Documenti di Didattica
Documenti di Professioni
Documenti di Cultura
Setting Up 802.1x Authentiaction
Caricato da
ruletriplexCopyright
Formati disponibili
Condividi questo documento
Condividi o incorpora il documento
Hai trovato utile questo documento?
Questo contenuto è inappropriato?
Segnala questo documentoCopyright:
Formati disponibili
Setting Up 802.1x Authentiaction
Caricato da
ruletriplexCopyright:
Formati disponibili
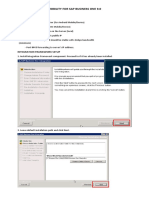
Setting up 802.1x Authentication using PEAP on Windows Server 2008: 1. Install an Enterprise CA and perform the following: a.
Create a copy of the Computer certificate template called 802.1x in the Certificate Templates MMC snap-in that: i. Gives everyone Read and Enroll permission on the Security tab ii. Uses the Fully Distinguished Name in the Subject Name Format section on the Subject Name tab. b. Import the template into the Certificate Templates folder within the Certification Authority MMC snap-in. c. Enroll for an 802.1x certificate using the Certificates (Local Computer) MMC snap-in (right click Personal Certificates). 2. Install the Network Policy Server (NPS) role in Server Manager. 3. In the NPS console, ensure that: a. A RADIUS Client has been created for the WAP using the WAPs IP Address, RADIUS Standard protocol and the Message Authenticator Attribute. You must supply a password (i.e. Secret555). b. A Network Policy has been created (called 802.1x Policy for example) that uses PEAP. You must manually add the PEAP protocol and Edit its configuration to ensure that you have an adequate PEAP certificate from Step 1. c. (Optional) In the Network Policy you created in the previous step, ensure that the Session-Timeout is set to 5 minutes. This will force the RADIUS server to regenerate the symmetric keys used by WEP/WPA every 5 minutes (good security). 4. Configure the WAP (using the web interface) to use WEP/WPA and RADIUS. Ensure that you enter the IP address of your RADIUS server (the IAS server) as well as the same password from Step 3a (i.e. Secret555). 5. Ensure that the Trusted Root certificate for your CA has been installed on the client computer. You can do this by: a. Importing the Trusted Root certificate (from the root of C:\ on your CA) into the Trusted Root Certification Authorities folder within the Certificates (Local Computer) MMC snap-in or b. Importing the Trusted Root certificate into a GPO (Computer Configuration Windows Settings Security Settings Public Key Policies Trusted Root Certification Authorities).
6. Configure the properties of your wireless NIC (Wireless Networks tab) to use PEAP authentication. In the PEAP properties, you can configure your system to use the Trusted Root of the CA to validate the server certificate as well as ensure that MSCHAPv2 is used to protect the username/password that is automatically passed to the RADIUS server. All of this configuration may also be done with a GPO (Computer Configuration Windows Settings Security Settings Wireless Network (IEEE 802.11) Policies) 7. Connect to the SSID of the WAP by browsing for available networks (Right-click your wireless NIC). Once you are connected, you can run the getmac command on the command line to verify that you were authenticated by RADIUS.
Setting up 802.1x Authentication using PEAP on Windows Server 2003: 1. Install an Enterprise CA and perform the following: a. Create a copy of the Computer certificate template called 802.1x in the Certificate Templates MMC snap-in that: i. Gives everyone Read and Enroll permission on the Security tab ii. Uses the Fully Distinguished Name in the Subject Name Format section on the Subject Name tab. b. Import the template into the Certificate Templates folder within the Certification Authority MMC snap-in. c. Enroll for an 802.1x certificate using the Certificates (Local Computer) MMC snap-in (right click Personal Certificates). 2. Install the Internet Authentication Service (IAS) from Add/Remove Programs in Control Panel. 3. In the IAS console, ensure that: a. The IAS Server is registered in AD b. A RADIUS Client has been created for the WAP using the WAPs IP Address, RADIUS Standard protocol and the Message Authenticator Attribute. You must supply a password (i.e. Secret555). c. A Remote Access Policy has been created (called 802.1x Policy for example) that uses PEAP. Ensure that you press the Configure button beside PEAP to ensure that you have an adequate PEAP certificate from Step 1. d. (Optional) In the Profile section of the Remote Access Policy you created in the previous step, ensure that the Session-Timeout is set to 5 minutes. This will force the RADIUS server to regenerate the symmetric keys used by WEP/WPA every 5 minutes (good security). 4. Configure the WAP (using the web interface) to use WEP/WPA and RADIUS. Ensure that you enter the IP address of your RADIUS server (the IAS server) as well as the same password from Step 3b (i.e. Secret555). 5. Ensure that the Trusted Root certificate for your CA has been installed on the client computer. You can do this by: a. Importing the Trusted Root certificate (from the root of C:\ on your CA) into the Trusted Root Certification Authorities folder within the Certificates (Local Computer) MMC snap-in or b. Importing the Trusted Root certificate into a GPO (Computer Configuration Windows Settings Security Settings Public Key Policies Trusted Root Certification Authorities).
6. Configure the properties of your wireless NIC (Wireless Networks tab) to use PEAP authentication. In the PEAP properties, you can configure your system to use the Trusted Root of the CA to validate the server certificate as well as ensure that MSCHAPv2 is used to protect the username/password that is automatically passed to the RADIUS server. All of this configuration may also be done with a GPO (Computer Configuration Windows Settings Security Settings Wireless Network (IEEE 802.11) Policies) 7. Connect to the SSID of the WAP by browsing for available networks (Right-click your wireless NIC). Once you are connected, you can run the getmac command on the command line to verify that you were authenticated by RADIUS.
Potrebbero piacerti anche
- How To Configure GlobalProtect SSODocumento9 pagineHow To Configure GlobalProtect SSOkano_85Nessuna valutazione finora
- 这篇文档是我当时部署 CHEVRON 中国区 802.1X 的设计实施文档, 由本人领导项目, 带领团 队执行, 事后书写成文. 每个企业环境不尽相同, 大家可供参考!Documento41 pagine这篇文档是我当时部署 CHEVRON 中国区 802.1X 的设计实施文档, 由本人领导项目, 带领团 队执行, 事后书写成文. 每个企业环境不尽相同, 大家可供参考!wanglinNessuna valutazione finora
- SSL Certificate Download ProcessDocumento2 pagineSSL Certificate Download Processkrishna mNessuna valutazione finora
- Configuring CISCO ACS Server As Radius For Intel AMT 802.1x Clients With Windows DB Rev 3Documento30 pagineConfiguring CISCO ACS Server As Radius For Intel AMT 802.1x Clients With Windows DB Rev 3Angel AlarasNessuna valutazione finora
- How To Configure Odyssey Client For Secure EAP-PEAP AuthenticationDocumento2 pagineHow To Configure Odyssey Client For Secure EAP-PEAP AuthenticationvivekNessuna valutazione finora
- HMC DesktopDocumento22 pagineHMC DesktopgmawoyoNessuna valutazione finora
- How To Setup and Configure Commerce Data Exchange Real-Time ServiceDocumento12 pagineHow To Setup and Configure Commerce Data Exchange Real-Time ServiceIslam SultanNessuna valutazione finora
- VM Quick ReferenceDocumento4 pagineVM Quick Referencenebojsa_n_nikolicNessuna valutazione finora
- Peap Configuration Guide v1.20: Self-Signing Certificates SectionDocumento15 paginePeap Configuration Guide v1.20: Self-Signing Certificates SectionvladusgeniusNessuna valutazione finora
- IM-A9 Integration StepsDocumento2 pagineIM-A9 Integration StepsBikesh PandeyNessuna valutazione finora
- How-To Configure Azure AD and Office 365 Mailbox Settings For ESADocumento18 pagineHow-To Configure Azure AD and Office 365 Mailbox Settings For ESAmhakeem.elsaeedNessuna valutazione finora
- Avaya Knowledge - AES - How To Create A Certificate Authority CA From SMGR For AES and Test With TSAPI and DMCC SDKs PDFDocumento15 pagineAvaya Knowledge - AES - How To Create A Certificate Authority CA From SMGR For AES and Test With TSAPI and DMCC SDKs PDFAshishNessuna valutazione finora
- Windows CFG Gen User GuideDocumento5 pagineWindows CFG Gen User GuideOrlando Villabona BolañosNessuna valutazione finora
- SCCM Home LabDocumento11 pagineSCCM Home Labpeddareddy100% (2)
- How To Setup Wireless Network SecurityDocumento28 pagineHow To Setup Wireless Network SecurityCollins OnwocheiNessuna valutazione finora
- Client To Box Certificate Auth VPNDocumento9 pagineClient To Box Certificate Auth VPNMihai MihutzNessuna valutazione finora
- Generating and Installing Domain Controller CertificateDocumento2 pagineGenerating and Installing Domain Controller CertificateGabriel Morales AngaritaNessuna valutazione finora
- Install SSL in AwareIM/TomcatDocumento3 pagineInstall SSL in AwareIM/TomcatcishpixNessuna valutazione finora
- 213922-Configure-Mac-Authentication-Ssid-On-Cis C9800Documento15 pagine213922-Configure-Mac-Authentication-Ssid-On-Cis C9800JavierNessuna valutazione finora
- Configure EAP-TLS Authentication With ISE - CiscoDocumento17 pagineConfigure EAP-TLS Authentication With ISE - CiscoOussama HlaliNessuna valutazione finora
- Client Authentication Using Digital Certificates in Websphere Application Server Community EditionDocumento19 pagineClient Authentication Using Digital Certificates in Websphere Application Server Community EditionstevicNessuna valutazione finora
- Mobility For Sap Business One 9.0: Integration Framework SetupDocumento13 pagineMobility For Sap Business One 9.0: Integration Framework SetupRobeth John BacalanNessuna valutazione finora
- SiC Worksheet - Practical 2 AAADocumento15 pagineSiC Worksheet - Practical 2 AAAHasan ShaikhNessuna valutazione finora
- CscappaDocumento18 pagineCscappanethakzNessuna valutazione finora
- BIOS and Integrated Management Controller SetupDocumento17 pagineBIOS and Integrated Management Controller SetupPetre RaduNessuna valutazione finora
- AAA Authentication LabDocumento4 pagineAAA Authentication LabGregoryNessuna valutazione finora
- Practice Test: Microsoft 70-648Documento53 paginePractice Test: Microsoft 70-648TestNessuna valutazione finora
- SSL Configuration Over WebSphereDocumento9 pagineSSL Configuration Over WebSphereKusum PoddarNessuna valutazione finora
- Configurating SAML AuthenticationDocumento6 pagineConfigurating SAML AuthenticationkrishnamurthyyadavNessuna valutazione finora
- Bench 7Documento34 pagineBench 7maham sabir100% (1)
- Cisco Packet Tracer Wireless LabDocumento3 pagineCisco Packet Tracer Wireless LabOmoyemi OniNessuna valutazione finora
- User-ID LabDocumento23 pagineUser-ID LabHenryNessuna valutazione finora
- Configure Eap Tls Flow With IseDocumento24 pagineConfigure Eap Tls Flow With IseKash BarlasNessuna valutazione finora
- Cyberoam SSL VPN Quick Start Guide For ApplianceDocumento14 pagineCyberoam SSL VPN Quick Start Guide For AppliancedanashriNessuna valutazione finora
- Preface: Howto Set Up Certificate Based Vpns With Check Point Appliances - R80.X EditionDocumento35 paginePreface: Howto Set Up Certificate Based Vpns With Check Point Appliances - R80.X Edition000-924680Nessuna valutazione finora
- Windows Openssl Ca Toolkit: Installation and ConfigurationDocumento8 pagineWindows Openssl Ca Toolkit: Installation and Configurationsantoshg83Nessuna valutazione finora
- Exam 70-744: IT Certification Guaranteed, The Easy Way!Documento188 pagineExam 70-744: IT Certification Guaranteed, The Easy Way!DanielNessuna valutazione finora
- Configuration Tool User Guide Windows Version 1.6.3.3: 1. InstallationDocumento5 pagineConfiguration Tool User Guide Windows Version 1.6.3.3: 1. InstallationBain WaveNessuna valutazione finora
- CA Server Using Certificates and SSL in Windows: Student Name: Aishpreet Sran UID:18BCS2835 Section/Group: CSE-17/BDocumento6 pagineCA Server Using Certificates and SSL in Windows: Student Name: Aishpreet Sran UID:18BCS2835 Section/Group: CSE-17/BAFAQ CUNessuna valutazione finora
- File-569764169-569764169 AssignmentAttachment E2BD9992 2638694495122549Documento7 pagineFile-569764169-569764169 AssignmentAttachment E2BD9992 2638694495122549magmuthmwangiNessuna valutazione finora
- Installation of Cisco Secure Acs Remote Agent For WindowsDocumento16 pagineInstallation of Cisco Secure Acs Remote Agent For Windowsregis_paduaNessuna valutazione finora
- Client VPN OS Configuration - Cisco MerakiDocumento48 pagineClient VPN OS Configuration - Cisco Merakikatherine painiiNessuna valutazione finora
- Pki OpensslDocumento11 paginePki OpensslgdeepthiNessuna valutazione finora
- Configure EAP-TLS Authentication With ISE PDFDocumento18 pagineConfigure EAP-TLS Authentication With ISE PDFkongarajaykumarNessuna valutazione finora
- 300 715 V8.02 PDFDocumento21 pagine300 715 V8.02 PDFInnovior IT TechNessuna valutazione finora
- SATItem ViewDocumento15 pagineSATItem ViewLuiz Carlos RochaNessuna valutazione finora
- Lab 2.5.2 Install Aironet Client Utility (ACU) : ObjectiveDocumento13 pagineLab 2.5.2 Install Aironet Client Utility (ACU) : ObjectiveMohammed SajidNessuna valutazione finora
- Integration of BW in SAP EPDocumento20 pagineIntegration of BW in SAP EPJuan Carlos FloresNessuna valutazione finora
- Common Errors in BW Related To SSLDocumento24 pagineCommon Errors in BW Related To SSLKrishna Chaitanya SunkavalliNessuna valutazione finora
- Anyconnect VPN Phone With Certificate Authentication On An Asa Configuration ExampleDocumento14 pagineAnyconnect VPN Phone With Certificate Authentication On An Asa Configuration Examplejorigoni2013Nessuna valutazione finora
- ISA Server 2006 Lab Manual (Version 3.0f) - HOL392Documento26 pagineISA Server 2006 Lab Manual (Version 3.0f) - HOL392Ntawigaya Baraka NtawigayaNessuna valutazione finora
- SW 6 10 Creating and Installing SSL Certificates DV 1 0Documento11 pagineSW 6 10 Creating and Installing SSL Certificates DV 1 0Dzmitry KuzmiankouNessuna valutazione finora
- Create Windows CA Certificate Templates For CUCMDocumento32 pagineCreate Windows CA Certificate Templates For CUCMDavid Van HerckNessuna valutazione finora
- ESXi Setup in DMCDocumento7 pagineESXi Setup in DMColgalushNessuna valutazione finora
- SM9.30 TSO LWSSO Configuring Guide PDFDocumento14 pagineSM9.30 TSO LWSSO Configuring Guide PDFhanspaulNessuna valutazione finora
- Securing Application Deployment with Obfuscation and Code Signing: How to Create 3 Layers of Protection for .NET Release BuildDa EverandSecuring Application Deployment with Obfuscation and Code Signing: How to Create 3 Layers of Protection for .NET Release BuildNessuna valutazione finora
- Deploying Certificates Cisco Meeting Server: Design your certificates for CMS services and integrate with Cisco UCM Expressway and TMSDa EverandDeploying Certificates Cisco Meeting Server: Design your certificates for CMS services and integrate with Cisco UCM Expressway and TMSNessuna valutazione finora
- Pro ASP.NET Core Identity: Under the Hood with Authentication and Authorization in ASP.NET Core 5 and 6 ApplicationsDa EverandPro ASP.NET Core Identity: Under the Hood with Authentication and Authorization in ASP.NET Core 5 and 6 ApplicationsNessuna valutazione finora
- Configuration and Evaluation of Some Microsoft and Linux Proxy Servers, Security, Intrusion Detection, AntiVirus and AntiSpam ToolsDa EverandConfiguration and Evaluation of Some Microsoft and Linux Proxy Servers, Security, Intrusion Detection, AntiVirus and AntiSpam ToolsNessuna valutazione finora
- Knowledge Assessment Answers 8Documento4 pagineKnowledge Assessment Answers 8ruletriplexNessuna valutazione finora
- Knowledge Assessment Answers 6Documento4 pagineKnowledge Assessment Answers 6ruletriplexNessuna valutazione finora
- Knowledge Assessment Answers 7Documento4 pagineKnowledge Assessment Answers 7ruletriplex100% (1)
- Knowledge Assessment Answers 4Documento4 pagineKnowledge Assessment Answers 4ruletriplexNessuna valutazione finora
- Knowledge Assessment Answers 5Documento9 pagineKnowledge Assessment Answers 5ruletriplexNessuna valutazione finora
- Knowledge Assessment Answers 1Documento3 pagineKnowledge Assessment Answers 1ruletriplex100% (2)
- Knowledge Assessment Answers 3Documento5 pagineKnowledge Assessment Answers 3ruletriplexNessuna valutazione finora
- HW Solution Chap1-3Documento8 pagineHW Solution Chap1-3ruletriplexNessuna valutazione finora
- DHCP Step by Step GuideDocumento28 pagineDHCP Step by Step GuideruletriplexNessuna valutazione finora
- RRAS TutorialDocumento10 pagineRRAS TutorialruletriplexNessuna valutazione finora
- LightSwitch HTML Client TutorialDocumento39 pagineLightSwitch HTML Client TutorialruletriplexNessuna valutazione finora
- PowerShell TutorialDocumento17 paginePowerShell TutorialruletriplexNessuna valutazione finora
- Lab11 WorksheetDocumento5 pagineLab11 WorksheetruletriplexNessuna valutazione finora
- Lab13 WorksheetDocumento4 pagineLab13 WorksheetruletriplexNessuna valutazione finora
- Lab13 WorksheetDocumento4 pagineLab13 WorksheetruletriplexNessuna valutazione finora
- Suelos y Ganado 2350Documento10 pagineSuelos y Ganado 2350Juan David Herrera CastroNessuna valutazione finora
- UNIT 3 DCN Class LecturesDocumento101 pagineUNIT 3 DCN Class LecturesJyotiSharmaNessuna valutazione finora
- Domain Name SystemDocumento39 pagineDomain Name SystemRavi SrinivasNessuna valutazione finora
- Lab 2 Configuring Basic Routing and Switching PDFDocumento11 pagineLab 2 Configuring Basic Routing and Switching PDFDennis Masuku MacfeeNessuna valutazione finora
- Conmutación, Planificación y Gestión de Redes - IET9-1.1: Pregunta 1Documento9 pagineConmutación, Planificación y Gestión de Redes - IET9-1.1: Pregunta 1Derly Valdivia CapizoNessuna valutazione finora
- IP Routing Primer Plus TQW - DarksidergDocumento505 pagineIP Routing Primer Plus TQW - DarksidergpankajduklanNessuna valutazione finora
- COMPUTER NETWORKS Answers To Selected Exam QuestionsDocumento33 pagineCOMPUTER NETWORKS Answers To Selected Exam QuestionsVijay TrivediNessuna valutazione finora
- CCNA 200 125 171q by PenPineappleApplePen Protected 1 PDFDocumento66 pagineCCNA 200 125 171q by PenPineappleApplePen Protected 1 PDFmsansari1984Nessuna valutazione finora
- Python ScapyDocumento34 paginePython ScapyFurqan Ali KhanNessuna valutazione finora
- Network - Diagnostics - 2023 01 09.14 09 29Documento23 pagineNetwork - Diagnostics - 2023 01 09.14 09 29jaewm123Nessuna valutazione finora
- Cisco Wireless Lan Control PDFDocumento1.016 pagineCisco Wireless Lan Control PDFTrung MỗNessuna valutazione finora
- RPKI Technology Overview: Sandeep BhanooriDocumento23 pagineRPKI Technology Overview: Sandeep BhanooriSandeep KumarNessuna valutazione finora
- Delta Insightpower G3 Mini SNMP Card: User ManualDocumento64 pagineDelta Insightpower G3 Mini SNMP Card: User ManualBenNessuna valutazione finora
- Fortinet Testking NSE4 v2016-16-20 by Andy 167qDocumento79 pagineFortinet Testking NSE4 v2016-16-20 by Andy 167qAndrew WebbNessuna valutazione finora
- CCNA Project ReportDocumento140 pagineCCNA Project ReportavniNessuna valutazione finora
- Pan Os Administrator's Guide: AuthenticationDocumento24 paginePan Os Administrator's Guide: Authenticationivanrisa2525Nessuna valutazione finora
- PCAP Debug Logs-Rev DDocumento18 paginePCAP Debug Logs-Rev DrodrigowandersoNessuna valutazione finora
- Mikrotik Load Balancing 2 ISPDocumento5 pagineMikrotik Load Balancing 2 ISPFanny SispriadiNessuna valutazione finora
- Step by Step Guide For Windows Server 2003 Domain Controller and DNS Server Setup - Windows ReferenceDocumento31 pagineStep by Step Guide For Windows Server 2003 Domain Controller and DNS Server Setup - Windows ReferenceMiguel DiasNessuna valutazione finora
- Nmap Cheat SheetDocumento9 pagineNmap Cheat SheetDraKon GamingNessuna valutazione finora
- EPC Principle TestDocumento8 pagineEPC Principle Testlaralym2Nessuna valutazione finora
- IS 1172 1993 Code of Basic Requirements For Water Supply, Drainage and SanitationDocumento18 pagineIS 1172 1993 Code of Basic Requirements For Water Supply, Drainage and SanitationbbaplNessuna valutazione finora
- Nse4 Study Plan - Weekly: Fortigate Security 6.2 Self-PacedDocumento2 pagineNse4 Study Plan - Weekly: Fortigate Security 6.2 Self-PacedAchraf AIT HIJOUBNessuna valutazione finora
- WWW Calculator NetDocumento2 pagineWWW Calculator NetMarcos Jair Cuellar ArteagaNessuna valutazione finora
- Wireshark Lab: 802.11: Approach, 6 Ed., J.F. Kurose and K.W. RossDocumento5 pagineWireshark Lab: 802.11: Approach, 6 Ed., J.F. Kurose and K.W. RossN Azzati LabibahNessuna valutazione finora
- Ip AddressDocumento19 pagineIp AddressRodel SantosNessuna valutazione finora
- 11 Data Link LayerMultiple Access ControlDocumento42 pagine11 Data Link LayerMultiple Access Controlrafaqathussainc077Nessuna valutazione finora
- CN Unit 5Documento153 pagineCN Unit 5lard BaringNessuna valutazione finora
- Csen 503 Application Layer I: Amr El Mougy Rania Said Lamia AlbadrawyDocumento35 pagineCsen 503 Application Layer I: Amr El Mougy Rania Said Lamia Albadrawybb2323bNessuna valutazione finora
- CN Lab - Manual (2023-24) Odd SemDocumento58 pagineCN Lab - Manual (2023-24) Odd SemBv shankar RoyalNessuna valutazione finora