Documenti di Didattica
Documenti di Professioni
Documenti di Cultura
IT Security Strategy
Caricato da
Gaurav AgarwalCopyright
Formati disponibili
Condividi questo documento
Condividi o incorpora il documento
Hai trovato utile questo documento?
Questo contenuto è inappropriato?
Segnala questo documentoCopyright:
Formati disponibili
IT Security Strategy
Caricato da
Gaurav AgarwalCopyright:
Formati disponibili
Information Technology Security Strategy
I. Executive Summary
The University of Tennessee, a statewide system of higher education, has four campuses, three institutes, and a presence in each of Tennessee's ninety-five counties. This distributed presence creates additional requirements for the electronic exchange of information. The universitys mission is to provide education, research, and community service to business and industry, schools, governments, organizations, and citizens throughout the state. Providing a secure and robust information technology (IT) infrastructure that supports this mission is critical. Each campus and institute plays a unique role in the overall success of the university. The universitys governance model, characterized as distinct-but-linked, has led to a combination of centralized and distributed management and operation of its IT infrastructure. This distributed environment presents many unique security challenges, many of which can only be addressed through centralized coordination and the collaboration of a broad statewide constituency. The Information Security Office (ISO), under the direction of the Senior Vice President and Chief Financial Officer, has the authority and responsibility for the universitys IT security program, which includes: y y y y y y y y y y y The development of a sound IT security strategy The development of IT security policies and adoption of best practices Oversight and regulatory compliance across the entire university Vulnerability assessment and remediation Incident response Network and systems monitoring Forensic analysis IT security consulting Policy and best practice compliance Information systems awareness training Business continuity
II. Scope
An effective and efficient IT security program requires the cooperation and collaboration of the entire university-wide community; therefore, this IT security strategy applies to the entire university, including all campuses and institutes. The University of Tennessee bears the responsibility for taking steps to protect the confidentiality, integrity, and availability of information in its custody, whether in electronic or material form.
III. Foundational Principles
This strategy is guided by the foundational principles of confidentiality, integrity, and availability as it relates to information and IT resources.
08/07/07
Information Technology Security Strategy
Page 1 of 6
Confidentiality attempts to prevent the intentional or unintentional unauthorized disclosure of electronic information (i.e., has the information been released to the public without authorization?). Integrity attempts to prevent the intentional or unintentional unauthorized modification of electronic information (i.e., has the information been altered?). Availability attempts to insure the reliable and timely access to electronic information or computing resources (i.e., is access to the electronic information efficient and available to the person in need?). In order to maintain confidentiality, integrity, and availability, there are a set of programs that must be established. These include: 1. A program to develop policies and adopt best practices ensures that the university community has a standard methodology for IT security. Included in this program is a clear definition of the roles and responsibilities for all constituents. 2. A network and systems monitoring program ensures that the infrastructure is watched for attacks. 3. A sound risk analysis and management program including a vulnerability assessment process that represents specific areas of security focus ensures that risks and consequences are identified, evaluated, and analyzed to avoid unnecessary remediation and expenses. 4. A program to direct regulatory compliance with all federal and state laws, university policies, university best practices, and other industry regulations assist the university in maintaining a compliant reputation with the regulatory bodies. 5. A user awareness and education program Recognizes the importance of the human aspect of IT security. 6. A business continuity program ensures the availability of computing and other resources necessary to carry on the mission of the university in times of physical duress. 7. An incident response program that includes forensic analysis ensures that the proper methods for handling IT security incidents are followed and that evidence is preserved. 8. An IT security consulting program ensures that the university user community has access to the information it needs to establish a secure IT environment.
08/07/07
Information Technology Security Strategy
Page 2 of 6
IV. Functional Principles
In order to extend beyond the foundational principles and implement a sound IT security program there are a set of functional principles that must be applied to all IT configurations. The two principles include the following: 1. The principle of least privilege requires that a user on a computer system be given no more privilege than necessary to perform a specific function. Implementing least privilege requires identifying the minimum set of privileges required to perform that function, and restricting the user or computer system to those privileges and nothing more. 2. The principle of defense-in-depth requires using a layered approach to security such that single points of failure in protection are minimized. A defense in depth strategy combines people, administration, and technology to establish multiple layers of protection. a. The People Strategy is defined as user awareness, user training, and user accountability including training efforts for students, faculty, staff, and others including but not limited to, subcontractors, visitors, visiting scholars, potential students, research associates, grant and contract support personnel, media representatives, guest speakers, and non-university entities granted access. b. The Administration Strategy is defined as the policies and best practices that detail what to do and how to do it as well as the consequences of non-compliance. c. The Technology Strategy is defined as the tools and equipment that protect the IT infrastructure. The Foundational and Functional Principles defined in sections III and IV will be implemented using information and system classification criteria. These criteria define a framework for categorizing information according to the perceived risk to the university and assign the responsibility to the custodian to identify and designate the classification.
V. Roles and Responsibilities
All members of the university have a role in the development, implementation, and maintenance of the IT security program. For the program to be successful, it is important to establish the key roles for the personnel that will implement and maintain it. The definition of roles in the IT security program is based on industry standards as well as the model created by organizations that require the strongest IT security: the Department of Energy (DOE) and the Department of Defense (DOD). The DOE and DOD design establishes an autonomous security department that oversees all IT activities that relate to security and validates that the implementations by departments meet the IT security requirements. The
08/07/07
Information Technology Security Strategy
Page 3 of 6
matrix showing the breakdown of the responsibilities for IT security can be found at http://security.tennessee.edu/. Senior Vice President and Chief Financial Officer Responsible for providing system oversight of all IT resources. In concert with the Executive Vice President of the university, provides the final approval for all IT policies university-wide. Information Security Office Responsible for centralized coordination and oversight of the universitys IT security. The ISO will perform both proactive and reactive IT security activities. The proactive activities include, but are not limited to, best practices definition, departmental, system, and application vulnerability assessment, firewall design review, procurement review, systems and applications design review, and policy and best practices compliance validation. The reactive activities include, but are not limited to, network and systems anomaly monitoring, forensics, and incident response as it relates to issues with critical systems or confidential information. The ISO will provide oversight and develop policies and best practices, whereas, individual campus/institute leadership will be responsible for the actual implementation. Campus/Institute Leadership Responsible for the implementation and maintenance of the protective measures required for creating a secure IT environment at the campus/institute. The secure IT environment will be based on the IT security policies and best practices as defined by the ISO. Implementation will include both proactive and reactive IT security activities. Responsible for assigning the Position of Authority for Information Systems who is the person assigned the information systems authority for that respective location. Information/System Custodian An employee acting on the behalf of the university who bears responsibility for a particular set of the university's information or a specific university system that is under their control. Information/System Manager The person or persons who have been delegated by the information/system custodian with the responsibility for maintaining security controls. Users Responsible for the implementation and maintenance of protection measures for the systems they manage based on the IT security policies and best practices.
VI. Policies and Best Practices
All University of Tennessee IT policies must be followed and are located at http://www.tennessee.edu/policy/. The IT security policies are created by the ISO in coordination with the Information Technology Security Council (ITSC). The Information Security Officer (ISO) chairs the ITSC with membership from the Knoxville campus, the Chattanooga campus, the Martin campus, the Health 08/07/07 Information Technology Security Strategy Page 4 of 6
Sciences Center, the Space Institute, the Institute of Agriculture, and the Institute for Public Service. All policies are reviewed by the Policy Management Committee and presented to the Senior Vice President and Chief Financial Officer and Executive Vice President for joint approval. The ISO will also develop IT security best practices that provide specific guidance in protecting information and systems. The best practices are designed to establish the minimum protections necessary based on the classification of the system and the classification of the information contained on the system. These best practices must be followed unless an exception is documented and approved. Best practice documents are referenced from the Information Security Office home page at http://security.tennessee.edu/.
VII. Communications
Establishing and maintaining effective and efficient communications channels for IT security related activity is essential. To facilitate the necessary collaboration between the ISO and various system/campus/institute leaders, the ISO will establish and maintain the following IT security committees: 1. The Information Technology Security Council (ITSC) As defined above, will assist in the development of IT security policies. 2. IT Security Technical Review Committee Made up of representatives from the campus or institute IT technical community, this committee will assist in the implementation of best practices at the campus/institute level. 3. IT Security Business and Operations Review Committee Made up of representatives from the campus or institute business and operations community, this committee will examine and make recommendations concerning the protocols that relate to IT security issues at the campus/institute level. While this strategy seeks to provide clear lines of separation and segregation of duties in the assigned IT security responsibilities as defined in section V, areas of overlap will occasionally occur. In those cases, the ISO and the campuses/institutes must work together to ensure that proper security practices are implemented (e.g., incident response of critical systems or systems with confidential information, systems and applications design, and firewall design). In these areas of overlap, the ISO will fulfill its responsibility for IT security oversight. The ISO may also, at the direction of the Senior Vice President and Chief Financial Officer or at the request of campus/institute leadership, assume temporary responsibility for specific projects or security activities as necessary. From time to time, critical IT security issues require immediate decisions by the university leadership in order to minimize risk or impact. The ISO will establish a direct line of communication with the campus, institute, or system senior leadership in dealing with these issues. 08/07/07 Information Technology Security Strategy Page 5 of 6
VIII. University Provided Security Resources
The university supports the need for tools for implementing sound IT security practices at campuses and institutes and will fund the base cost of these tools. The campuses and institutes will be provided the opportunity to buy from a university contract based on a per-unit cost. Examples of such tools include, but are not limited to, a software firewall, an encryption tool for individual files, sanitization tools, a search tool for confidential footprints, and a server change monitoring tool.
IX. Compliance
Individual areas (e.g. campuses or institutes, departments, colleges and divisions) within the university may define specific IT security requirements, guidelines, and standards as long as the documents do not detract from the universitys Information Technology Security Strategy, policies, or best practices. The universitys Information Technology Security Strategy, policies, and best practices will supersede such documents where inconsistencies exist. Any non-compliance of the universitys Information Technology Security Strategy, policies, or best practices must be reported to the ISO. Non-compliance can result in immediate withdrawal or suspension of system and network privileges and/or disciplinary action. The ISO will work with University Human Resources and campus Student Judicial Affairs departments to develop and implement appropriate sanctions for non-compliance of the Universitys Information Technology Security Strategy, policies, or best practices. Noncompliance issues that cannot be resolved by the ISO will be directed to the Senior Vice President and Chief Financial Officer. Critical non-compliance issues will be directed to the Audit Committee of the Board of Trustees.
X.
Exceptions
Policies and best practices are management instructions indicating a course of action. Compliance with the universitys Information Technology Security Strategy, policies, and best practices are mandatory. In some instances, exceptions to policies and best practices must be made due to extenuating circumstances. Such exceptions must be documented and approved prior to implementation. To provide for a standard way of doing non-standard things, the university will implement a process for reviewing and approving/ disapproving requests for exceptions. This process shall be created and maintained by the ISO for the University of Tennessee. Instructions for requesting an exception can be found at http://security.tennessee.edu/.
08/07/07
Information Technology Security Strategy
Page 6 of 6
Potrebbero piacerti anche
- Information Security Incident ManagementDocumento8 pagineInformation Security Incident ManagementcaliagarNessuna valutazione finora
- Information Security PolicyDocumento19 pagineInformation Security PolicyVarun UpadhyayNessuna valutazione finora
- IT Risk Management Process A Complete Guide - 2020 EditionDa EverandIT Risk Management Process A Complete Guide - 2020 EditionNessuna valutazione finora
- Remote Access Policy Word TemplateDocumento2 pagineRemote Access Policy Word Templateapi-3736636100% (1)
- security controls A Complete Guide - 2019 EditionDa Everandsecurity controls A Complete Guide - 2019 EditionNessuna valutazione finora
- Iso/Iec: Group 3Documento37 pagineIso/Iec: Group 3Abdunnajar MahamudNessuna valutazione finora
- IT Security Incident ManagementDocumento3 pagineIT Security Incident ManagementBrianEarlNessuna valutazione finora
- Operations Security Policy Template v1.0Documento10 pagineOperations Security Policy Template v1.0rsgrthyjhNessuna valutazione finora
- Iso/Iec 27001 and Cobit 5 Information Security Management and Data Classification ProgramDocumento8 pagineIso/Iec 27001 and Cobit 5 Information Security Management and Data Classification Programstephen1004Nessuna valutazione finora
- 10-Cisa It Audit - BCP and DRPDocumento27 pagine10-Cisa It Audit - BCP and DRPHamza NaeemNessuna valutazione finora
- Cybersecurity Regulatory Framework (CRF) For The ICT Sector: Date: 29/05/2019 Classification: PublicDocumento52 pagineCybersecurity Regulatory Framework (CRF) For The ICT Sector: Date: 29/05/2019 Classification: PublicStrategic EschatologyNessuna valutazione finora
- Secure SDLC Consideration With NIST SP 800 64Documento27 pagineSecure SDLC Consideration With NIST SP 800 64JavvedNessuna valutazione finora
- 3rd Party Outsourcing Information Security Assessment Questionnaire V1.4Documento10 pagine3rd Party Outsourcing Information Security Assessment Questionnaire V1.4Ryan GlasgowNessuna valutazione finora
- Digital Risk Management A Complete Guide - 2019 EditionDa EverandDigital Risk Management A Complete Guide - 2019 EditionNessuna valutazione finora
- Disaster RecoveryDocumento6 pagineDisaster Recoverymav2u2Nessuna valutazione finora
- Module-6-Program Planning and DevelopmentDocumento79 pagineModule-6-Program Planning and DevelopmentUmair Amjad100% (1)
- 01 Security of Critical IT Infrastructure Full Report PDFDocumento34 pagine01 Security of Critical IT Infrastructure Full Report PDFmahadvikaNessuna valutazione finora
- Physical and Environmental Security Policy: Nformation Ecurity OlicyDocumento9 paginePhysical and Environmental Security Policy: Nformation Ecurity Olicypenumudi233Nessuna valutazione finora
- Cyber Security Strategy For GermanyDocumento20 pagineCyber Security Strategy For Germanycarumu01Nessuna valutazione finora
- IT Change Control Management Policy v3 - 201209280744175904Documento45 pagineIT Change Control Management Policy v3 - 201209280744175904Herik renaldo100% (3)
- ISMS Supplier Security PolicyDocumento4 pagineISMS Supplier Security PolicyAmine RachedNessuna valutazione finora
- Security and Data Governance Standard RequirementsDa EverandSecurity and Data Governance Standard RequirementsNessuna valutazione finora
- Connecticut Cyber Security StrategyDocumento39 pagineConnecticut Cyber Security StrategyHelen Bennett100% (2)
- PWC It Security Strategy and PlanningDocumento2 paginePWC It Security Strategy and Planningtracert100% (1)
- IT Risk Register IntroductionDocumento48 pagineIT Risk Register IntroductionjramkiNessuna valutazione finora
- 2012 Guidelines For Information SecurityDocumento1 pagina2012 Guidelines For Information SecurityDebanjan DeyNessuna valutazione finora
- Audit Programs - ICTDocumento15 pagineAudit Programs - ICTBenny NdossiNessuna valutazione finora
- WP2016 1-3 3 Study On Security Aspects of Virtualization PDFDocumento97 pagineWP2016 1-3 3 Study On Security Aspects of Virtualization PDFDeepthi Suresh100% (1)
- Getting-started-NIST (CSF) CyberSecurity FrameworkDocumento15 pagineGetting-started-NIST (CSF) CyberSecurity FrameworkJulius Malco100% (1)
- VPN Access Policy V 1.1Documento10 pagineVPN Access Policy V 1.1BirhanNessuna valutazione finora
- Database Security RoadmapDocumento1 paginaDatabase Security Roadmapwaz32195Nessuna valutazione finora
- ISM12 PatchAndVulnerabilityManagementPolicyDocumento4 pagineISM12 PatchAndVulnerabilityManagementPolicypenumudi233100% (1)
- Cybersecurity ISMS Policies And Procedures A Complete Guide - 2020 EditionDa EverandCybersecurity ISMS Policies And Procedures A Complete Guide - 2020 EditionNessuna valutazione finora
- Firewall Policy TemplateDocumento8 pagineFirewall Policy TemplateChristine MbinyaNessuna valutazione finora
- Information Security Architecture Standard RequirementsDa EverandInformation Security Architecture Standard RequirementsNessuna valutazione finora
- Info Handling PolicyDocumento4 pagineInfo Handling PolicybhwjNessuna valutazione finora
- Complete With Covers PDFDocumento226 pagineComplete With Covers PDFDanielFernandezMedinaNessuna valutazione finora
- Cybersecurity-Related Policies and Issuances: Developed by The Dod Deputy Cio For CybersecurityDocumento1 paginaCybersecurity-Related Policies and Issuances: Developed by The Dod Deputy Cio For CybersecurityVandoir GoncalvesNessuna valutazione finora
- Panagiotis C. Kalantzis, CISSP, CISM, ISO2700LA: Strategic Cybersecurity Leader & Executive ConsultantDocumento4 paginePanagiotis C. Kalantzis, CISSP, CISM, ISO2700LA: Strategic Cybersecurity Leader & Executive ConsultantPanos KalantzisNessuna valutazione finora
- ISO IEC 27002 2013 A Complete Guide - 2019 EditionDa EverandISO IEC 27002 2013 A Complete Guide - 2019 EditionNessuna valutazione finora
- ISO27k ISMS Gap Analysis and SoA - v1 - 02Documento47 pagineISO27k ISMS Gap Analysis and SoA - v1 - 02Christen Castillo100% (1)
- Network Security and ManagementDocumento4 pagineNetwork Security and Managementrashid1986Nessuna valutazione finora
- Perations Ecurity Olicy: Inspiring Business InnovationDocumento20 paginePerations Ecurity Olicy: Inspiring Business InnovationrontechtipsNessuna valutazione finora
- ISMS-105 - Bring Your Own Device Policy V2.0Documento7 pagineISMS-105 - Bring Your Own Device Policy V2.0O GoogleNessuna valutazione finora
- Iso27001 Gap Analysis Sam9779Documento5 pagineIso27001 Gap Analysis Sam9779Ahm HamzaNessuna valutazione finora
- Information Security Management ISO27001Documento16 pagineInformation Security Management ISO27001Johanna SmithNessuna valutazione finora
- Lidget Green Primary School and Children's Centre Acceptable Use PolicyDocumento4 pagineLidget Green Primary School and Children's Centre Acceptable Use Policybarbara.feather3403Nessuna valutazione finora
- Cyber Security PoliciesDocumento6 pagineCyber Security Policiesadeelshahzadqureshi8086100% (1)
- Security Vulnerability Threat Assessments A Complete Guide - 2019 EditionDa EverandSecurity Vulnerability Threat Assessments A Complete Guide - 2019 EditionNessuna valutazione finora
- B A Manifesto For Cyber Resilience PDFDocumento17 pagineB A Manifesto For Cyber Resilience PDFashokjpNessuna valutazione finora
- Clear Desk and Clear Screen PolicyDocumento4 pagineClear Desk and Clear Screen Policydhir.ankurNessuna valutazione finora
- Information Security Policy ChecklistDocumento2 pagineInformation Security Policy ChecklistRead Rule100% (6)
- Operational Procedures: I. T. PolicyDocumento50 pagineOperational Procedures: I. T. Policymc180204073 YUSRA REHMAT ELAHINessuna valutazione finora
- Certificate of Appreciation SampleDocumento1 paginaCertificate of Appreciation SampleGaurav AgarwalNessuna valutazione finora
- MyDLP Administration GuideDocumento84 pagineMyDLP Administration Guiderandom123vnNessuna valutazione finora
- Detailed Status Report TemplateDocumento1 paginaDetailed Status Report TemplateGaurav AgarwalNessuna valutazione finora
- OIM Quality Assurance Program CharterDocumento4 pagineOIM Quality Assurance Program CharterGaurav AgarwalNessuna valutazione finora
- Design Review ChecklistDocumento3 pagineDesign Review ChecklistGaurav AgarwalNessuna valutazione finora
- XIV. The Requirements Specification Document (RSD)Documento9 pagineXIV. The Requirements Specification Document (RSD)Gaurav AgarwalNessuna valutazione finora
- Sample Letter of TerminationDocumento1 paginaSample Letter of TerminationGaurav AgarwalNessuna valutazione finora
- UML Business ContextDocumento4 pagineUML Business ContextIRMTraining100% (2)
- CSRProjectClosureChecklist SampleDocumento4 pagineCSRProjectClosureChecklist SampleGaurav AgarwalNessuna valutazione finora
- Understanding ISO 22301 A Practical GuideDocumento1 paginaUnderstanding ISO 22301 A Practical GuideGaurav AgarwalNessuna valutazione finora
- Using Rational RoseDocumento19 pagineUsing Rational RosesolocheruicNessuna valutazione finora
- What Are The Different Approaches For Risk ToleranceDocumento20 pagineWhat Are The Different Approaches For Risk ToleranceGaurav AgarwalNessuna valutazione finora
- Trace Ability Sep 02Documento14 pagineTrace Ability Sep 02Gaurav AgarwalNessuna valutazione finora
- CabdriverDocumento1 paginaCabdriverGaurav AgarwalNessuna valutazione finora
- SharePoint2010 Permissions MatrixDocumento11 pagineSharePoint2010 Permissions MatrixGaurav AgarwalNessuna valutazione finora
- Employment Bring Your Own Device (BYOD)Documento4 pagineEmployment Bring Your Own Device (BYOD)Gaurav AgarwalNessuna valutazione finora
- Cyber Security Plan TemplateDocumento63 pagineCyber Security Plan TemplateGaurav Agarwal86% (7)
- J2Lite SRS TemplateDocumento7 pagineJ2Lite SRS Templatesami_20031Nessuna valutazione finora
- Simple Procurement GuideDocumento12 pagineSimple Procurement GuideGaurav AgarwalNessuna valutazione finora
- Bus Risk AnalDocumento8 pagineBus Risk AnalGaurav AgarwalNessuna valutazione finora
- This Document Is Classified For Public AccessDocumento1 paginaThis Document Is Classified For Public AccessGaurav AgarwalNessuna valutazione finora
- Data Security Model Enhancement in Cloud EnvironmentDocumento6 pagineData Security Model Enhancement in Cloud EnvironmentGaurav AgarwalNessuna valutazione finora
- NCERDC DataSecurityPlanExampleDocumento1 paginaNCERDC DataSecurityPlanExampleGaurav AgarwalNessuna valutazione finora
- MS ProjectExercise1Documento10 pagineMS ProjectExercise1inaam410Nessuna valutazione finora
- 15 Question SharePoint Risk AssessmentDocumento2 pagine15 Question SharePoint Risk AssessmentGaurav Agarwal0% (1)
- EmbassyofIndia 2MiscFormDocumento4 pagineEmbassyofIndia 2MiscFormGaurav AgarwalNessuna valutazione finora
- Agile Testing: A Practical Guide For Tes..Documento1 paginaAgile Testing: A Practical Guide For Tes..Gaurav AgarwalNessuna valutazione finora
- ReadmeDocumento5 pagineReadmeMatthew CaldwellNessuna valutazione finora
- B-Symc Ep Mob Ed DS - En-Usb-Symc Ep Mob Ed DS - En-UsDocumento2 pagineB-Symc Ep Mob Ed DS - En-Usb-Symc Ep Mob Ed DS - En-UsGaurav AgarwalNessuna valutazione finora
- Insurance 2012 - 2013Documento2 pagineInsurance 2012 - 2013Gaurav AgarwalNessuna valutazione finora
- UtilitarianismDocumento37 pagineUtilitarianismLeiya Lansang100% (2)
- Face Book: Khalid Hameed Students Galaxy: Khs Islamiyat Notes Series Chap 2 P2Documento9 pagineFace Book: Khalid Hameed Students Galaxy: Khs Islamiyat Notes Series Chap 2 P2areebsiddiqueNessuna valutazione finora
- Create An Informational Flyer AssignmentDocumento4 pagineCreate An Informational Flyer AssignmentALEEHA BUTTNessuna valutazione finora
- 01sample - Petition For Compulsory Recognition - rrp10182020Documento3 pagine01sample - Petition For Compulsory Recognition - rrp10182020Madam JudgerNessuna valutazione finora
- Medieval India 2022 1007Documento30 pagineMedieval India 2022 1007Kumar ShivrajNessuna valutazione finora
- 2017-18 Annual Report - California YMCA Youth & GovernmentDocumento16 pagine2017-18 Annual Report - California YMCA Youth & GovernmentRichard HsuNessuna valutazione finora
- 9-14-10 Captain Frank G Sabatino-To Receive His FirearmDocumento2 pagine9-14-10 Captain Frank G Sabatino-To Receive His FirearmEwing Township, NJNessuna valutazione finora
- PTS 30061020Documento54 paginePTS 30061020ronelbarafaeldiegoNessuna valutazione finora
- Bpats Enhancement Training ProgramDocumento1 paginaBpats Enhancement Training Programspms lugaitNessuna valutazione finora
- Color Run Entry FormDocumento1 paginaColor Run Entry Formapi-278815558Nessuna valutazione finora
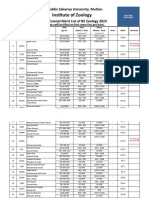
- 5953-6th Merit List BS Zool 31-8-2023Documento22 pagine5953-6th Merit List BS Zool 31-8-2023Muhammad AttiqNessuna valutazione finora
- Untitled DocumentDocumento16 pagineUntitled DocumentJolina CabardoNessuna valutazione finora
- Cases NOvember 21Documento31 pagineCases NOvember 21Wilfredo Guerrero IIINessuna valutazione finora
- Britmindogroupcompanyprofile PDFDocumento20 pagineBritmindogroupcompanyprofile PDFSatia Aji PamungkasNessuna valutazione finora
- Physical Education ProjectDocumento7 paginePhysical Education ProjectToshan KaushikNessuna valutazione finora
- Order RecieptDocumento1 paginaOrder RecieptAnUbHaV TiWaRiNessuna valutazione finora
- Security Administration GuideDocumento416 pagineSecurity Administration GuideCauã VinhasNessuna valutazione finora
- Government of IndiaDocumento13 pagineGovernment of Indiavikash_kumar_thakurNessuna valutazione finora
- JD 1-Moral Values: Kathrina Lana S. LanajaDocumento2 pagineJD 1-Moral Values: Kathrina Lana S. LanajaBrigitte YambaNessuna valutazione finora
- Auditing Theory Notes RA 9298Documento5 pagineAuditing Theory Notes RA 9298Honeylyne PlazaNessuna valutazione finora
- Polo Pantaleon V American ExpressDocumento10 paginePolo Pantaleon V American ExpressLyleThereseNessuna valutazione finora
- Grant, R - A Historical Introduction To The New TestamentDocumento11 pagineGrant, R - A Historical Introduction To The New TestamentPaulo d'OliveiraNessuna valutazione finora
- PAS 7 and PAS 41 SummaryDocumento5 paginePAS 7 and PAS 41 SummaryCharles BarcelaNessuna valutazione finora
- Opposition To Motion To DismissDocumento24 pagineOpposition To Motion To DismissAnonymous 7nOdcANessuna valutazione finora
- China Signposts: A Practical Guide For Multinationals in 2022Documento16 pagineChina Signposts: A Practical Guide For Multinationals in 2022APCO WorldwideNessuna valutazione finora
- DENTAL JURIS - Dental Legislation PDFDocumento2 pagineDENTAL JURIS - Dental Legislation PDFIsabelle TanNessuna valutazione finora
- Ideological Differences - Communism V CapitalismDocumento11 pagineIdeological Differences - Communism V CapitalismElvira ToktasinovaNessuna valutazione finora
- Squatting Problem and Its Social Ills in MANILADocumento10 pagineSquatting Problem and Its Social Ills in MANILARonstar Molina TanateNessuna valutazione finora
- 2017 IPCC Fall-Winter Newsletter IssueDocumento10 pagine2017 IPCC Fall-Winter Newsletter IssueaprotonNessuna valutazione finora
- Fundamentals of Drilling Operations: ContractsDocumento15 pagineFundamentals of Drilling Operations: ContractsSAKNessuna valutazione finora