control packets in ad hoc wireless networks by eliminating the periodic table-update messages. C.
Vol 1 Issue 2 September 2012 ISSN 2278-733X
DYMO (Dynamic On-Demand MANET Routing Protocol)
.Fig. 3.1 External and Internal Attacks in MANETs
The Dynamic MANET On-demand (DYMO) routing protocol enables reactive, multihop, unicast routing between participating DYMO routers. The basic operations of the DYMO protocol are route discovery and route maintenance. III. CLASSIFICATION OF ATTACKS The attacks can be categorized on the basis of the source of the attacks i.e. Internal or External, and on the behaviour of the attack i.e. Passive or Active attack. This classification is important because the attacker can develop the network either as internal, external or/ as well as active or passive attack against the network. A. External and Internal Attack External attacks, in which the attacker aims to cause congestion, spread false routing information or disturb nodes from providing services.External attacks are attacks launched by challengers who are not initially official to participate in the network operations. These attacks usually aim to cause network congestion, deny access to specific network function or to interrupt the whole network operations. External attackers are mainly outside the networks who want to get access to the network, once they get access to the network they start sending fake packets, denial of service in order to interrupt the performance of the whole network. This attack is same, like the attacks that are made against wired network. These attacks can be barred by implementing security measures such as firewall, where the access of unauthorized person to the network can be mitigated. In internal attack the attacker wants to have usual access to the network as well as contribute in the normal activities of the network. Internal attack is more strict attacks then external attacks. Internal attacks, in which the challenger wants to gain the normal access to the network and contribute the network activities, either by some malicious impersonation to get the access to the network as a new node, or by directly compromising a existing node and using it as a basis to conduct its malicious behaviors.Internal nodes might misbehave to save their limited resources, such as the battery powers, the processing capabilities, and the communication bandwidth. Attacks that are caused by the misbehaving internal nodes are hard to detect because to distinguish between normal network failures and misbehaviour activities in the ad hoc networks is not an easy task.
B. Active and Passive Attack In active attack the attacker disrupt the performance of the network, steal important information and try to destroy the data during the exchange in the network. Active attacks can be an internal or an external attack. The active attacks are meant to destroy the performance of the network in such case the active attack act as an internal node in the network. Being an active part of the network it is easy for the node to make use of and takeover any internal node to use it to introduce false packets injection or denial of service. This attack brings the 18 attacker in strong position where attacker can modify, make and replays the massages. Attackers in passive attacks do not interrupt the normal operations of the network. In Passive attack, it listens to the network in order to know and understand how they are located in the network, how the nodes are communicating with each other. Before the attacker start an attack against the network, the attacker has enough information about the network that it can easily capture and introduce attack in the network.
Fig. 3.2 Active and Passive Attack in MANETs
IV. NETWORK LAYER THREATS A. Black hole Attack MANETs face various securities threats i.e. attack that are passed out against them to interrupt the normal performance of the networks. Black hole attack is one of the security threat in which the traffic is redirect to such a node that actually does not exist in the network. In these attacks, black hole attack is that kind of attack which occurs in Mobile Ad-Hoc networks (MANET). In black hole attack, a malicious node uses its
B.Revathi et.al.
206
www.ijcsmr.org
International Journal of Computer Science and Management Research
routing protocol in order to endorse itself for having the shortest path to the destination node or to the packet it wants to interrupt. This destructive node advertises its availability of new routes irrespective of checking its routing table. In this way attacker node will always have the availability in replying to the route request and thus intercept the data packet and retain it [6]. In protocol based on flooding, the malicious node reply will be received by the requesting node before the response of reply from actual node; hence a malicious and forged route is created. When this route is establish, now it is up to the node whether to drop all the packets or promote it to the unknown address [7]. The black hole attack has two properties. First, the node exploits the mobile ad-hoc routing protocol, such as AODV, to promote itself as having a valid route to a target node, even though the route is false, with the aim of intercepting packets. Second, the attacker consumes the intercepted packets without any forwarding. However, the attacker runs the risk that neighbouring nodes will check and represent the ongoing attacks. There is a more delicate form of these attacks when an attacker selectively forward packets. An attacker suppress or modifies packets originating from some nodes, while leaving the data from the other nodes unchanged, which limits the suspicion of its wrongdoing.
Vol 1 Issue 2 September 2012 ISSN 2278-733X
involves the cooperation between two attacking nodes [14]. One attacker captures routing traffic at one point of the network and turns it to another point in the network that shares a private high speed communication link between the attackers, and then selectively injects tunnel traffic back into the network. The two colluding attacker can potentially deform the topology and establish routes under the control over the wormhole link.
1 2 3 A
Fig.4.2 Warm Hole Attack
D. Location Disclosure Attack: In this attack, the privacy necessities of an ad hoc network are compromised. Through the use of traffic analysis techniques or with simpler probing and monitoring approaches an attacker is able to discover the place of a node, and the configuration of the network. E. Gray hole Attack In this kind of attack the attacker misleads the network by approving to forward the packets in the network. As soon as it receive the packets from the neighbouring node, the attacker falls the packets. This is a type of active attack. In the beginning the attacker nodes behaves usually and reply true RREP messages to the nodes that started RREQ messages. When it receives the packets it starts falling the packets and launch Denial of Service (DoS) attack. The malicious activities of gray hole attack is different in different ways. It drops packets while forwarding them in the network. In some other gray hole attacks the attacker node behaves maliciously for the time until the packets are dropped and then switch to their normal behavior [8]. Due this behavior its very tricky for the network to figure out such kind of attack. Gray hole attack is also termed as node misbehaving attack [9]. V. PROPERTIES OF BLACKHOLE, GREYHOLE AND WORMHOLE ATTACKS First, the Black hole node exploits the ad hoc routing protocol, such as AODV, to promote itself as having a valid route to a destination node, even though the route is fake, with the intention of intercepting packets. Second, the packets are consumed by the Black hole node. Third, the Black hole nodes can conduct synchronized attacks. Grey hole is a node that can switch from behaving acceptably to behaving like a black hole. Wormhole attacks depend on a node misrepresenting its
Fig.4.1Black hole Attack
B. Impersonation Attack: The attacker nodes impersonates a right node and joins the network untraceable, sends false routing information, masked as some other trusted node. C. Wormhole Attack: In the wormhole attacks, a compromised node in the ad hoc networks colludes with external attacker to create a shortcut in the network. By creating this shortcut, they could trap the source node to win in the route discovery process and later starts the interception attacks. Packets from these two colluding attackers are usually transmitted using wired connection to create the best route from source to the destination node. In addition, if the wormhole nodes constantly maintain the false routes, they could permanently reject other routes from being established. As a result, the intermediate nodes reside along that denied routes are unable to contribute in the network operations. The wormhole attack
B.Revathi et.al.
207
www.ijcsmr.org
International Journal of Computer Science and Management Research
location. Hence, location based routing protocols have the potential to prevent wormhole attacks. VI. COUNTERMEASURES A. Wormhole Attack Countermeasure Wormhole attacks depend on a node misrepresenting its position. Hence, location based routing protocols have the ability to prevent wormhole attacks. Localization may be done using globally easy to get to beacons that broadcast known locations [10]. A solution to wormhole attacks was planned in which all nodes are equipped with directional antennas. Nodes use specific sectors of their antennas to communicate with each other. Each couple of nodes examine the track of received signals from its neighbour. If the directions of both pairs match the neighbour relation is set [10]. This method may only be used in networks using Directional antennas [11].Another solution was proposed in which nodes estimate the expanse of its neighbours using the Received Signal Strength. The value is sent to a central controller which calculates the physical topology based on individual sensor distance measurement. Wormhole can be trapped as without wormhole attack the topology is usually flat [12] [11]. B. Black hole and Grey hole Attack Countermeasure To detect black and gray hole nodes, one proposal is having the sender occasionally check through all available routes to establish if the destination received all of its messages intact. This must be done after some data has been sent. In order to avoid any black hole nodes that might interfere with message traffic, the sender broadcasts a "check" request message (Fig. 3), and the destination's response would follow the same route as the request (Fig. 4). To pact with the possibility of a node altering or faking the clients response, the sender compares each response with the data that it sent to the destination. If the responses differ from what the sender sent, it may indicate a bad link or a malicious node. If any two client responses vary, that is almost a sure sign of a malicious node [13].
Vol 1 Issue 2 September 2012 ISSN 2278-733X
CONCLUSION In this paper, a study on the work that attempt to detect black or gray hole or cooperative black and gray hole attack has been done. Each node can locally maintain its own table of black listed nodes whenever it tries to send data to any destination node and it can also aware the network about the black listed nodes which are of great importance in networking. The survey revised about various type of protocols commonly used for MANETs.(eg. AODV, DSR, DYMO) and briefly summarized about the classification of attacks, Network layer threats and its properties of black hole, gray hole attack, worm hole attacks. Finally the paper explained the countermeasures of Warm hole attacks, gray hole attack and black hole attack.
REFERENCES
[1] [1] C. Perkins, E. Belding-Royer, and S. Das, Ad Hoc Ondemand Distance Vector (AODV) Routing, IETF RFC 3561, July 2003. Th. Clausen et al., Optimized Link State Routing Protocol, IETF Internet P. Misra,. Routing Protocols for Ad Hoc Mobile Wireless Networks,http://www.cse.wustl.edu/~jain/cis78899/adhoc_ro uting/index.html, 14 May 2006. H. Goto, Y. Hasegawa, and M . Tanaka, Efficient Schedu lin g Focusing on the Duality of MPL Representatives, Proc. IEEE Symp. Computational Intelligence in Scheduling (SCIS 07), IEEE Press, Dec. 2007, pp. 57-64, doi:10.1109/SCIS.2007.357670. J.Yoon, M. Liu, B.Noble Random Waypoint Considered Harmful IEEE INFOCOM, 2003. [6] K. Biswas and Md. Liaqat Ali, Security threats in Mobile AdHoc Network, Master Thesis, Blekinge Institute of Technology Sweden, 22nd March 2007 G. A. Pegueno and J. R. Rivera, Extension to MAC 802.11 for performance Improvement in MANET, Karlstads University, Sweden, December 2006 S.Marti, T.J.Giuli, K.Lai, M.Baker, Mitigating Routing Misbehavior in Mobile Ad-Hoc Networks. Zhu, C. Lee, M.J.Saadawi, T., RTT-Based Optimal Waiting time for Best Route Selection in Ad-Hoc Routing Protocols, IEEE Military Communications Conference, Vol. 2, pp. 1054-1059, Oct, 2003. L. Hu and D. Evans, Department of Computer Science , University of Virginia Charlottesville, Using Directional Antennas to Prevent Wormhole Attacks, VA IJCSNS International Journal of Computer Science and Network Security, VOL.8 No.7, July 2008. K. Win, Department of Engineering Physics, Mandalay Technological University, Pathein Gyi, Mandalay, Analysis of Detecting Wormhole Attack in Wireless Networks, World Academy of Science, Engineering and Technology 48 2008 W. Wang and B. Bhargava., Visualization of wormholes in sensor networks, Proceedings of the 2004 ACM workshop on Wireless Security, pp. 51-60, 2004. E. Mohammed and L. Dargin,Oakland University School of Computer Science and Engineering CSE 681 Information Security, Routing Protocols Security in Ad Hoc Networks. Y.C.Hu, A.Perrig, and D.B.Johnson, Packet Leashes: A Defense Against Wormhole Attacks in Wireless Ad hoc Networks, Proceedings of 22nd Annual Joint Conf. IEEE Computer and Communications Societies (Infocom03), San Francisco, CA, vol.3, pp.1976-1986, April 2003.
[2] [3]
[4]
[5]
[7]
[8] [9]
N1 S BH N2 D
[10]
[11]
Fig.6.1 black hole interference in sender broadcast [12]
N1 S BH
Fig.6.2 Destination Response
D N2
[13]
[14]
B.Revathi et.al.
208
www.ijcsmr.org
Potrebbero piacerti anche
- Signals and CommunicationDocumento3 pagineSignals and CommunicationTushar SaxenaNessuna valutazione finora
- Andhra Bank - Recruitment of Probationary Officers (PGDBF 2016 - 17)Documento1 paginaAndhra Bank - Recruitment of Probationary Officers (PGDBF 2016 - 17)Tushar SaxenaNessuna valutazione finora
- ClassifiationDocumento26 pagineClassifiationTushar SaxenaNessuna valutazione finora
- Signal Processing:: ACF PDF CDF Communication:: Block Diagram Analog and Digital Modulation Schemes NoiseDocumento1 paginaSignal Processing:: ACF PDF CDF Communication:: Block Diagram Analog and Digital Modulation Schemes NoiseTushar SaxenaNessuna valutazione finora
- Basic Electrical NotesDocumento58 pagineBasic Electrical NotesKamal Joshi100% (2)
- Di Capsule BA Part 1Documento5 pagineDi Capsule BA Part 1Tushar SaxenaNessuna valutazione finora
- L-26 (TB) Three Phase TransformerDocumento16 pagineL-26 (TB) Three Phase Transformervelisbar100% (1)
- 8085 Microprocessor Lab ManualDocumento43 pagine8085 Microprocessor Lab ManualMukulSinghNessuna valutazione finora
- BCADocumento23 pagineBCATushar SaxenaNessuna valutazione finora
- Syll ELitmusDocumento2 pagineSyll ELitmusTushar SaxenaNessuna valutazione finora
- CWE-SPL-IV-Recruitment of Specialist Officers PDFDocumento2 pagineCWE-SPL-IV-Recruitment of Specialist Officers PDFTushar SaxenaNessuna valutazione finora
- Elitmus Probability Questions For Elitmus - Elitmus Questions For PH Test Page 1 PDFDocumento3 pagineElitmus Probability Questions For Elitmus - Elitmus Questions For PH Test Page 1 PDFTushar Saxena0% (1)
- Uptu B.tech 2nd Year SyllabusDocumento16 pagineUptu B.tech 2nd Year SyllabusPrakash KumarNessuna valutazione finora
- BtechDocumento27 pagineBtechakash nairNessuna valutazione finora
- Cse 2ndyear SyllabusDocumento11 pagineCse 2ndyear Syllabusashish jainNessuna valutazione finora
- Syll ELitmusDocumento2 pagineSyll ELitmusTushar SaxenaNessuna valutazione finora
- Some Basic ConceptsDocumento10 pagineSome Basic ConceptsTushar SaxenaNessuna valutazione finora
- Features of IndiaDocumento2 pagineFeatures of IndiaTushar SaxenaNessuna valutazione finora
- CL 11Documento8 pagineCL 11Tushar SaxenaNessuna valutazione finora
- Chemistry Class 11 Syllabus - 2015-2016 CBSEsyllabusDocumento4 pagineChemistry Class 11 Syllabus - 2015-2016 CBSEsyllabusTushar SaxenaNessuna valutazione finora
- Days of National and International Importance JanurayDocumento7 pagineDays of National and International Importance JanurayTushar SaxenaNessuna valutazione finora
- Banking Pathway 2015: English (Mix Quiz) : Bankers Adda Old Logo SeminarDocumento7 pagineBanking Pathway 2015: English (Mix Quiz) : Bankers Adda Old Logo SeminarTushar SaxenaNessuna valutazione finora
- AdvertisementDocumento2 pagineAdvertisementTushar SaxenaNessuna valutazione finora
- Verification Value Rupee Savings Bank Account Modi: Crucible Theatre (UK)Documento7 pagineVerification Value Rupee Savings Bank Account Modi: Crucible Theatre (UK)Tushar SaxenaNessuna valutazione finora
- InjusticeDocumento1 paginaInjusticeTushar SaxenaNessuna valutazione finora
- P-N Junction DiodeDocumento7 pagineP-N Junction DiodeTushar SaxenaNessuna valutazione finora
- EMI BasicsDocumento11 pagineEMI BasicsTushar SaxenaNessuna valutazione finora
- BJTDocumento14 pagineBJTTushar SaxenaNessuna valutazione finora
- Progrmming LanguageDocumento2 pagineProgrmming LanguageTushar SaxenaNessuna valutazione finora
- Why BPSKDocumento1 paginaWhy BPSKTushar SaxenaNessuna valutazione finora
- The Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeDa EverandThe Subtle Art of Not Giving a F*ck: A Counterintuitive Approach to Living a Good LifeValutazione: 4 su 5 stelle4/5 (5794)
- The Yellow House: A Memoir (2019 National Book Award Winner)Da EverandThe Yellow House: A Memoir (2019 National Book Award Winner)Valutazione: 4 su 5 stelle4/5 (98)
- A Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryDa EverandA Heartbreaking Work Of Staggering Genius: A Memoir Based on a True StoryValutazione: 3.5 su 5 stelle3.5/5 (231)
- Hidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceDa EverandHidden Figures: The American Dream and the Untold Story of the Black Women Mathematicians Who Helped Win the Space RaceValutazione: 4 su 5 stelle4/5 (895)
- The Little Book of Hygge: Danish Secrets to Happy LivingDa EverandThe Little Book of Hygge: Danish Secrets to Happy LivingValutazione: 3.5 su 5 stelle3.5/5 (400)
- Shoe Dog: A Memoir by the Creator of NikeDa EverandShoe Dog: A Memoir by the Creator of NikeValutazione: 4.5 su 5 stelle4.5/5 (537)
- Never Split the Difference: Negotiating As If Your Life Depended On ItDa EverandNever Split the Difference: Negotiating As If Your Life Depended On ItValutazione: 4.5 su 5 stelle4.5/5 (838)
- Elon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureDa EverandElon Musk: Tesla, SpaceX, and the Quest for a Fantastic FutureValutazione: 4.5 su 5 stelle4.5/5 (474)
- Grit: The Power of Passion and PerseveranceDa EverandGrit: The Power of Passion and PerseveranceValutazione: 4 su 5 stelle4/5 (588)
- The Emperor of All Maladies: A Biography of CancerDa EverandThe Emperor of All Maladies: A Biography of CancerValutazione: 4.5 su 5 stelle4.5/5 (271)
- On Fire: The (Burning) Case for a Green New DealDa EverandOn Fire: The (Burning) Case for a Green New DealValutazione: 4 su 5 stelle4/5 (74)
- Team of Rivals: The Political Genius of Abraham LincolnDa EverandTeam of Rivals: The Political Genius of Abraham LincolnValutazione: 4.5 su 5 stelle4.5/5 (234)
- Devil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaDa EverandDevil in the Grove: Thurgood Marshall, the Groveland Boys, and the Dawn of a New AmericaValutazione: 4.5 su 5 stelle4.5/5 (266)
- The Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersDa EverandThe Hard Thing About Hard Things: Building a Business When There Are No Easy AnswersValutazione: 4.5 su 5 stelle4.5/5 (344)
- The World Is Flat 3.0: A Brief History of the Twenty-first CenturyDa EverandThe World Is Flat 3.0: A Brief History of the Twenty-first CenturyValutazione: 3.5 su 5 stelle3.5/5 (2259)
- The Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreDa EverandThe Gifts of Imperfection: Let Go of Who You Think You're Supposed to Be and Embrace Who You AreValutazione: 4 su 5 stelle4/5 (1090)
- The Unwinding: An Inner History of the New AmericaDa EverandThe Unwinding: An Inner History of the New AmericaValutazione: 4 su 5 stelle4/5 (45)
- The Sympathizer: A Novel (Pulitzer Prize for Fiction)Da EverandThe Sympathizer: A Novel (Pulitzer Prize for Fiction)Valutazione: 4.5 su 5 stelle4.5/5 (121)
- Her Body and Other Parties: StoriesDa EverandHer Body and Other Parties: StoriesValutazione: 4 su 5 stelle4/5 (821)
- USA v. William Gazafi Plea Letter To Judge TitusDocumento13 pagineUSA v. William Gazafi Plea Letter To Judge TitusSouthern Maryland OnlineNessuna valutazione finora
- Omer Farooq ResumeDocumento3 pagineOmer Farooq ResumemykdesignerNessuna valutazione finora
- Zambian Open University: School of Social Science and HumanitiesDocumento9 pagineZambian Open University: School of Social Science and HumanitiesEvangelist Kabaso SydneyNessuna valutazione finora
- Self Incompatibility: Dr. L.K.GangwarDocumento38 pagineSelf Incompatibility: Dr. L.K.GangwarSiddhant Singh100% (1)
- Hernia Examination OSCE Guide PDFDocumento8 pagineHernia Examination OSCE Guide PDFParsaant SinghNessuna valutazione finora
- National Social Protection Strategy GhanaDocumento95 pagineNational Social Protection Strategy GhanaSisiraPinnawalaNessuna valutazione finora
- Web Applications Desktop IntegratorDocumento5 pagineWeb Applications Desktop IntegratorSatendra BhatiNessuna valutazione finora
- PHD 2020 21 List of Shortlisted Candidates For InterviewDocumento6 paginePHD 2020 21 List of Shortlisted Candidates For InterviewAnkesh Kumar SrivastavaNessuna valutazione finora
- Rfid: Threats, Failures, and FixesDocumento43 pagineRfid: Threats, Failures, and FixesChromatonNessuna valutazione finora
- President Uhuru Kenyatta's Speech During The Kenya@50 Celebrations at Uhuru Gardens, Nairobi On The Mid-Night of 12th December, 2013Documento3 paginePresident Uhuru Kenyatta's Speech During The Kenya@50 Celebrations at Uhuru Gardens, Nairobi On The Mid-Night of 12th December, 2013State House KenyaNessuna valutazione finora
- What Is Black Box Testing?: Black Box Testing Is Done Without The Knowledge of The Internals of The System Under TestDocumento127 pagineWhat Is Black Box Testing?: Black Box Testing Is Done Without The Knowledge of The Internals of The System Under TestusitggsipuNessuna valutazione finora
- Gelernter, David Hillel - The Tides of Mind - Uncovering The Spectrum of Consciousness-Liveright Publishing Corporation (2016)Documento263 pagineGelernter, David Hillel - The Tides of Mind - Uncovering The Spectrum of Consciousness-Liveright Publishing Corporation (2016)রশুদ্দি হাওলাদার100% (2)
- Take Home Assignment 2Documento2 pagineTake Home Assignment 2Kriti DaftariNessuna valutazione finora
- Match Headings Questions 1-5Documento2 pagineMatch Headings Questions 1-5Aparichit GumnaamNessuna valutazione finora
- GRADE 8 3rd Quarter ReviewerDocumento9 pagineGRADE 8 3rd Quarter ReviewerGracella BurladoNessuna valutazione finora
- Kenoyer, Jonathan M. & Heather ML Miller, Metal technologies of the Indus valley tradition in Pakistan and Western India, in: The Archaeometallurgy of the Asian Old World, 1999, ed. by VC Piggott, Philadelphia, Univ. of Pennsylvania Museum, pp.107-151Documento46 pagineKenoyer, Jonathan M. & Heather ML Miller, Metal technologies of the Indus valley tradition in Pakistan and Western India, in: The Archaeometallurgy of the Asian Old World, 1999, ed. by VC Piggott, Philadelphia, Univ. of Pennsylvania Museum, pp.107-151Srini KalyanaramanNessuna valutazione finora
- Agriculture SustanableDocumento13 pagineAgriculture SustanableCoco FloraNessuna valutazione finora
- Detailed Lesson Plan in English I. ObjectivesDocumento3 pagineDetailed Lesson Plan in English I. ObjectivesJenefer Tunares100% (1)
- CBR Bahasa Inggris Fisika Kelompok 1Documento9 pagineCBR Bahasa Inggris Fisika Kelompok 1Ryan SianiparNessuna valutazione finora
- I Semester Financial Accounting - Bpz1A: Theory 15 Problems 60Documento28 pagineI Semester Financial Accounting - Bpz1A: Theory 15 Problems 60Blaze MysticNessuna valutazione finora
- Azeem English Magazine Vol. 22 Issue 01Documento68 pagineAzeem English Magazine Vol. 22 Issue 01Raheel Asghar100% (1)
- Mosaic TRD4 Tests EOY 1Documento4 pagineMosaic TRD4 Tests EOY 1MarcoCesNessuna valutazione finora
- Introductory Econometrics A Modern Approach Solutions Manual PDFDocumento9 pagineIntroductory Econometrics A Modern Approach Solutions Manual PDFAnonymous bzcYj42Ain0% (2)
- EndomytosisDocumento8 pagineEndomytosisBlackbeetleNessuna valutazione finora
- How Order Management Help E-Commerce Increase Performance During The Pandemic PeriodDocumento4 pagineHow Order Management Help E-Commerce Increase Performance During The Pandemic PeriodInternational Journal of Innovative Science and Research TechnologyNessuna valutazione finora
- Edward Taylor S PoemsDocumento6 pagineEdward Taylor S PoemsGodofwarNessuna valutazione finora
- Alphabet Series Tricks - PDF: Down During Your ExamDocumento8 pagineAlphabet Series Tricks - PDF: Down During Your ExamJoshNessuna valutazione finora
- OODBSDocumento29 pagineOODBSMinh Tu TranNessuna valutazione finora
- Catalog Encoder MILEDocumento1 paginaCatalog Encoder MILELucas SuplinoNessuna valutazione finora
- Social Defence Vision 2020: Dr. Hira Singh Former Director National Institute of Social DefenceDocumento19 pagineSocial Defence Vision 2020: Dr. Hira Singh Former Director National Institute of Social DefencePASION Jovelyn M.Nessuna valutazione finora